(Felica/Mifare/NFC チャレンジシリーズ) その他の記事はこちら 「Felica/Mifare/NFC でいろいろ実験」
https://qiita.com/nanbuwks/items/1f416d6e45a87250ee0a
「RaspberryPi で NFC RFID-RC522 を Python3 で使う」
https://qiita.com/nanbuwks/items/c502ba880fbb93f522b3
では Python3 のライブラリを何種類かを試してみました。今回は、そのうちの、ondryaso / pi-rc522 をもう少し調べてみます。
ondryaso / pi-rc522
https://github.com/ondryaso/pi-rc522
MITライセンスです。
環境
- Raspbian Buster Lite
- Raspberry Pi 3 Model B Ver.2
- NFC RFID-RC522 格安モジュール
- pi-r522 2.2.1
- python 3.7.3
設定
配線については先の
「RaspberryPi で NFC RFID-RC522 を Python3 で使う」
https://qiita.com/nanbuwks/items/c502ba880fbb93f522b3
を参照。
インストールは先の記事では pip3 を使いましたが、それだと旧いものになるようだ。
不安定になる不具合が解消されているらしいので、新しいのが望ましい。
git から取得する。
pi@raspberrypi:~ $ git clone https://github.com/ondryaso/pi-rc522.git
Cloning into 'pi-rc522'...
remote: Enumerating objects: 260, done.
remote: Total 260 (delta 0), reused 0 (delta 0), pack-reused 260
Receiving objects: 100% (260/260), 56.47 KiB | 410.00 KiB/s, done.
Resolving deltas: 100% (135/135), done.
ここからインストールすると最新のものがインストールされるされるはずだが・・・
pi@raspberrypi:~ $ cd pi-rc522
pi@raspberrypi:~/pi-rc522 $ sudo python3 setup.py install
running install
running bdist_egg
running egg_info
.
.
.
Adding RPi.GPIO 0.7.0 to easy-install.pth file
Using /usr/local/lib/python3.7/dist-packages
Finished processing dependencies for pi-rc522==2.2.1
pi@raspberrypi:~/pi-rc522 $ python3
うーん、2.2.1がインストールされましたね。
pip3でインストールした版
Python 3.7.3 (default, Dec 20 2019, 18:57:59)
[GCC 8.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import pirc522
>>> pirc522.__version__
'2.2.1'
>>>
github からインストールした版
pi@raspberrypi:~ $ python3
Python 3.7.3 (default, Dec 20 2019, 18:57:59)
[GCC 8.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import pirc522
>>> pirc522.__version__
'2.2.1'
となってバージョン番号は同じだが diff を取ってみると結構違う。
2,22c2,3
<
< RASPBERRY = object()
< BEAGLEBONE = object()
< board = RASPBERRY
< try:
< # Try with Raspberry PI imports first
< import spidev
< import RPi.GPIO as GPIO
< SPIClass = spidev.SpiDev
< def_pin_rst = 22
< def_pin_irq = 18
< def_pin_mode = GPIO.BOARD
< except ImportError:
< # If they failed, try with Beaglebone
< import Adafruit_BBIO.SPI as SPI
< import Adafruit_BBIO.GPIO as GPIO
< SPIClass = SPI.SPI
< board = BEAGLEBONE
< def_pin_rst = "P9_23"
< def_pin_irq = "P9_15"
< def_pin_mode = None
---
> import spidev
> import RPi.GPIO as GPIO
56,69d36
< antenna_gain = 0x04
<
< #antenna_gain
< # defines the receiver's signal voltage gain factor:
< # 000 18 dB HEX = 0x00
< # 001 23 dB HEX = 0x01
< # 010 18 dB HEX = 0x02
< # 011 23 dB HEX = 0x03
< # 100 33 dB HEX = 0x04
< # 101 38 dB HEX = 0x05
< # 110 43 dB HEX = 0x06
< # 111 48 dB HEX = 0x07
< # 3 to 0 reserved - reserved for future use
<
73,74c40,41
< def __init__(self, bus=0, device=0, speed=1000000, pin_rst=def_pin_rst,
< pin_ce=0, pin_irq=def_pin_irq, pin_mode = def_pin_mode):
---
> def __init__(self, bus=0, device=0, speed=1000000, pin_rst=22,
> pin_ce=0, pin_irq=18, pin_mode=GPIO.BOARD):
79c46
< self.spi = SPIClass()
---
> self.spi = spidev.SpiDev()
81,85c48
< if board == RASPBERRY:
< self.spi.max_speed_hz = speed
< else:
< self.spi.mode = 0
< self.spi.msh = speed
---
> self.spi.max_speed_hz = speed
87,91c50,51
< if pin_mode is not None:
< GPIO.setmode(pin_mode)
< if pin_rst != 0:
< GPIO.setup(pin_rst, GPIO.OUT)
< GPIO.output(pin_rst, 1)
---
> GPIO.setmode(pin_mode)
> GPIO.setup(pin_rst, GPIO.OUT)
94a55
> GPIO.output(pin_rst, 1)
108d68
< self.dev_write(0x26, (self.antenna_gain<<4))
141,147d100
< def set_antenna_gain(self, gain):
< """
< Sets antenna gain from a value from 0 to 7.
