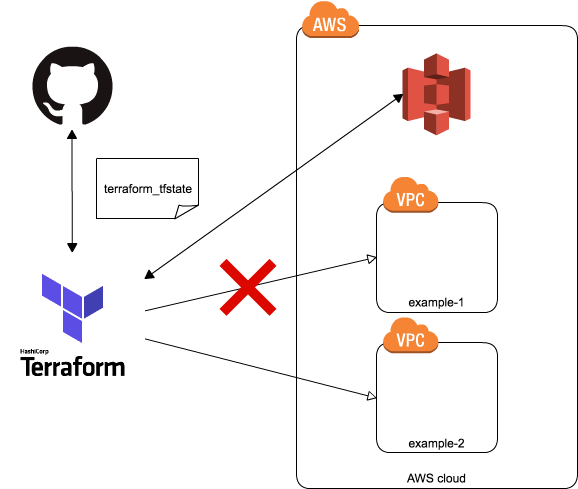
目的
- 特定のVPCで起動させるEC2にタグ指定が必要なIAMポリシーを作成し、他VPCにあるリソースに影響が及ばないようにする
- 他VPCやインスタンスを表示するなどの権限は付ける
イメージ
設定
iam_role.tf
resource "aws_iam_role" "<role-name>" {
name = "<role-name>"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Effect": "Allow",
"Sid": ""
}
]
}
EOF
}
iam_instance_profile.tf
resource "aws_iam_instance_profile" "<profile-name>" {
name = "<profile-name>"
role = "${aws_iam_role.<role-name>.name}"
}
- タグを指定しないと起動しない設定にする
- key=Name,value=user-name
iam_policy.tf
resource "aws_iam_policy" "example-policy" {
name = "example-policy"
path = "/"
description = "example vpc only"
policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "not support resource",
"Effect": "Allow",
"Action": [
"iam:GetInstanceProfile",
"iam:ListInstanceProfiles",
"ec2:Describe*",
"ec2:*Tags",
"ec2:Get*",
"ec2:*KeyPair",
"ec2:AllocateAddress",
"ec2:AssociateAddress",
"ec2:AttachNetworkInterface",
"ec2:AttachVolume",
"ec2:CancelSpotInstanceRequests",
"ec2:CopyImage",
"ec2:CopySnapshot",
"ec2:CreateImage",
"ec2:CreateSnapshot",
"ec2:CreateVolume",
"ec2:CreateSecurityGroup",
"ec2:DeleteSecurityGroup",
"ec2:DeleteSnapshot",
"ec2:DeleteVolume",
"ec2:DetachNetworkInterface",
"ec2:DetachVolume",
"ec2:DisassociateAddress",
"ec2:EnableVolumeIO",
"ec2:ModifyImageAttribute",
"ec2:ModifyInstanceAttribute",
"ec2:ModifyNetworkInterfaceAttribute",
"ec2:ModifySnapshotAttribute",
"ec2:ModifyVolumeAttribute",
"ec2:MonitorInstances",
"ec2:ReleaseAddress",
"ec2:ReportInstanceStatus",
"ec2:RequestSpotInstances",
"ec2:RequestSpotFleet",
"ec2:AuthorizeSecurityGroupEgress",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupEgress",
"ec2:RevokeSecurityGroupIngress",
"ec2:UnmonitorInstances"
],
"Resource": "*"
},
{
"Sid": "PassRole",
"Action": [
"iam:PassRole"
],
"Effect": "Allow",
"Resource": "arn:aws:iam::<account-id>:role/<role-name>"
},
{
"Sid": "AllowInstanceActions",
"Effect": "Allow",
"Action": [
"ec2:RunInstances",
"ec2:RebootInstances",
"ec2:StopInstances",
"ec2:TerminateInstances",
"ec2:StartInstances",
"ec2:AttachVolume",
"ec2:DetachVolume"
],
"Resource": "arn:aws:ec2:<region>:<account-id>:instance/*",
"Condition": {
"StringEquals": {
"ec2:InstanceProfile": "arn:aws:iam::<account-id>:instance-profile/<profile-name>"
}
}
},
{
"Sid": "RunInstances",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:<region>:<account-id>:instance/*",
"Condition": {
"StringEquals": {
"ec2:InstanceProfile": "arn:aws:iam::<account-id>:instance-profile/<profile-name>"
}
}
},
{
"Sid": "LaunchInstanceInSubnet",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:<region>:<account-id>:subnet/*",
"Condition": {
"StringEquals": {
"ec2:Vpc": "arn:aws:ec2:<region>:<account-id>:vpc/<vpc-id>"
}
}
},
{
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": [
"arn:aws:ec2:<region>::image/*",
"arn:aws:ec2:<region>:<account-id>:instance/*",
"arn:aws:ec2:<region>:<account-id>:volume/*",
"arn:aws:ec2:<region>:<account-id>:network-interface/*",
"arn:aws:ec2:<region>:<account-id>:key-pair/*",
"arn:aws:ec2:<region>:<account-id>:security-group/*"
]
},
{
"Effect": "Allow",
"Action": [
"ec2:TerminateInstances",
"ec2:StopInstances",
"ec2:StartInstances",
"ec2:RebootInstances"
],
"Resource": [
"arn:aws:ec2:<region>:<account-id>:instance/*"
],
"Condition": {
"StringEquals": {
"ec2:ResourceTag/User": "<user-name>"
}
}
}
]
}
EOF
}
所感
- 嵌った箇所
-
ec2:vpc条件キーをStartInstanceやRunInstancesに指定していたが、実はサポートされていなかった。RunInstances に関するリソースレベルのアクセス許可
-
{
"Sid":"EC2RunInstances",
"Effect":"Allow",
"Action":"ec2:RunInstances",
"Resource":[
"arn:aws:ec2:<region>::image/*",
"arn:aws:ec2:<region>::snapshot/*",
"arn:aws:iam::<account-id>:instance-profile/*",
"arn:aws:ec2:<region>:<account-id>:volume/*",
"arn:aws:ec2:<region>:<account-id>:security-group/*"
],
"Condition":{
"StringEquals":{
"ec2:Vpc":"arn:aws:ec2:<region>:<account-id>:vpc/<vpc-id>"
}
}
}
- サブネットのVPCを限定とする記述に変更
{
"Sid": "LaunchInstanceInSubnet",
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:<region>:<account-id>:subnet/*",
"Condition": {
"StringEquals": {
"ec2:Vpc": "arn:aws:ec2:<region>:<account-id>:vpc/<vpc-id>"
}
}
},