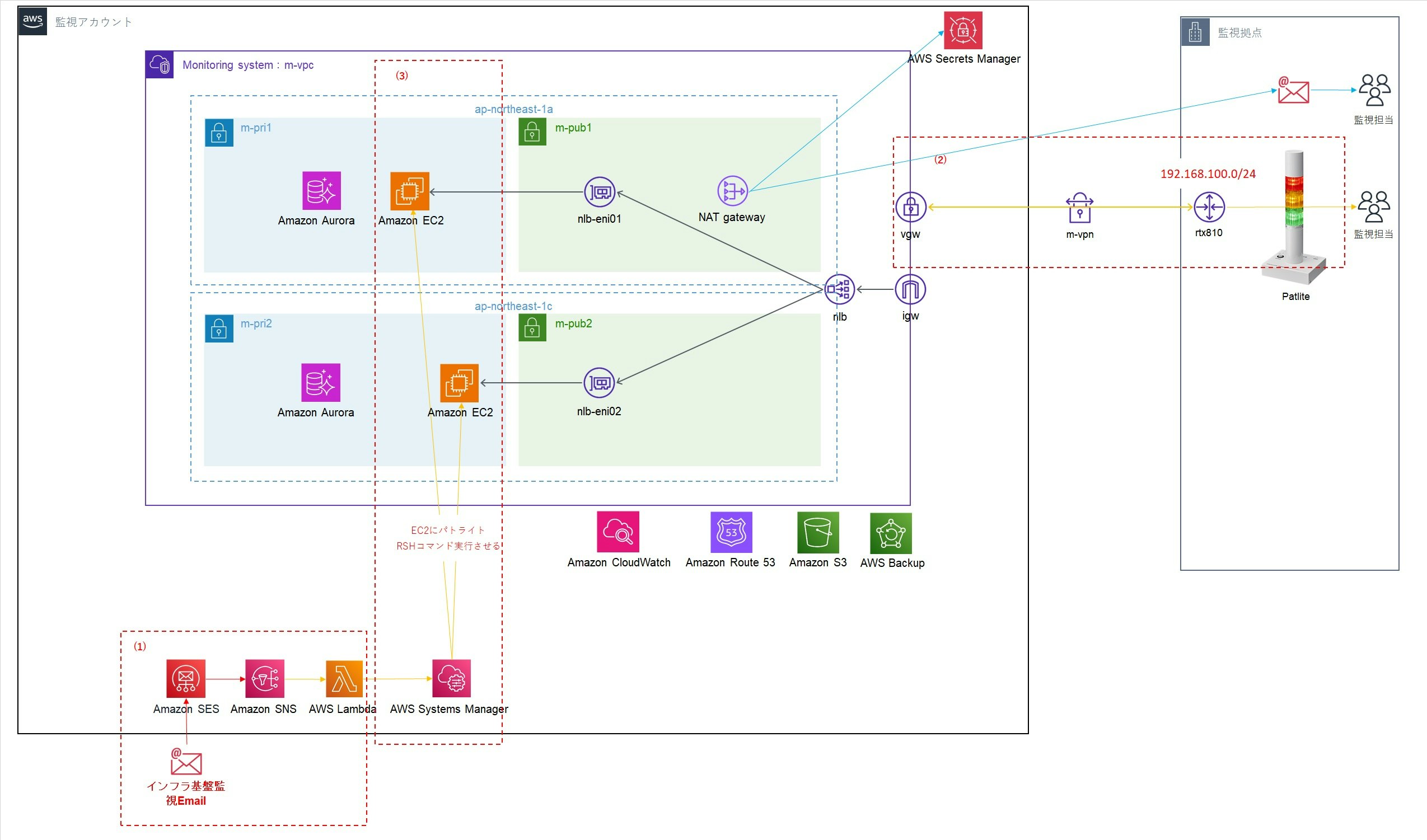
当社は、流通業向けのシステムに対して、監視サービスをお客様に提供しています。近年、サービスを利用されるお客様の増加に伴い、監視メールは毎日数千件ほどが来ています。監視サービスの品質を向上させるため、AWSクラウド上の監視サーバー(EC2)からの通知手段はメールのみならず、パトライトを点灯したり鳴らしたりする仕組みも導入いたしました。その環境の構築方法について、こちらで解説いたします。
当社で直面した課題
- 毎日数千件の監視メールが来ている状況で、その中で監視NGのメールが来ているのにもかかわらず、担当者の見落としにより、適切な対応ができないことで、お客様の業務に大きく影響を与えてしまう
- 各監視メールに対して障害検知内容によって重要度に分けておらず、どの障害メールを優先対応すべきか担当者は迷っている
導入の成果
- パトライトを点灯したり、鳴らしたりする仕組みの導入によって、業務へのインパクトが大きいメールを受信したら、パトライトを点灯したり、鳴らしたりすることで、担当者に対して注意喚起を行い、速やかに対応措置が取れることで、お客様の業務への影響を軽減
- 事前に定めた障害内容分類によってパトライトの点灯をすることで、人為的な対応優先度の判断ミスを回避
主な導入サービス
- AWS Systems Manager
- Amazon Simple Email Service (SES)
- Amazon Simple Notification Service (Amazon SNS)
- AWS Lambda
- AWS Site-to-Site VPN
インフラ構成図
設計、構築のポイント
1. 障害メール受信部分
障害メールをAmazon SESは受信し、受信完了をトリガーにしてAmazon SNSにイベント送信をし、AWS Lambdaを起動しています。SES受信において独自ドメインを使っていますので、独自ドメインの取得がまだの場合、先に独自ドメインを取得し、Route 53にホストゾーンを設定しておく必要です。
また、SESから直接Lambdaにイベントを送信することができますが、SNSを経由した場合のみ、通知にはメール本文(content)が含まれますので、SNSを経由することにしました。
SESの設定
事前にドメイン認証済み(お名前.comでCNAME設定しています)
SNSの設定
Lambda関数をサブスクリプションしている必要
2. パトライトと通信のためのSite-to-Site VPN構築部分
パトライトは、ローカルに置いているので、EC2と通信するためには、Site-to-Site VPNの構築が必要になります。
Site-to-Site VPN関連設定
VGW、CGWの作成
VPCルート追加(192.168.100.0/24へのトラフィックは、VGW経由)
EC2のセキュリティグループ変更(192.168.100.0/24から許可)
は、行っておいてください。
YAMAHA Router(RTX810) Config設定内容
ローカルに置いたヤマハルーターのConfig設定が必要です。
# RTX810 Rev.11.01.19 (Mon Jul 29 15:27:26 2013)
# MAC Address : 00:a0:de:ab:4a:a0, 00:a0:de:ab:4a:a1
# Memory 128Mbytes, 2LAN
# main: RTX810 ver=00 serial=S3K084888 MAC-Address=00:a0:de:ab:4a:a0 MAC-Address=00:a0:de:ab:4a:a1
# Reporting Date: May 21 15:56:27 2024
ip route default gateway pp 1 filter 500000 gateway pp 1
ip route 10.1.8.0/24 gateway tunnel 1 hide gateway tunnel 2 hide
ip lan1 address 192.168.100.1/24
provider type isdn-terminal
provider filter routing connection
provider lan1 name LAN:
provider lan2 name PPPoE/0/1/5/0/0/0:
pp select 1
pp name PRV/1/1/5/0/0/0:
pp keepalive interval 30 retry-interval=30 count=12
pp always-on on
pppoe use lan2
pppoe auto disconnect off
pp auth accept pap chap
pp auth myname ********** *
ppp lcp mru on 1454
ppp ipcp ipaddress on
ppp ipcp msext on
ppp ccp type none
ip pp address 202.213.149.180/32
ip pp secure filter in 200003 200020 200021 200022 200023 200024 200025 200030 200032 200080 200081
ip pp secure filter out 200013 200020 200021 200022 200023 200024 200025 200026 200027 200099 dynamic 200080 200081 200082 200083 200084 200085 200098 200099
ip pp nat descriptor 1000
pp enable 1
provider set 1
provider dns server pp 1 1
provider select 1
tunnel select 1
ipsec tunnel 201
ipsec sa policy 201 1 esp aes-cbc sha-hmac
ipsec ike duration ipsec-sa 1 3600
ipsec ike encryption 1 aes-cbc
ipsec ike group 1 modp1024
ipsec ike hash 1 sha
ipsec ike keepalive log 1 off
ipsec ike keepalive use 1 on heartbeat 10 3
ipsec ike local address 1 192.168.100.1
ipsec ike local id 1 192.168.100.0/24
ipsec ike pfs 1 on
ipsec ike pre-shared-key 1 *
ipsec ike remote address 1 3.113.138.62
ipsec ike remote id 1 10.1.8.0/24
ipsec tunnel outer df-bit clear
ip tunnel address 169.254.247.102/30
ip tunnel remote address 169.254.247.101
ip tunnel tcp mss limit auto
tunnel enable 1
tunnel select 2
ipsec tunnel 202
ipsec sa policy 202 2 esp aes-cbc sha-hmac
ipsec ike duration ipsec-sa 2 3600
ipsec ike encryption 2 aes-cbc
ipsec ike group 2 modp1024
ipsec ike hash 2 sha
ipsec ike keepalive use 2 on dpd 10 3
ipsec ike local address 2 192.168.100.1
ipsec ike local id 2 192.168.100.0/24
ipsec ike pfs 2 on
ipsec ike pre-shared-key 2 *
ipsec ike remote address 2 3.114.147.40
ipsec ike remote id 2 10.1.8.0/24
ipsec tunnel outer df-bit clear
ip tunnel address 169.254.215.42/30
ip tunnel remote address 169.254.215.41
ip tunnel tcp mss limit 1379
tunnel enable 2
ip filter 200000 reject 10.0.0.0/8 * * * *
ip filter 200001 reject 172.16.0.0/12 * * * *
ip filter 200002 reject 192.168.0.0/16 * * * *
