ドハマりかと思った。。
いくつか英語サイト探して情報組み合わせて修正してようやく動作。
1.まずAzure Portalでアプリを登録

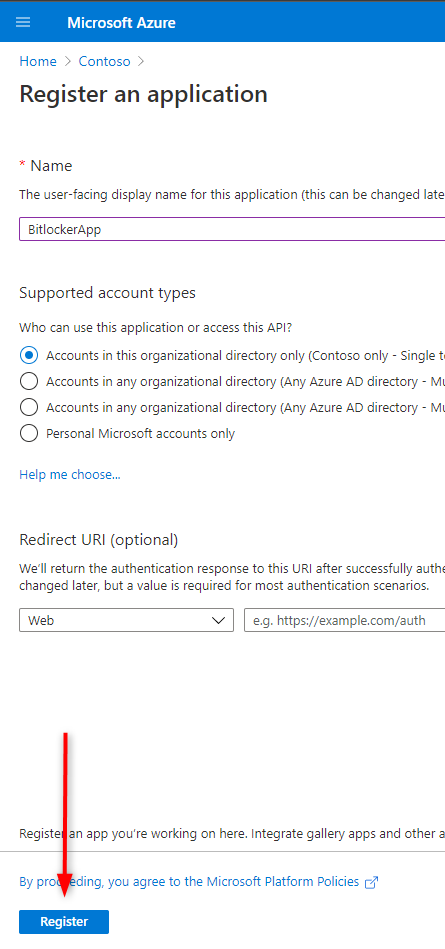
2.アクセス権を設定
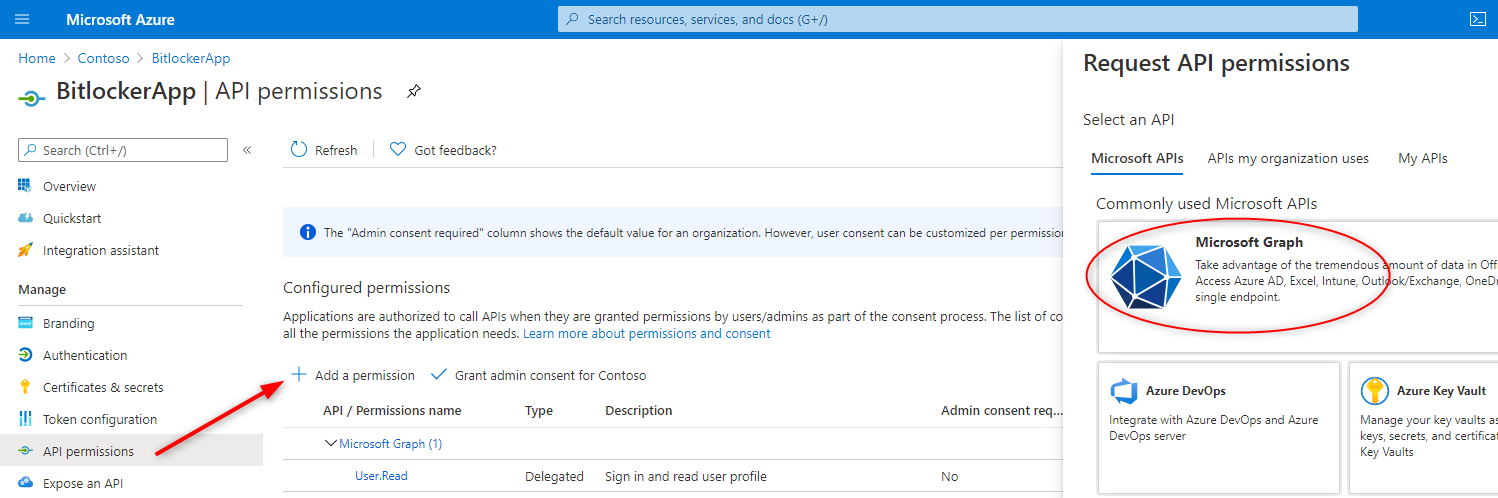

