本文書について
googleが公開してくれたtsunamiについて、現状を確認しました。
- 何をどの程度見てくれるのか
- open sourceなので、今後はどのように発展しそうか
- 既存のツールとのすみ分けは
今回は書きかけです。検証途中のままですが、公開します。
- 一部エラー吐いてるから、もしかしたら何かおかしいのかもしれない
- 自分が運用しているハニーポットに試してみたところ、ncrackはきちんとアタックしてた
- どんなふうに動いてるのか、どんなログが出るのか、等を知ってもらいたい
サマリ
プレ アルファ版です。
- Current Status参照
-
Currently Tsunami is in 'pre-alpha' release for developer preview.(tsunamiは開発者向けプレビュー用の「pre-alpha」リリースです。)
fingerprintはnmapの推定を利用
- そのため、ベンダパッケージのものは正しく読み取れない可能性がある(バックポートされているものが正しく読めず)
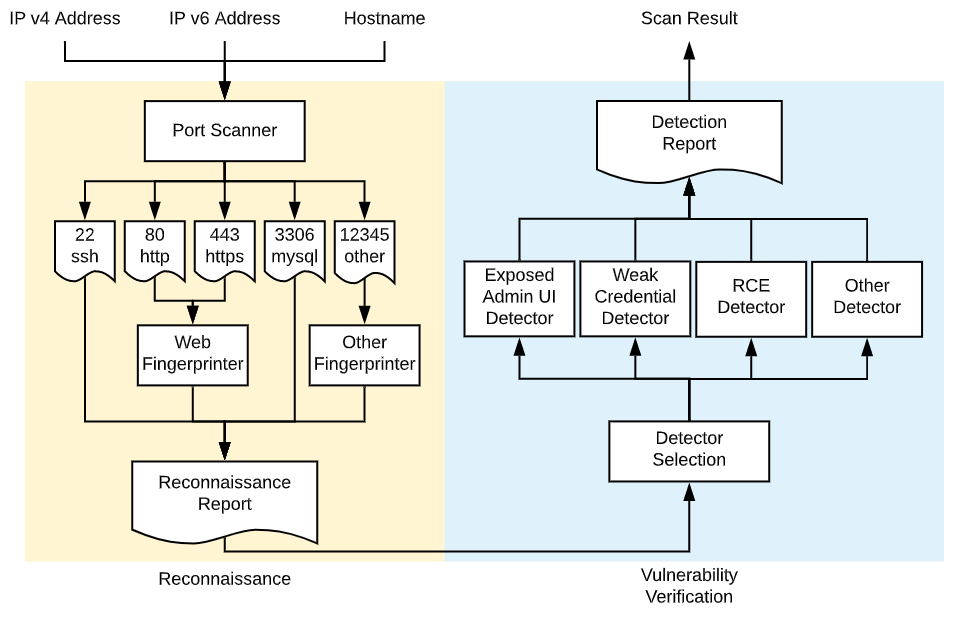
pluginによって、拡張できる感じです。
- tunami-security-scanner-plugins参照
- 現状、exsample_vuln_detector、exsample_calling_commandが登録されている
- Detectorの強化により、脆弱性の認知ができるようになるっぽい
- あくまで pre-alphaなので、プレビュー用の脆弱性スキャナ(Jupyter Notebook server用)以外はまともに検出できていないようです
現時点で、開発者以外が使うのはツラい
- 情報を追いかけて、可能ならコミットしてほしいし、していきたい
- しかしながら、例えばすぐに OpenVASやNessusと入れ替わるかといえば、「No」
- 一般運用者は、ある程度開発が進んでから並行運用するのがよさそう
- また、ネットワーク型なので、Vulsのような内部から検出するスキャナと併用するのがよいかと思われる(同じ「脆弱性スキャナ」という分類だが、「何のために」の部分の適用対象等が異なるため)
tsunamiを使う
tsunamiのインストール
minimumだと、gitやcurlも必要ですね。
tsunamiの Quick Start そのままです。
- テスト用の脆弱性のあるアプリケーションは利用しないので、
docker run --...は無視します。 -
quick_start.sh実行後、/home/<ユーザ名>/tsunamiに環境が用意されます。
~$ sudo apt-get install nmap ncrack openjdk-11-jdk curl git
~$ bash -c "$(curl -sfL https://raw.githubusercontent.com/google/tsunami-security-scanner/master/quick_start.sh)"
自分自身に対するスキャンを実施してみます。
- 上記
quick_start.sh終了時にコマンド例が出るので、それを実行します。(ユーザはhogehugaでやっています)
~$ cd tsunami
tsunami$ java -cp "tsunami-main-0.0.2-SNAPSHOT-cli.jar:/home/hogehuga/tsunami/plugins/*" \
-Dtsunami-config.location=/home/hogehuga/tsunami/tsunami.yaml \
com.google.tsunami.main.cli.TsunamiCli \
--ip-v4-target=127.0.0.1 \
--scan-results-local-output-format=JSON \
--scan-results-local-output-filename=/tmp/tsunami-output.json
検出テスト
ここからは、何がどこまで検出できるのかのテストをします。
- 現時点(2020/06/28)での、実装されているPluginでの検出テスト。
- 今後は、pluginを充実させていくことで検査がよくなっていくと思われます。
環境構築
Ubuntu18.04のaptで導入可能な古いパッケージを使い、wordpressを作る。
脆弱なユーザを作る(test:123456, pi:123456)。
- apache2
- mysql
- openssh (client/server/sftp)
- wordpress
# apt show apache2 -a | grep Version
Version: 2.4.29-1ubuntu4.13
Version: 2.4.29-1ubuntu4
# apt install apache2=2.4.29-1ubuntu4 apache2-utils=2.4.29-1ubuntu4 apache2-data=2.4.29-1ubuntu4 apache2-bin=2.4.29-1ubuntu4
#
# apt show mysql-server -a | grep Version
Version: 5.7.30-0ubuntu0.18.04.1
Version: 5.7.21-1ubuntu1
# apt install mysql-server=5.7.21-1ubuntu1 mysql-client=5.7.21-1ubuntu1
#
# apt show openssh-server -a | grep Version
Version: 1:7.6p1-4ubuntu0.3