< """
< if 0 <= gain <= 7:
< self.antenna_gain = gain
<
410,414d362
< self.init()
< #self.irq.clear()
< self.dev_write(0x04, 0x00)
< self.dev_write(0x02, 0xA0)
<
github からインストールしたもののほうが新しい。
安定化
github のものを使っても繰り返し処理をするとボードがハングしてしまったりしました。
対策として、手元に会った47μFの電解コンデンサを RFID-RC522 ボートの 3.3V と GND 間につないでみました。
この対策でかなり快調に!また、感度も大幅に改善しました。
カードの種類によっては RFID-RC522 ボードに密着しないと読み込みができなかったのも、3cm ぐらい離れても読み込みができるようになりました。
読んでみる
github の README にあるサンプルプログラムを元に、以下を作ってみました。
元々のプログラムは、セクタ10を読み込んで表示するものですが、引数にセクタを指定して読ませるようにしました。
import sys
from pirc522 import RFID
rdr = RFID()
sector = int(sys.argv[1])
print('target sector = : ', sector)
while True:
rdr.wait_for_tag()
(error, tag_type) = rdr.request()
if not error:
print("Tag detected")
(error, uid) = rdr.anticoll()
if not error:
print(" UID: " + str(uid))
# Select Tag is required before Auth
if not rdr.select_tag(uid):
print(" not rdr.select_tag")
# Auth for sector using default shipping key A
if not rdr.card_auth(rdr.auth_a, sector, [0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF], uid):
# This will print something like (False, [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0])
print(" Reading sector "+ str(sector) +" " + str(rdr.read(sector)))
# Always stop crypto1 when done working
rdr.stop_crypto()
# Calls GPIO cleanup
rdr.cleanup()
動かしてみました。
pi@raspberrypi:~ $ python3 ondryaso_read.py 10
/usr/local/lib/python3.7/dist-packages/pirc522/rfid.py:51: RuntimeWarning: This channel is already in use, continuing anyway. Use GPIO.setwarnings(False) to disable warnings.
GPIO.setup(pin_rst, GPIO.OUT)
target sector = : 10
Tag detected
Tag detected
Tag detected
Tag detected
Tag detected
Tag detected
Tag detected
Tag detected
E2
E2
E2
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Reading block 10 (False, [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0])
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
E2
Tag detected
UID: [242, 195, 43, 51, 41]
E2
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
E2
E2
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Reading block 10 (False, [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0])
書いてみる
の UtilExample.py を実行してみる。
本来はセクター9(セクタ2ブロック1)に
0x01, 0x23, 0x45, 0x67, 0x89, 0x98, 0x76, 0x54, 0x32, 0x10, 0x69, 0x27, 0x46, 0x66, 0x66, 0x64
を書き、更に上書きで
None, None, 0xAB, 0xCD, 0xEF
を書くプログラム。
pi@raspberrypi:~ $ python3 UtilExample.py
Detected
Detected
Card read UID: 242,193,107,51
Selecting UID [242, 193, 107, 51, 107]
Changing auth key and method to None
Changing used auth key to [255, 255, 255, 255, 255, 255] using method B
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B0: [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 255, 11, 12, 13, 14, 15]
Not calling card_auth - already authed
S1.0B0: [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 255, 11, 12, 13, 14, 15]
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Changing used auth key to [255, 255, 255, 255, 255, 255] using method A
Calling card_auth on UID [242, 193, 107, 51, 107]
Not calling card_auth - already authed
Changing pos 2 with current value 69 to 171
Changing pos 3 with current value 103 to 205
Changing pos 4 with current value 137 to 239
Writing [1, 35, 171, 205, 239, 152, 118, 84, 50, 16, 105, 39, 70, 102, 102, 100] to S2.0B1
Not calling card_auth - already authed
S2.0B1: [1, 35, 171, 205, 239, 152, 118, 84, 50, 16, 105, 39, 70, 102, 102, 100]
Calling card_auth on UID [242, 193, 107, 51, 107]
S0.0B0: [242, 193, 107, 51, 107, 8, 4, 0, 98, 99, 100, 101, 102, 103, 104, 105]
Calling card_auth on UID [242, 193, 107, 51, 107]
S0.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S0.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S0.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B0: [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 255, 11, 12, 13, 14, 15]
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S1.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S2.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S2.0B1: [1, 35, 171, 205, 239, 152, 118, 84, 50, 16, 105, 39, 70, 102, 102, 100]
Calling card_auth on UID [242, 193, 107, 51, 107]