3.管理者の承認

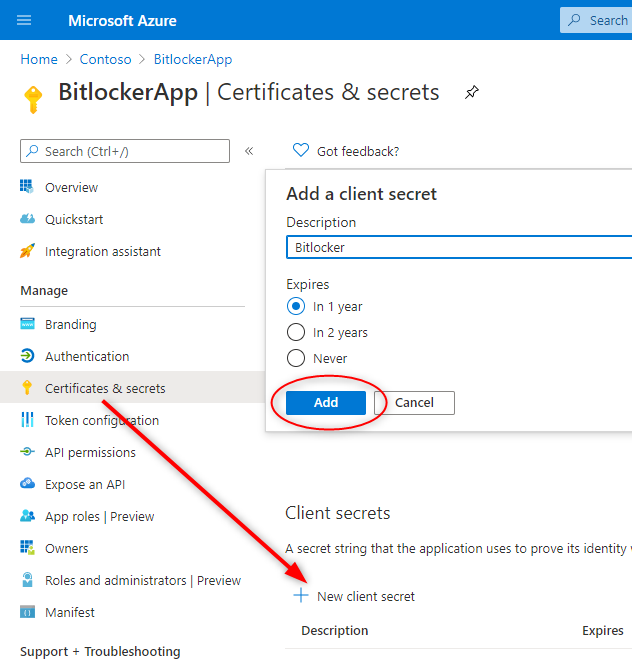
4.シークレットを作成
5.おソース
$AccountName = "username@onmicrosoft.com"
$AccountPassword = "XXXXXXXXXXXXX"
$ClientId = "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX"
$ClientSecret = "XXXXXXXXXXXXXXXXXXXXXX"
$TenantID = "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX"
$GraphUri = "https://graph.microsoft.com"
$GraphVersion = "beta"
Add-Type -AssemblyName System.Web
$ClientSecret = [System.Web.HttpUtility]::UrlEncode($ClientSecret)
# Authentication url
$AzureResourceURI = "https://login.microsoftonline.com/$TenantID/oauth2/v2.0/token"
# Construct the Body for the POST
$Body = "grant_type=password"`
+ "&username=" + $Accountname `
+ "&client_id=" + $ClientId `
+ "&client_secret=" + $ClientSecret`
+ "&password=" + $AccountPassword `
+ "&scope=https://graph.microsoft.com/.default"
# The result should contain a token for use with Graph
$Response = Invoke-WebRequest -Uri $AzureResourceURI -Method POST -Body $Body -UseBasicParsing
$ResponseJSON = $Response | ConvertFrom-Json
# Add the token to headers for the Graph request
$Headers = @{
Authorization = "Bearer " + $ResponseJSON.access_token
}
# Run API call
$Deviceuri = "$GraphUri/$GraphVersion/devices"
$AllDevices = Invoke-RestMethod -Uri $Deviceuri -Headers $Headers -Method Get
$Body = @{
grant_type = "password"
scope = "https://graph.microsoft.com/.default"
client_id = "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX"
client_secret = "XXXXXXXXXXXXXXXXXXXXXX"
username = "username@onmicrosoft.com"
password = "XXXXXXXXXXXXX"
}
$ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantID
/oauth2/v2.0/token" -Method POST -Body $Body
$token = $ConnectGraph.access_token
$headr = @{
Authorization = "Bearer $($token)"
'ocp-client-name' = "My Friendly Client"
'ocp-client-version' = "1.2"
}
$GrapGroupUrl = 'https://graph.microsoft.com/beta/bitlocker/recoveryKeys'
$bitlockerkeys = @()
$bitlockerkeysuri = Invoke-RestMethod -Headers $headr -Uri $GrapGroupUrl -Method Get
$bitlockerkeys += $bitlockerkeysuri.value
while ($bitlockerkeysuri.'@odata.nextLink') {
$NextBatchRequest = $bitlockerkeysuri.'@odata.nextLink'
$bitlockerkeysuri = Invoke-RestMethod -Uri $NextBatchRequest -Headers $headr -Method Get
$bitlockerkeys += $bitlockerkeysuri.value
}
# Get all AAD devices and filter out Windows managed by Intune
$AllDevicesArr = @()
$Deviceuri = "$GraphUri/$GraphVersion/devices?`$filter=operatingSystem eq 'Windows' AND isManaged eq true AND accountEnabled eq true"
$Devices = Invoke-RestMethod -Uri $Deviceuri -Headers $Headers -Method Get
$AllDevicesArr += $Devices.value
while ($Devices.'@odata.nextLink') {
$NextBatchRequest = $Devices.'@odata.nextLink'
$Devices = Invoke-RestMethod -Uri $NextBatchRequest -Headers $Headers -Method Get
$AllDevicesArr += $Devices.value
}
$Devices2 = $AllDevicesArr | Where-Object {$PSItem.managementType -eq 'MDM'}
# For every managed device check if there is a recovery key in AAD
$Results = @()
try {
foreach ($device in $Devices2) {
if (($bitlockerkeys | Where-Object { $PSItem.deviceId -eq $device.deviceId } | Measure-Object).Count -gt 0) {
$Results += [PSCustomObject]@{
DeviceName = $device.displayName
DeviceId = $device.deviceId
RecoveryKeyInAAD = $true
AdditionalInfo = "$(($bitlockerkeys | Where-Object { $PSItem.deviceId -eq $device.deviceId } | Measure-Object).Count) keys found"
}
} else {
$Results += [PSCustomObject]@{
DeviceName = $device.displayName
DeviceId = $device.deviceId
RecoveryKeyInAAD = $false
AdditionalInfo = ''
}
}
}
} catch {
Write-Error $device
Write-Error $_
break
}
$filename = Get-Date -Format "yyyy-MMdd-HHmmss"
[string]$csvFile = "BitLockerRecoverKeysExists_" + $filename + ".csv"
[string]$csvPath = Join-Path "C:\Temp" $csvFile
$Results | select DeviceName,DeviceId,RecoveryKeyInAAD,AdditionalInfo | Export-Csv -Path $csvPath -Encoding UTF8 -NoTypeInformation
invoke-item $csvPath
■ネタ元
Verify Azure AD Bitlocker Keys with Microsoft Graph - Maciej Horbacz
https://universecitiz3n.tech/powershell/Graph-Bitlocker/
azure active directory - "Failed to authorize caller, the caller wasn't owner of the device or one of the admin roles." microsoft-graph - Stack Overflow
https://stackoverflow.com/questions/64905676/failed-to-authorize-caller-the-caller-wasnt-owner-of-the-device-or-one-of-the
Intune – Query Azure AD Bitlocker Keys using Graph API – Azure Cloud & AI Domain Blog
https://azurecloudai.blog/2020/11/24/intune-query-azure-ad-bitlocker-keys-using-graph-api/