Version: 1:7.6p1-4
# apt-get install openssh-server=1:7.6p1-4 openssh-client=1:7.6p1-4 openssh-sftp-server=1:7.6p1-4
# adduser test (passwd is 123456)
# useradd pi; passwd pi (as 123456)
wordpressは以下で導入
wordpress-4.9.4.tar.gz
createdb: wordpress
admin: wpadmin
pass: wpadmin
スキャンをしてみる
上記でスキャン後の結果は以下の通り
$ java -cp "tsunami-main-0.0.2-SNAPSHOT-cli.jar:/home/hogehuga/tsunami/plugins/*" \
-Dtsunami-config.location=/home/hogehuga/tsunami/tsunami.yaml com.google.tsunami.main.cli.TsunamiCli \
--ip-v4-target=127.0.0.1 \
--scan-results-local-output-format=JSON \
--scan-results-local-output-filename=/tmp/tsunami-output.json
スキャン中の標準出力
適宜読み飛ばしましょう
$ java -cp "tsunami-main-0.0.2-SNAPSHOT-cli.jar:/home/hogehuga/tsunami/plugins/*" -Dtsunami-config.location=/home/hogehuga/tsunami/tsunami.yaml com.google.tsunami.main.cli.TsunamiCli --ip-v4-target=127.0.0.1 --scan-results-local-output-format=JSON --scan-results-local-output-filename=/tmp/tsunami-output.json
6月 28, 2020 6:14:31 午後 com.google.tsunami.main.cli.TsunamiCli main
情報: Full classpath scan took 4.898 s
6月 28, 2020 6:14:31 午後 com.google.tsunami.common.config.ConfigModule configure
情報: Found Tsunami config class: com.google.tsunami.plugins.portscan.nmap.NmapPortScannerConfigs
6月 28, 2020 6:14:31 午後 com.google.tsunami.common.cli.CliOptionsModule configure
情報: Found CliOption: com.google.tsunami.common.io.archiving.GoogleCloudStorageArchiver$Options
6月 28, 2020 6:14:31 午後 com.google.tsunami.common.cli.CliOptionsModule configure
情報: Found CliOption: com.google.tsunami.main.cli.ScanResultsArchiver$Options
6月 28, 2020 6:14:31 午後 com.google.tsunami.common.cli.CliOptionsModule configure
情報: Found CliOption: com.google.tsunami.main.cli.option.ScanTargetCliOptions
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by com.google.inject.internal.cglib.core.$ReflectUtils$1 (file:/home/hogehuga/tsunami/tsunami-main-0.0.2-SNAPSHOT-cli.jar) to method java.lang.ClassLoader.defineClass(java.lang.String,byte[],int,int,java.security.ProtectionDomain)
WARNING: Please consider reporting this to the maintainers of com.google.inject.internal.cglib.core.$ReflectUtils$1
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.detectors.credentials.ncrack.NcrackWeakCredentialDetector
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.detectors.credentials.ncrack.NcrackWeakCredentialDetector is registered.