S2.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S2.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S3.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S3.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S3.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S3.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S4.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S4.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S4.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S4.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S5.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S5.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S5.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S5.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 192, 125, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S6.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S6.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S6.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S6.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S7.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S7.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S7.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S7.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S8.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S8.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S8.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S8.0B3: [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Calling card_auth on UID [242, 193, 107, 51, 107]
S9.0B0: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S9.0B1: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
S9.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Calling card_auth on UID [242, 193, 107, 51, 107]
E2
Error on S9.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
E2
Error on S10.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S10.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S10.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S10.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S11.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S11.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S11.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S11.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S12.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S12.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S12.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S12.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S13.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S13.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S13.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S13.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S14.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S14.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S14.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S14.0B3
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S15.0B0
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S15.0B1
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S15.0B2
Calling card_auth on UID [242, 193, 107, 51, 107]
Error on S15.0B3
Changing auth key and method to None
Stopping crypto1
となりました。
読み込みができて、書き込みが終わって、確認の読み込みのあとダンプがなされます。
そのダンプは S9.0B2: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0] まではOKですが、
それから後はエラーが起こってますね。
何回か試したら、エラー発生箇所は不定ですがダンプがいずれも途中で失敗します。
しかしながらそれ以前の読み込み、書き込み、確認の読み込みは正常になっていそうです。
ちなみに、電解コンデンサをつなげずに行ったときは以下のように結構なエラーが発生していました。
Detected
Card read UID: 242,195,43,51
Selecting UID [242, 195, 43, 51, 41]
Changing used auth key to [255, 255, 255, 255, 255, 255] using method B
Calling card_auth on UID [242, 195, 43, 51, 41]
E2
Error on S1.0B0
Not calling card_auth - already authed
S1.0B0: [2]
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S1.0B2
Changing used auth key to [255, 255, 255, 255, 255, 255] using method A
Calling card_auth on UID [242, 195, 43, 51, 41]
Not calling card_auth - already authed
Not calling card_auth - already authed
S2.0B1: []
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S0.0B0
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S0.0B1
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S0.0B2
.
.
.
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S15.0B2
Calling card_auth on UID [242, 195, 43, 51, 41]
Error on S15.0B3
Changing auth key and method to None
Keyを使ったアクセス
とあるカードではセクタ4が特定のキーが無いと読めないようになっていました。
pi@raspberrypi:~ $ python3 ondryaso_read.py 4
/usr/local/lib/python3.7/dist-packages/pirc522/rfid.py:51: RuntimeWarning: This channel is already in use, continuing anyway. Use GPIO.setwarnings(False) to disable warnings.
