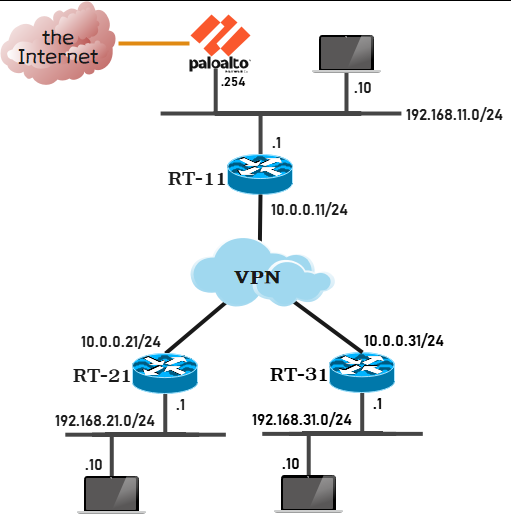
構成
- インターネットへの出口は画像上の Palo Alto (NGFW:次世代ファイヤーウォール) から出ていく
- 各拠点が固定 IP を持っている
- ikev2 で接続する
- DMVPN ではなく、拠点間の通信は RT-11 (HUB) を経由する
機器
EVE-NG 上で実行。
- Cisco router : isrv-17.03.03 (Cisco IOS XE Software, Version 17.03.03)
- 端末 : debian 12.9
- PA-VM : PAN-OS 11.1.4-h7
設定
共通部分
ホスト名、ログ、時刻を設定 (不要なものは削除)
共通
hostname RT-11
ip domain name my.home
no ip domain lookup
clock timezone JST 9
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
no service config
no ip http server
no ip http authentication local
no ip http secure-server
no ip http client source-interface GigabitEthernet1
no ip tftp source-interface GigabitEthernet1
ntp server 192.168.0.252
結線確認用
仮想環境なので、接続が間違えていないことを確認できるようにしておく。
共通
cdp run
lldp run
ssh ログインの設定
パスワードは適宜変更してください
共通
ip ssh version 2
username admin privilege 9 secret Cisco123
enable secret Cisco123
line vty 0 4
login local
transport input ssh
ライセンスのメッセージがうるさいのでダミー
共通
service call-home
license boot level ax
license smart url http://127.0.0.1/
license smart transport smart
インターフェース、ルーティングの設定 RT-11―RT-21 間
RT-11
RT-11
hostname RT-11
int Gi1
desc /// LAN - Internet
no ip dhcp client client-id
ip address 10.0.0.11 255.255.255.0
no shut
!
int Gi3
desc /// VPN
no ip dhcp client client-id
ip address 192.168.11.1 255.255.255.0
no shut
!
ip route 0.0.0.0 0.0.0.0 192.168.11.254
RT-21
VPN の設定が入っていないのでルーティングはまだ
RT-21
int Gi1
desc /// LAN
no ip dhcp client client-id
ip address 10.0.0.21 255.255.255.0
no shut
!
int Gi3
desc /// VPN
no ip dhcp client client-id
ip address 192.168.21.1 255.255.255.0
no shut
VPN設定 RT-11―RT-21 間
RT-11 側
RT-11
! プロポーサル
! aes-gcm-xx を使うときは DH group は定義しない
crypto ikev2 proposal ike2-prop1
encryption aes-cbc-256
integrity SHA512 sha384
group 24 21 19 14
!
! ポリシー
crypto ikev2 policy ike2-pol1
match fvrf any
proposal ike2-prop1
!
! キーリング
crypto ikev2 keyring RT11-RT21
peer RT21
address 10.0.0.21
pre-shared-key RT11-RT21
!
!
! プロファイル
crypto ikev2 profile prof-RT21
match fvrf any
match identity remote address 10.0.0.21 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local RT11-RT21
lifetime 1800
dpd 30 6 on-demand
!
!
crypto ipsec transform-set trans esp-sha384-hmac esp-256-aes
!
crypto ipsec profile ipsec-RT21
set transform-set trans
set pfs group24
set ikev2-profile prof-RT21
interface Tunnel2
desc to RT-21
ip unnumbered Gi3
tunnel source 10.0.0.11
tunnel mode ipsec ipv4
tunnel destination 10.0.0.21
tunnel protection ipsec profile ipsec-RT21
!
ip route 192.168.21.0 255.255.255.0 Tunnel2
RT-21 側
RT-21
! プロポーサル
! aes-gcm-xx を使うときは DH group は定義しない
crypto ikev2 proposal ike2-prop1
encryption aes-cbc-256
integrity SHA512 sha384
group 24 21 19 14
!
! ポリシー
crypto ikev2 policy ike2-pol1
match fvrf any
proposal ike2-prop1
!
! キーリング
crypto ikev2 keyring RT21-RT11
peer RT11
address 10.0.0.11
pre-shared-key RT11-RT21
!
!
! プロファイル
crypto ikev2 profile prof-RT11
match fvrf any
match identity remote address 10.0.0.11 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local RT21-RT11
lifetime 1800
dpd 30 6 on-demand
!