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.detectors.exposedui.hadoop.yarn.YarnExposedManagerApiDetector
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.detectors.exposedui.hadoop.yarn.YarnExposedManagerApiDetector is registered.
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.detectors.exposedui.jenkins.JenkinsExposedUiDetector
6月 28, 2020 6:14:31 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.detectors.exposedui.jenkins.JenkinsExposedUiDetector is registered.
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.detectors.exposedui.jupyter.JupyterExposedUiDetector
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.detectors.exposedui.jupyter.JupyterExposedUiDetector is registered.
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.detectors.exposedui.wordpress.WordPressInstallPageDetector
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.detectors.exposedui.wordpress.WordPressInstallPageDetector is registered.
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginLoadingModule configure
情報: Found plugin class: com.google.tsunami.plugins.portscan.nmap.NmapPortScanner
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugin.PluginBootstrapModule registerPlugin
情報: Plugin class com.google.tsunami.plugins.portscan.nmap.NmapPortScanner is registered.
6月 28, 2020 6:14:32 午後 com.google.tsunami.main.cli.TsunamiCli run
情報: TsunamiCli starting...
6月 28, 2020 6:14:32 午後 com.google.tsunami.workflow.DefaultScanningWorkflow runAsync
情報: Staring Tsunami scanning workflow.
6月 28, 2020 6:14:32 午後 com.google.tsunami.workflow.DefaultScanningWorkflow scanPorts
情報: Starting port scanning phase of the scanning workflow.
6月 28, 2020 6:14:32 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner scan
情報: Starting nmap scan.
6月 28, 2020 6:14:32 午後 com.google.tsunami.common.command.CommandExecutor execute
情報: Executing the following command: '/usr/bin/nmap --unprivileged -Pn -n -sT -sV --version-intensity 5 -T4 --script banner 127.0.0.1 -oX /tmp/nmap1144012732494230082.report'
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner scan
情報: Finished nmap scan on target '127.0.0.1' in 27.47 s.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner extractServicesFromNmapRun
情報: Building PortScanningReport from Nmap result.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner logIdentifiedNetworkService
情報: Nmap identified service: ip 127.0.0.1, port 22, protocol TCP, service ssh, software OpenSSH, version 7.6p1 Ubuntu 4, banner SSH-2.0-OpenSSH_7.6p1 Ubuntu-4
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner logIdentifiedNetworkService
情報: Nmap identified service: ip 127.0.0.1, port 80, protocol TCP, service http, software Apache httpd, version 2.4.29
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner logIdentifiedNetworkService
情報: Nmap identified service: ip 127.0.0.1, port 631, protocol TCP, service ipp, software CUPS, version 2.2
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.portscan.nmap.NmapPortScanner logIdentifiedNetworkService
情報: Nmap identified service: ip 127.0.0.1, port 3306, protocol TCP, service mysql, software MySQL, version 5.7.30-0ubuntu0.18.04.1, banner [\x00\x00\x00\x0A5.7.30-0ubuntu0.18.04.1\x00+\x00\x00\x00)\x1D\ x1F\x1E[}6.\x00\xFF\xFF\x08\x02\x00\xFF\xC1\x15\x00\x00\x00\x00\x00\...
