ebtablesでのIPレイヤのフィルタリング+ログ
「いまさらだけどebtables(その1)」の続き。ebtablesにて、IPレイヤのフィルタリングおよびログを実施。
ネットワーク構成およびNetwork Bridge設定
前回と同じ。

$ sudo brctl addbr br0
$ sudo brctl addif br0 enp0s3
$ sudo brctl addif br0 enp0s9
$ sudo brctl addif br0 enp0s10
$ sudo ip link set up dev br0
$ sudo brctl show
bridge name bridge id STP enabled interfaces
br0 8000.08002703353c no enp0s10
enp0s3
enp0s9
$ ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br0 state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:03:35:3c brd ff:ff:ff:ff:ff:ff
3: enp0s9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br0 state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:7f:54:7d brd ff:ff:ff:ff:ff:ff
4: enp0s10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br0 state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:29:53:04 brd ff:ff:ff:ff:ff:ff
5: br0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:03:35:3c brd ff:ff:ff:ff:ff:ff
検証
特定IPアドレスを送信元とするIPパケットをDrop(破棄)
設定
「-p ipv4」および「--ip-src 192.168.10.22」により、特定送信元IPアドレスのIPパケットを破棄。
$ sudo ebtables -A FORWARD -p ipv4 --ip-src 192.168.10.22 -j DROP
$ sudo ebtables -L
Bridge table: filter
Bridge chain: INPUT, entries: 0, policy: ACCEPT
Bridge chain: FORWARD, entries: 1, policy: ACCEPT
-p IPv4 --ip-src 192.168.10.22 -j DROP
Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
結果
VM:192.168.10.22でのpingの結果である。
$ ping 192.168.10.33 -c 1
PING 192.168.10.33 (192.168.10.33) 56(84) bytes of data.
--- 192.168.10.33 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
特定宛先ポートをもつIPパケットをDrop
設定
「-p ipv4」、「--ip-protocol tcp」、「--ip-destination-port 1234」により、特定宛先ポートを持つIPパケットを破棄。
$ sudo ebtables -A FORWARD -p ipv4 --ip-protocol tcp --ip-destination-port 1234 -j DROP
$ sudo ebtables -L
Bridge table: filter
Bridge chain: INPUT, entries: 0, policy: ACCEPT
Bridge chain: FORWARD, entries: 1, policy: ACCEPT
-p IPv4 --ip-proto tcp --ip-dport 1234 -j DROP
Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
VM:192.168.10.44(Server)のポート1234で待受(Listen)。
#### 結果
$ nc -l -p 1234
VM:192.168.10.11(Client)で、Serverにポート1234でアクセスできず。
$ echo test | nc 192.168.10.44 1234
(UNKNOWN) [192.168.10.44] 1234 (?) : Connection timed out
このときのServerの様子。ARPのやり取りはあるが、その続き(TCP)がない。
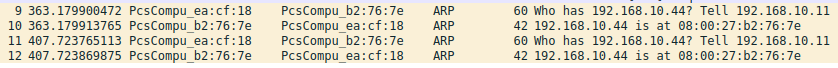
特定宛先IPアドレスを持つIPパケットをDropかつログ化
設定
VM:192.168.10.44宛のIPパケットを破棄し、「--log-ip --log-prefix "[ebtables Drop]"」により、syslogにログ。
$ sudo ebtables -A FORWARD -p ipv4 --ip-destination 192.168.10.44 -j DROP --log-ip --log-prefix "[ebtables Drop]"
$ sudo ebtables -L
Bridge table: filter
Bridge chain: INPUT, entries: 0, policy: ACCEPT
Bridge chain: FORWARD, entries: 1, policy: ACCEPT
-p IPv4 --ip-dst 192.168.10.44 --log-level notice --log-prefix "[ebtables Drop]" --log-ip -j DROP
Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
VM:192.168.10.11でのping。
$ ping 192.168.10.44 -c 1
PING 192.168.10.44 (192.168.10.44) 56(84) bytes of data.
--- 192.168.10.44 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
結果
下記ログ。
$ tail /var/log/syslog
...
Jun 4 20:48:40 vamos kernel: [45219.165499] [ebtables Drop] IN=enp0s3 OUT=enp0s10 MAC source = 08:00:27:ea:cf:18 MAC dest = 08:00:27:b2:76:7e proto = 0x0800 IP SRC=192.168.10.11 IP DST=192.168.10.44, IP tos=0x00, IP proto=1
Jun 4 20:48:40 vamos kernel: [45219.165523] [ebtables Drop] IN=enp0s3 OUT=enp0s9 MAC source = 08:00:27:ea:cf:18 MAC dest = 08:00:27:b2:76:7e proto = 0x0800 IP SRC=192.168.10.11 IP DST=192.168.10.44, IP tos=0x00, IP proto=1
特定I/Fからのデータのログ化
設定
「-i enp0s3」により、特定I/Fの入力を、「--log-ip --log-prefix "[ebtables From enp0s3]"」によりログ化。
$ sudo ebtables -A FORWARD -i enp0s3 --log-ip --log-prefix "[ebtables From enp0s3]"
$ sudo ebtables -L
Bridge table: filter
Bridge chain: INPUT, entries: 0, policy: ACCEPT
Bridge chain: FORWARD, entries: 1, policy: ACCEPT
-i enp0s3 --log-level notice --log-prefix "[ebtables From enp0s3]" --log-ip -j CONTINUE
Bridge chain: OUTPUT, entries: 0, policy: ACCEPT
結果
下記ログ。IPパケットやARPパケットが見える。
$ tail /var/log/syslog
...
Jun 4 20:52:13 vamos kernel: [45431.670263] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s10 MAC source = 08:00:27:ea:cf:18 MAC dest = 08:00:27:b2:76:7e proto = 0x0800 IP SRC=192.168.10.11 IP DST=192.168.10.44, IP tos=0x00, IP proto=1
Jun 4 20:52:18 vamos kernel: [45436.736065] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s10 MAC source = 08:00:27:ea:cf:18 MAC dest = 08:00:27:b2:76:7e proto = 0x0806
Jun 4 20:52:18 vamos kernel: [45436.765031] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s10 MAC source = 08:00:27:ea:cf:18 MAC dest = 08:00:27:b2:76:7e proto = 0x0806
...
Jun 4 20:52:51 vamos kernel: [45469.660584] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s9 MAC source = 08:00:27:c2:b3:07 MAC dest = 08:00:27:d0:a0:46 proto = 0x0800 IP SRC=192.168.10.22 IP DST=192.168.10.33, IP tos=0x00, IP proto=1
Jun 4 20:52:56 vamos kernel: [45474.665604] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s9 MAC source = 08:00:27:c2:b3:07 MAC dest = 08:00:27:d0:a0:46 proto = 0x0806
Jun 4 20:52:56 vamos kernel: [45474.777063] [ebtables From enp0s3] IN=enp0s3 OUT=enp0s9 MAC source = 08:00:27:c2:b3:07 MAC dest = 08:00:27:d0:a0:46 proto = 0x0806
EOF