LDAPログインについて
*ほぼUbuntu Serverの公式ドキュメントからのコピペです。自分用に書き換えただけ。
本記事の説明はLDAPの基本設定やユーザ名「john」の追加をUbuntu公式ドキュメントに従って設定した後に、LDAPサーバとLDAPクライアントを連携させる作業のメモです。まずは公式ドキュメントに従ってjohnまで作ってから読んでください。
イメージ画像
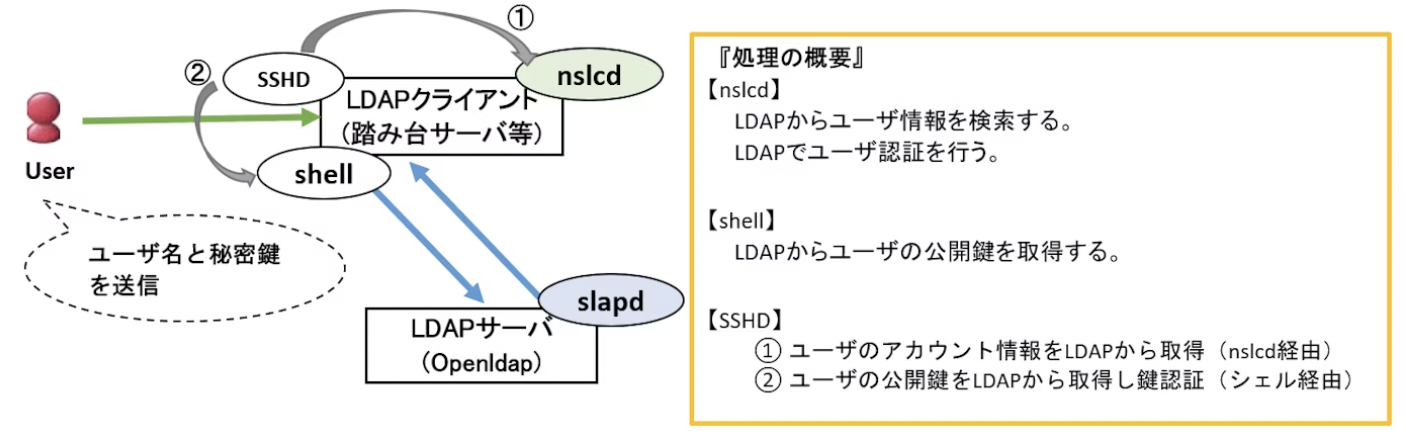
(引用:https://qiita.com/y-araki-qiita/items/0c954c3ae25d4ed9dbb8)
サーバ側設定(FQDN: node1.example.com)
自己証明書の作成
Install the gnutls-bin and ssl-cert packages:
sudo apt install gnutls-bin ssl-cert
Create a private key for the Certificate Authority:
sudo certtool --generate-privkey --bits 4096 --outfile /etc/ssl/private/mycakey.pem
Create the template/file /etc/ssl/ca.info to define the CA:
cn = Example Company
ca
cert_signing_key
expiration_days = 3650
Create the self-signed CA certificate:
sudo certtool --generate-self-signed \
--load-privkey /etc/ssl/private/mycakey.pem \
--template /etc/ssl/ca.info \
--outfile /usr/local/share/ca-certificates/mycacert.crt
sudo update-ca-certificates
各クライアントへ送信
scp /usr/local/share/ca-certificates/mycacert.crt kodai4@node4:~/
LDAPサービスの証明書作成
Make a private key for the server:
sudo certtool --generate-privkey \
--bits 2048 \
--outfile /etc/ldap/node1_slapd_key.pem
Create the /etc/ssl/node1.info info file containing:
organization = Example Company
cn = node1.example.com
tls_www_server
encryption_key
signing_key
expiration_days = 365
Create the server’s certificate:
sudo certtool --generate-certificate \
--load-privkey /etc/ldap/node1_slapd_key.pem \
--load-ca-certificate /etc/ssl/certs/mycacert.pem \
--load-ca-privkey /etc/ssl/private/mycakey.pem \
--template /etc/ssl/node1.info \
--outfile /etc/ldap/node1_slapd_cert.pem
Adjust permissions and ownership:
sudo chgrp openldap /etc/ldap/node1_slapd_key.pem
sudo chmod 0640 /etc/ldap/node1_slapd_key.pem
Create the file certinfo.ldif with the following contents (adjust paths and filenames accordingly):
dn: cn=config
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ssl/certs/mycacert.pem
-
add: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ldap/node1_slapd_cert.pem
-
add: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ldap/node1_slapd_key.pem
Use the ldapmodify command to tell slapd about our TLS work via the slapd-config database:
sudo ldapmodify -Y EXTERNAL -H ldapi:/// -f certinfo.ldif
If you need access to LDAPS (LDAP over SSL), then you need to edit /etc/default/slapd and include ldaps:/// in SLAPD_SERVICES like below:
SLAPD_SERVICES="ldap:/// ldapi:/// ldaps:///"
And restart slapd with:
sudo systemctl restart slapd
クライアント側の設定
証明書の設定
sudo chown root:root mycacert.crt
sudo mv mycacert.crt /usr/local/share/ca-certificates/
sudo update-ca-certificates
sssdをldapと連携