GPIO.setup(pin_rst, GPIO.OUT)
target sector = : 4
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Tag detected
UID: [242, 195, 43, 51, 41]
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Tag detected
E2
Tag detected
E2
Tag detected
E2
キーも読み込みNGとなっています。
該当のブロックのアクセスビットは 0x787788となってました。
MyFare のデータシートぽいものとして、 MF1S50YYX_V1 MIFARE Classic EV1 1K - Mainstream contactless smart card IC for fast and easy solution development Rev. 3.2 — 23 May 2018
https://www.nxp.com/docs/en/data-sheet/MF1S50YYX_V1.pdf
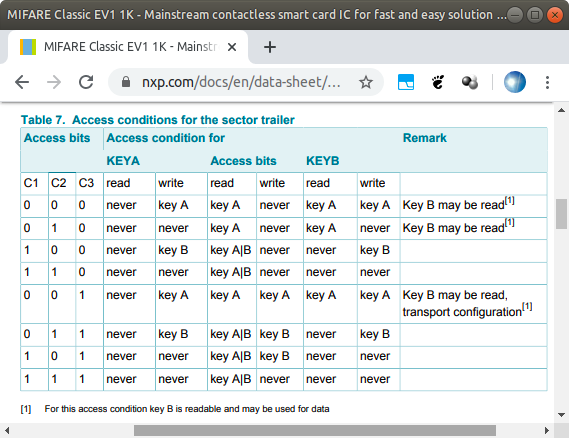
8.7.1 Access conditions によると、以下のようになります。
- C10 = 1
- C20 = 0
- C30 = 0
- C11 = 1
- C21 = 0
- C31 = 0
- C12 = 1
- C22 = 0
- C32 = 0
- C13 = 0
- C23 = 1
- C33 = 1
これの意味するものは以下のようになります
- 該当ブロックセクタ0に対するアクセス権
- C10 = 1
- C20 = 0
- C30 = 0
- キーA,キーBで読み込み可能、キーBで書き込み可能
- 該当ブロックセクタートレーラに対するアクセス権
- C13 = 0
- C23 = 1
- C33 = 1
- アクセスビットの書き込みは KeyB のみで可能、KeyA は KeyB で書き込み可能、KeyB は KeyA で読み込み可能、読み込みはアクセスビットだけ KeyA,B で可能
Key を使った読み込み
ということで、カードリーダー側で予め用意したキー値を指定してリードするようにします。仮に KeyA が 0x0F, 0xF0, 0x0F, 0xF0, 0x0F, 0xF0 となっていた場合、先の読み込みプログラムを以下のように書き換えます。
if not rdr.card_auth(rdr.auth_a, sector, [0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF], uid):
↓
if not rdr.card_auth(rdr.auth_a, sector, [0x0F, 0xF0, 0x0F, 0xF0, 0x0F, 0xF0], uid):
実行してみます
pi@raspberrypi:~ $ python3 ondryaso_read_with_key.py 4
/usr/local/lib/python3.7/dist-packages/pirc522/rfid.py:51: RuntimeWarning: This channel is already in use, continuing anyway. Use GPIO.setwarnings(False) to disable warnings.
GPIO.setup(pin_rst, GPIO.OUT)
target sector = : 4
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Reading sector 4 (False, [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 0, 0, 0, 0, 0, 0])
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Reading sector 4 (False, [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 0, 0, 0, 0, 0, 0])
Tag detected
UID: [242, 195, 43, 51, 41]
not rdr.select_tag
Reading sector 4 (True, [51,48,1])
Tag detected
うまく読めました
Keyを使った書き込み
https://github.com/ondryaso/pi-rc522/blob/master/examples/KeyChange.py
を元にして、以下のように作りました
#!/usr/bin/env python3
import signal
import time
import sys
# from rfid import RFID
from pirc522 import RFID
sector = int(sys.argv[1])
print('target sector : ', sector)
s = sys.argv[2]
writedata=[]
li = [writedata.append(int(i+j,16)) for (i,j) in zip(s[::2],s[1::2])]
run = True
rdr = RFID()
util = rdr.util()
util.debug = False
keyab=rdr.auth_b
key =[0xA1,0xA2,0xA3,0xA4,0xA5,0xA6]
def end_read(signal,frame):
global run
print("\nCtrl+C captured, ending read.")
run = False
print("\ncleanuping...")
rdr.cleanup()
print("\ncleanup end")
exit()
signal.signal(signal.SIGINT, end_read)
print("Starting")
while run:
rdr.wait_for_tag()
(error, data) = rdr.request()
if not error:
time.sleep(0.1)
print("\nDetected: " + format(data, "02X"))
(error, uid) = rdr.anticoll()
if not error:
time.sleep(0.1)
print("Card read UID: "+str(uid[0])+","+str(uid[1])+","+str(uid[2])+","+str(uid[3]))
print("Setting tag")
util.set_tag(uid)
time.sleep(0.1)
print("\nAuthorizing")
util.auth(keyab, key)
time.sleep(0.1)
print("\nWriting modified bytes")
util.rewrite(sector, writedata)
time.sleep(0.1)
print("\nReading")
(error, data) = rdr.read(sector)
print(util.sector_string(sector) + ": " + str([format(data[i],'02x') for i in range(len(writedata))]))
count = 0
diffflag = 0
if ( len(writedata) <= len(data)):
for x in writedata:
if ( writedata[count] != data[count] ):
diffflag = 1
count = count + 1
if ( 0 == diffflag ):
print(" verify ok ")
exit()
time.sleep(0.1)
うまくできました。
pi@raspberrypi:~ $ python3 Write.py 4 4D1F
target sector : 4
Starting
Detected: 10
Card read UID: 242,195,43,51,41
Setting tag
Authorizing
Writing modified bytes
Reading
S1.0B0: ['4d', '1f']
verify ok