概要
TryHackMe「XSS」ルームのwalkthroughです。
Task2
Q1.Which XSS vulnerability relies on saving the malicious script?
A.Stored XSS
Q2.Which prevalent XSS vulnerability executes within the browser session without being saved?
A.Reflected XSS
Q3.What does DOM stand for?
A.Document Object Model
Task3
Q1.Based on the leading causes of XSS vulnerabilities, what operations should be performed on the user input?
A.validation and sanitization
Q2.To prevent XSS vulnerabilities, what operations should be performed on the data before it is output to the user?
A.encoding
Task4
Q1.Which one of the following characters do you expect to be encoded? ., ,, ;, &, or #?
A.&
Q2.Which one of the following characters do you expect to be encoded? +, -, *, <, =, or ^?
A.<
Q3.Which function can we use in JavaScript to replace (unsafe) special characters with HTML entities?
A.escapeHtml()
Q4.Which function did we use in PHP to replace HTML special characters?
A.htmlspecialchars
Task5
Start Machineをクリックしマシンを起動後、openvpnを起動し接続します。
copypartyの脆弱性CVE-2023-38501を利用してマシンを攻略します。
- copyparty
- CVE
- Exploit DB
Q1.What type of vulnerability is it?
Exploit DBのDescriptionにはこう書かれています。
Copyparty is a portable file server. Versions prior to 1.8.6 are subject to a reflected cross-site scripting (XSS) Attack.
引用:Exploit DB:copyparty v1.8.6 - Reflected Cross Site Scripting (XSS)
A.reflected xss
Q2.Use the above exploit against the attached VM. What do you see on the second line after go to?
対象マシンの3923ポートへブラウザで接続するとホーム画面が表示されます。
URLに下記exploitを使用して実行します。
- URLエンコード前
?k304=y <img src=copyparty onerror=alert(1)>
- URLエンコード後
?k304=y%0D%0A%0D%0A%3Cimg+src%3Dcopyparty+onerror%3Dalert(1)%3E
実行後、アラートとパスが表示されました。
表示された/h#ccへアクセスすると管理者画面が表示されました。
A./?h#cc
Task6
Q1.What is the name of the JavaScript function we used to sanitize the user input before saving it?
A.sanitizeHTML()
Q2.Which method did we call in ASP.Net C# to sanitize user input?
A.HttpUtility.HtmlEncode()
Task7
対象のマシンではHospital Management Systemが動作しています。
このプログラムにはcontact.phpを介した蓄積型XSSの脆弱性があり、CVE-2021-38757として採番されています。
- ソースコード
- CVE-2021-38757
- PoC
- 脆弱なコード
フォームから入力された情報がサニタイズされずにMySQLに保存されていることが確認できます。
<?php
$con=mysqli_connect("localhost","root","","myhmsdb");
if(isset($_POST['btnSubmit']))
{
$name = $_POST['txtName'];
$email = $_POST['txtEmail'];
$contact = $_POST['txtPhone'];
$message = $_POST['txtMsg'];
$query="insert into contact(name,email,contact,message) values('$name','$email','$contact','$message');";
$result = mysqli_query($con,$query);
Q1.What type of vulnerability is it?
A.stored xss
Q2.Go to the contact page and submit the following message <script>alert(document.cookie)</script>. Next, log in as the Receptionist. What is the name of the key from the displayed key-value pair?
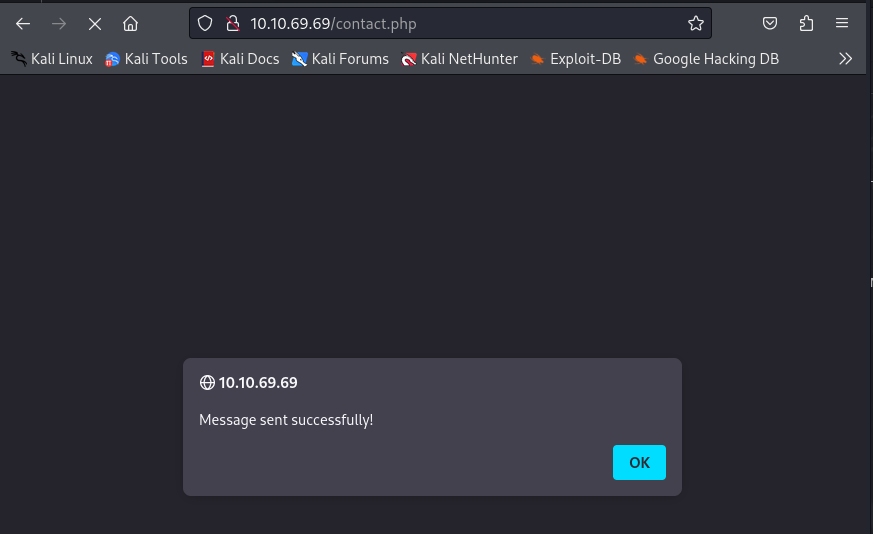
ブラウザからコンタクトページにアクセスします。
メッセージ枠に任意のJavaScriptコードを入力し、実行することができます。
<script>alert(document.cookie)</script>を入力し送信します。
Receptionist画面からUsername: admin,Password: admin123の資格情報を使ってログインすると、先ほどのスクリプトが実行されCookie情報を見られました。
A.PHPSESSID
Task8
Q1.DOM-based XSS is reflected via the server. (Yea/Nay)
A.Nay
Q2.DOM-based XSS happens only on the client side. (Yea/Nay)
A.Yea
Q3.Which JavaScript method was used to escape the user input?
A.encodeURIComponent()
Task9
Q1.Which character does 	 represent?
	はASCIIコードで水平タブを表しています。
A.TAB
Task10
Q1.This room used a fictional static site to demonstrate one of the XSS vulnerabilities. Which XSS type was that?
A.DOM-based XSS