sudo apt install sssd-ldap ldap-utils
Create the /etc/sssd/sssd.conf configuration file, with permissions 0600 and ownership root:root, and add the following content:
[sssd]
config_file_version = 2
domains = example.com
[domain/example.com]
id_provider = ldap
auth_provider = ldap
ldap_uri = ldap://node1.example.com
cache_credentials = True
ldap_search_base = dc=example,dc=com
Make sure to start the sssd service:
sudo chmod 600 /etc/sssd/sssd.conf
sudo chown root:root /etc/sssd/sssd.conf
sudo systemctl restart sssd.service
To enable automatic home directory creation, run the following command:
sudo pam-auth-update --enable mkhomedir
ここまででパスワード認証を用いたSSHログインをユーザ名johnで行えるようになった。
気を付けるべきこと
sudo certtool --generate-certificate \
--load-privkey /etc/ldap/ldap01_slapd_key.pem \
--load-ca-certificate /etc/ssl/certs/mycacert.pem \
--load-ca-privkey /etc/ssl/private/mycakey.pem \
--template /etc/ssl/ldap01.info \
--outfile /etc/ldap/ldap01_slapd_cert.pem
で使用される/etc/ssl/ldap01.infoの内容が以下
organization = Example Company
cn = ldap01.example.com
tls_www_server
encryption_key
signing_key
expiration_days = 365
ここでcnはホスト名を指定する。
この時ホスト名はDNSサーバに登録している必要がある
SSH公開鍵の共有
スキーマの追加
https://openssh-ldap-pubkey.readthedocs.io/en/latest/openldap.html
$ vim openssh-lpk.ldif
-----------------
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 f6bf57a2
dn: cn=openssh-lpk,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: openssh-lpk
olcAttributeTypes: {0}( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME 'sshPublicKey' DES
C 'MANDATORY: OpenSSH Public key' EQUALITY octetStringMatch SYNTAX 1.3.6.1.4.
1.1466.115.121.1.40 )
olcObjectClasses: {0}( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME 'ldapPublicKey' DESC
'MANDATORY: OpenSSH LPK objectclass' SUP top AUXILIARY MAY ( sshPublicKey $
uid ) )
-------------------
sudo ldapadd -H ldapi:/// -Y EXTERNAL -f openssh-lpk.ldif
公開鍵をLDIFで追加
https://teratail.com/questions/283183
dn: uid=john,ou=People,dc=example,dc=com
changetype: modify
add: objectClass
objectClass: ldapPublicKey
-
add: sshPublicKey
sshPublicKey: ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKqFDgQXi2ndSdZJhLIhr85TeT9dAUc85EShTGGVm0HZ john@node1
sudo ldapmodify -D cn=admin,dc=example,dc=com -W -H ldapi:/// -f add_sshpubkey.ldif
sudo ldapadd -H ldapi:/// -Y EXTERNAL -f openssh-lpk.ldif
クライアント側のSSSDとsshdの設定変更
https://qiita.com/s5601026/items/8c5f16a2935ccd7fb305
$ sudo vim /etc/ssh/sshd_config
-------------------
PubkeyAuthentication yes
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys
AuthorizedKeysCommandUser root
--------------------
sudo systemctl restart sshd