6月 28, 2020 6:15:00 午後 com.google.tsunami.workflow.DefaultScanningWorkflow fingerprintNetworkServices
情報: Port scanning phase done, moving to service fingerprinting phase with '0' fingerprinter(s) selected.
6月 28, 2020 6:15:00 午後 com.google.tsunami.workflow.DefaultScanningWorkflow detectVulnerabilities
情報: Service fingerprinting phase done, moving to vuln detection phase.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.credentials.ncrack.NcrackWeakCredentialDetector detect
情報: Starting weak credential detection using ncrack.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.exposedui.hadoop.yarn.YarnExposedManagerApiDetector detect
情報: Starting unauthenticated Apache Yarn ResourceManager API detection
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.exposedui.jenkins.JenkinsExposedUiDetector detect
情報: Starting exposed ui detection for Jenkins
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.exposedui.jupyter.JupyterExposedUiDetector detect
情報: Starting exposed ui detection for Jupyter Notebook
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.exposedui.wordpress.WordPressInstallPageDetector detect
情報: Starting unfinished install page detection for WordPress.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient send
情報: Sending HTTP 'GET' request to 'http://127.0.0.1/wp-admin/install.php?step=1'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient send
情報: Sending HTTP 'GET' request to 'http://127.0.0.1/terminals/1'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient send
情報: Sending HTTP 'GET' request to 'http://127.0.0.1/view/all/newJob'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient send
情報: Sending HTTP 'GET' request to 'http://127.0.0.1/wp-login.php'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient send
情報: Sending HTTP 'GET' request to 'http://127.0.0.1/cluster/cluster'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient parseResponse
情報: Received HTTP response with code '404' for request to 'http://127.0.0.1/terminals/1'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient parseResponse
情報: Received HTTP response with code '404' for request to 'http://127.0.0.1/cluster/cluster'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient parseResponse
情報: Received HTTP response with code '404' for request to 'http://127.0.0.1/view/all/newJob'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugins.detectors.exposedui.hadoop.yarn.YarnExposedManagerApiDetector detect
情報: YarnExposedManagerApiDetector finished, detected '0' vulns.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient parseResponse
情報: Received HTTP response with code '200' for request to 'http://127.0.0.1/wp-login.php'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugin.PluginExecutorImpl buildFailedResult
警告: Plugin '/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/NcrackWeakCredentialDetectorPlugin/0.1' failed.
6月 28, 2020 6:15:00 午後 com.google.tsunami.common.net.http.HttpClient parseResponse
情報: Received HTTP response with code '200' for request to 'http://127.0.0.1/wp-admin/install.php?step=1'.
6月 28, 2020 6:15:00 午後 com.google.tsunami.plugin.PluginExecutorImpl buildFailedResult
警告: Plugin '/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/WordPressInstallPageDetector/0.1' failed.
6月 28, 2020 6:15:00 午後 com.google.tsunami.workflow.DefaultScanningWorkflow generateScanResults
情報: Tsunami scanning workflow done. Generating scan results.
6月 28, 2020 6:15:00 午後 com.google.tsunami.workflow.DefaultScanningWorkflow lambda$runAsync$0
情報: Tsunami scanning workflow traces:
Port scanning phase (27.57 s) with 1 plugin(s):
/Tsunami Dev (tsunami-dev@google.com)/PORT_SCAN/NmapPortScanner/0.1
Service fingerprinting phase (526.1 ms) with 0 plugin(s):
Vuln detection phase (311.8 ms) with 5 plugin(s):
/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/NcrackWeakCredentialDetectorPlugin/0.1 was selected for the following services: ssh (TCP, port 22), http (TCP, port 80), ipp (TCP, port 631), mysql (TCP, port 3306)
/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/YarnExposedManagerApiDetector/0.1 was selected for the following services: ssh (TCP, port 22), http (TCP, port 80), ipp (TCP, port 631), mysql (TCP, port 3306)
/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/JenkinsExposedUiDetector/0.1 was selected for the following services: ssh (TCP, port 22), http (TCP, port 80), ipp (TCP, port 631), mysql (TCP, port 3306)
/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/JupyterExposedUiDetector/0.1 was selected for the following services: ssh (TCP, port 22), http (TCP, port 80), ipp (TCP, port 631), mysql (TCP, port 3306)
/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/WordPressInstallPageDetector/0.1 was selected for the following services: ssh (TCP, port 22), http (TCP, port 80), ipp (TCP, port 631), mysql (TCP, port 3306)
# of detected vulnerability: 0.
6月 28, 2020 6:15:01 午後 com.google.tsunami.main.cli.TsunamiCli run
情報: Tsunami scan finished, saving results.