!
crypto ipsec transform-set trans esp-sha384-hmac esp-256-aes
!
crypto ipsec profile ipsec-RT11
set transform-set trans
set pfs group24
set ikev2-profile prof-RT11
interface Tunnel1
desc to RT-11
ip unnumbered Gi3
tunnel source 10.0.0.21
tunnel mode ipsec ipv4
tunnel destination 10.0.0.11
tunnel protection ipsec profile ipsec-RT11
!
ip route 0.0.0.0 0.0.0.0 Tunnel1
状態を確認
RT-11
RT-11
RT-11#show crypto session
Crypto session current status
Interface: Tunnel2
Profile: prof-RT21
Session status: UP-ACTIVE
Peer: 10.0.0.21 port 500
Session ID: 36
IKEv2 SA: local 10.0.0.11/500 remote 10.0.0.21/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
RT-11#
RT-11#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
3 10.0.0.11/500 10.0.0.21/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA384, Hash: SHA384, DH Grp:24, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 1800/1595 sec
IPv6 Crypto IKEv2 SA
RT-11#
RT-11#show crypto ipsec sa
interface: Tunnel2
Crypto map tag: Tunnel2-head-0, local addr 10.0.0.11
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 10.0.0.21 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 53, #pkts encrypt: 53, #pkts digest: 53
#pkts decaps: 53, #pkts decrypt: 53, #pkts verify: 53
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.0.0.11, remote crypto endpt.: 10.0.0.21
plaintext mtu 1422, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x5A51C743(1515308867)
PFS (Y/N): Y, DH group: group24
inbound esp sas:
spi: 0xC9F18F00(3388051200)
transform: esp-256-aes esp-sha384-hmac ,
in use settings ={Tunnel, }
conn id: 2056, flow_id: CSR:56, sibling_flags FFFFFFFF80000048, crypto map: Tunnel2-head-0
sa timing: remaining key lifetime (k/sec): (4608000/3495)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x5A51C743(1515308867)
transform: esp-256-aes esp-sha384-hmac ,
in use settings ={Tunnel, }
conn id: 2055, flow_id: CSR:55, sibling_flags FFFFFFFF80000048, crypto map: Tunnel2-head-0
sa timing: remaining key lifetime (k/sec): (4608000/3495)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
RT-11#
RT-21
RT-21
RT-21#show crypto session
Crypto session current status
Interface: Tunnel1
Profile: prof-RT11
Session status: UP-ACTIVE
Peer: 10.0.0.11 port 500
Session ID: 2
IKEv2 SA: local 10.0.0.21/500 remote 10.0.0.11/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
RT-21#
RT-21#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
3 10.0.0.21/500 10.0.0.11/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA384, Hash: SHA384, DH Grp:24, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 1800/68 sec
IPv6 Crypto IKEv2 SA
RT-21#
RT-21#show crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 10.0.0.21
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 10.0.0.11 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.0.0.21, remote crypto endpt.: 10.0.0.11
plaintext mtu 1422, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xC9F18F00(3388051200)
PFS (Y/N): Y, DH group: group24
inbound esp sas:
spi: 0x5A51C743(1515308867)
transform: esp-256-aes esp-sha384-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: CSR:5, sibling_flags FFFFFFFF80000048, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4607999/3312)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC9F18F00(3388051200)
transform: esp-256-aes esp-sha384-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: CSR:6, sibling_flags FFFFFFFF80000048, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4607999/3312)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
RT-21#
疎通確認
RT-21
RT-21#ping 192.168.11.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.11.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/7/22 ms
RT-21#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 5/5/6 ms
RT-21#
RT-11
RT-11#ping 192.168.21.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.21.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
RT-11#
RT-11―RT-31
RT-31の初期設定
int Gi1
no ip dhcp client client-id
ip address 10.0.0.31 255.255.255.0
no shut
!
int Gi3
no ip dhcp client client-id
ip address 192.168.31.1 255.255.255.0
no shut
RT-11
RT-11
crypto ikev2 keyring RT11-RT31
peer RT31
address 10.0.0.31
pre-shared-key RT11-RT31
!
!
! プロファイル
crypto ikev2 profile prof-RT31
match fvrf any
match identity remote address 10.0.0.31 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local RT11-RT31
lifetime 1800
dpd 30 6 on-demand
!
crypto ipsec profile ipsec-RT31
set transform-set trans
set pfs group24
set ikev2-profile prof-RT31
interface Tunnel3
desc to RT-31
ip unnumbered Gi3
tunnel source 10.0.0.11
tunnel mode ipsec ipv4
tunnel destination 10.0.0.31
tunnel protection ipsec profile ipsec-RT31
ip route 192.168.31.0 255.255.255.0 Tunnel3
RT-31
RT-31
! プロポーサル
! aes-gcm-xx を使うときは DH group は定義しない
crypto ikev2 proposal ike2-prop1
encryption aes-cbc-256
integrity SHA512 sha384
group 24 21 19 14
!
! ポリシー
crypto ikev2 policy ike2-pol1
match fvrf any
proposal ike2-prop1
!
! キーリング
crypto ikev2 keyring RT31-RT11
peer RT11
address 10.0.0.11
pre-shared-key RT11-RT31
!
!
! プロファイル
crypto ikev2 profile prof-RT11
match fvrf any
match identity remote address 10.0.0.11 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local RT31-RT11
lifetime 1800
dpd 30 6 on-demand
!
!
crypto ipsec transform-set trans esp-sha384-hmac esp-256-aes
!
crypto ipsec profile ipsec-RT11
set transform-set trans
set pfs group24
set ikev2-profile prof-RT11
interface Tunnel1
desc to RT-11
ip unnumbered Gi3
tunnel source 10.0.0.31
tunnel mode ipsec ipv4
tunnel destination 10.0.0.11
tunnel protection ipsec profile ipsec-RT11
!
ip route 0.0.0.0 0.0.0.0 Tunnel1
RT-11 から
RT-11#ping 192.168.21.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.21.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
RT-11#ping 192.168.31.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.31.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
RT-31 から
RT-31#ping 192.168.11.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.11.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/4 ms
RT-31#ping 192.168.21.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.21.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
RT-31#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/7 ms
RT-31#
かきかけ...