vRXの構築(L2TP/IPsecを用いたリモートアクセス)についての続きです。
AWS側の設定 はL2TP/IPsecを用いたリモートアクセスと大体同じですが、vRXの設定のみを記載しておきます。
■設定方法(拠点⇔AWS間のIPSec接続)
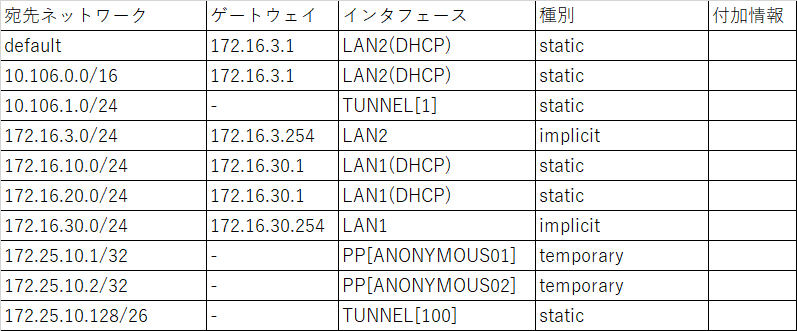
10.106.1.0/24は拠点IPセグメントであり、vRX内部でルーティングし、それ以外はdefaultへルーティングするような設計となります。
qiita.rb
# VRXのConfigファイル
vrx user *
ip route default gateway dhcp lan2
ip route 10.106.0.0/16 gateway dhcp lan2
ip route 10.106.1.0/24 gateway tunnel 1
ip route 172.16.10.0/24 gateway dhcp lan1
ip route 172.16.20.0/24 gateway dhcp lan1
ip route 172.25.10.128/26 gateway tunnel 100
ip filter source-route on
ip filter directed-broadcast on
description lan1 IP_172.16.30.254
ip lan1 address dhcp
ip lan1 proxyarp on
description lan2 IP_172.16.3.254_EIP_35.78.31.89
ip lan2 address dhcp
ip lan2 nat descriptor 1
pp select anonymous
pp bind tunnel81-tunnel95
pp auth request mschap-v2
pp auth username vpnuser01 *
pp auth username vpnuser02 *
pp auth username vpnuser03 *
pp auth username vpnuser04 *
pp auth username vpnuser05 *
pp auth username vpnuser06 *
pp auth username vpnuser07 *
pp auth username vpnuser08 *
pp auth username vpnuser09 *
pp auth username vpnuser10 *
pp auth username vpnuser11 *
pp auth username vpnuser12 *
pp auth username vpnuser13 *
pp auth username vpnuser14 *
pp auth username vpnuser15 *
ppp ipcp ipaddress on
ppp ipcp msext on
ip pp remote address pool 172.25.10.1-172.25.10.15
ip pp mtu 1258
pp enable anonymous
tunnel select 1
ipsec tunnel 101
ipsec sa policy 101 1 esp aes256-cbc sha256-hmac
ipsec ike encryption 1 aes256-cbc
ipsec ike group 1 modp1536
ipsec ike hash 1 sha256
ipsec ike keepalive log 1 off
ipsec ike keepalive use 1 on icmp-echo 10.106.1.1 30 5
ipsec ike local address 1 172.16.30.254
ipsec ike nat-traversal 1 on
ipsec ike pre-shared-key 1 *
ipsec ike remote address 1 any
ipsec ike remote name 1 hashidrug-shop001 key-id
ip tunnel tcp mss limit auto
tunnel enable 1
ip filter 3100 pass-log * *
nat descriptor type 1 masquerade
nat descriptor address outer 1 primary
nat descriptor masquerade static 1 1 172.16.30.254 udp 500
nat descriptor masquerade static 1 2 172.16.30.254 udp 4500
nat descriptor masquerade static 1 3 172.16.30.254 tcp 22
nat descriptor type 3 nat
nat descriptor address outer 3 192.168.200.77
nat descriptor address inner 3 172.16.30.5
nat descriptor static 3 1 192.168.200.77=172.16.30.5 1
ipsec auto refresh on
ipsec transport 81 81 udp 1701
ipsec transport 82 82 udp 1701
ipsec transport 83 83 udp 1701
ipsec transport 84 84 udp 1701
ipsec transport 85 85 udp 1701
ipsec transport 86 86 udp 1701
ipsec transport 87 87 udp 1701
ipsec transport 88 88 udp 1701
ipsec transport 89 89 udp 1701
ipsec transport 90 90 udp 1701
ipsec transport 91 91 udp 1701
ipsec transport 92 92 udp 1701
ipsec transport 93 93 udp 1701
ipsec transport 94 94 udp 1701
ipsec transport 95 95 udp 1701
syslog notice on
syslog info on
syslog debug off
tftp host any
telnetd service on
telnetd host any
dns server dhcp lan2
l2tp service on
sshd service on
sshd host key generate *
■ip route
■まとめ
上記の通り設定いただければ、通信可能と思います。これでvRXの構築の2パターンの設定方法の説明は完了となります。