ip filter 200003 reject 192.168.100.0/24 * * * *
ip filter 200010 reject * 10.0.0.0/8 * * *
ip filter 200011 reject * 172.16.0.0/12 * * *
ip filter 200012 reject * 192.168.0.0/16 * * *
ip filter 200013 reject * 192.168.100.0/24 * * *
ip filter 200020 reject * * udp,tcp 135 *
ip filter 200021 reject * * udp,tcp * 135
ip filter 200022 reject * * udp,tcp netbios_ns-netbios_ssn *
ip filter 200023 reject * * udp,tcp * netbios_ns-netbios_ssn
ip filter 200024 reject * * udp,tcp 445 *
ip filter 200025 reject * * udp,tcp * 445
ip filter 200026 restrict * * tcpfin * www,21,nntp
ip filter 200027 restrict * * tcprst * www,21,nntp
ip filter 200030 pass * 192.168.100.0/24 icmp * *
ip filter 200031 pass * 192.168.100.0/24 established * *
ip filter 200032 pass * 192.168.100.0/24 tcp * ident
ip filter 200033 pass * 192.168.100.0/24 tcp ftpdata *
ip filter 200034 pass * 192.168.100.0/24 tcp,udp * domain
ip filter 200035 pass * 192.168.100.0/24 udp domain *
ip filter 200036 pass * 192.168.100.0/24 udp * ntp
ip filter 200037 pass * 192.168.100.0/24 udp ntp *
ip filter 200080 pass * 192.168.100.1 udp * 500
ip filter 200081 pass * 192.168.100.1 esp * *
ip filter 200098 reject-nolog * * established
ip filter 200099 pass * * * * *
ip filter 500000 restrict * * * * *
ip filter dynamic 200080 * * ftp
ip filter dynamic 200081 * * domain
ip filter dynamic 200082 * * www
ip filter dynamic 200083 * * smtp
ip filter dynamic 200084 * * pop3
ip filter dynamic 200085 * * submission
ip filter dynamic 200098 * * tcp
ip filter dynamic 200099 * * udp
nat descriptor type 1000 masquerade
nat descriptor masquerade static 1000 1 192.168.100.1 udp 500
nat descriptor masquerade static 1000 2 192.168.100.1 esp
ipsec auto refresh on
dhcp service server
dhcp server rfc2131 compliant except remain-silent
dhcp scope 1 192.168.100.2-192.168.100.191/24
dns server pp 1
dns server select 500001 pp 1 any . restrict pp 1
dns private address spoof on