6月 28, 2020 6:15:01 午後 com.google.tsunami.common.io.archiving.RawFileArchiver archive
情報: Archiving data to file system with filename '/tmp/tsunami-output.json'.
6月 28, 2020 6:15:01 午後 com.google.tsunami.main.cli.TsunamiCli run
情報: TsunamiCli finished...
6月 28, 2020 6:15:01 午後 com.google.tsunami.main.cli.TsunamiCli main
情報: Full Tsunami scan took 35.21 s.
$
検査出力
{
"scanStatus": "PARTIALLY_SUCCEEDED",
"scanStartTimestamp": "2020-06-28T09:14:32.452Z",
"scanDuration": "28.516s",
"fullDetectionReports": {
},
"statusMessage": "Failed plugins:\n/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/NcrackWeakCredentialDetectorPlugin/0.1\n/Tsunami Team (tsunami-dev@google.com)/VULN_DETECTION/WordPressInstallPageDetector/0.1"
}
$
pluginの実行が一部失敗しているのかしら。
apache2のログ
..省略
127.0.0.1 - - [28/Jun/2020:18:15:00 +0900] "GET /terminals/1 HTTP/1.1" 404 501 "-" "TsunamiSecurityScanner"
127.0.0.1 - - [28/Jun/2020:18:15:00 +0900] "GET /view/all/newJob HTTP/1.1" 404 505 "-" "TsunamiSecurityScanner"
127.0.0.1 - - [28/Jun/2020:18:15:00 +0900] "GET /cluster/cluster HTTP/1.1" 404 505 "-" "TsunamiSecurityScanner"
127.0.0.1 - - [28/Jun/2020:18:15:00 +0900] "GET /wp-login.php HTTP/1.1" 200 1487 "-" "TsunamiSecurityScanner"
127.0.0.1 - - [28/Jun/2020:18:15:00 +0900] "GET /wp-admin/install.php?step=1 HTTP/1.1" 200 875 "-" "TsunamiSecurityScanner"
sshd
ハニーポットサーバに対してスキャンしたところ、ncrackが動いた。
ありがちなアカウントに対し、ありがちなパスワードリストでアクセスしている。
...
Jun 28 07:57:00 honeypotSVR sshd[25869]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57784
Jun 28 07:57:00 honeypotSVR sshd[25870]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57787
Jun 28 07:57:00 honeypotSVR sshd[25872]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57789
Jun 28 07:57:00 honeypotSVR sshd[25877]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57790
Jun 28 07:57:00 honeypotSVR sshd[25876]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57788
Jun 28 07:57:00 honeypotSVR sshd[25878]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57791
Jun 28 07:57:00 honeypotSVR sshd[25875]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57792
Jun 28 07:57:00 honeypotSVR sshd[25874]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57783
Jun 28 07:57:00 honeypotSVR sshd[25873]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57785
Jun 28 07:57:00 honeypotSVR sshd[25869]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57784 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25870]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57787 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25872]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57789 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25877]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57790 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25876]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57788 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25878]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57791 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25874]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57783 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25875]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57792 [preauth]
Jun 28 07:57:00 honeypotSVR sshd[25873]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57785 [preauth]
Jun 28 07:57:01 honeypotSVR sshd[25871]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57786
Jun 28 07:57:01 honeypotSVR sshd[25871]: Connection closed by invalid user azureuser xxx.xxx.xxx.xxx port 57786 [preauth]
Jun 28 07:57:01 honeypotSVR sshd[25889]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57793
Jun 28 07:57:01 honeypotSVR sshd[25890]: Invalid user azureuser from xxx.xxx.xxx.xxx port 57794
...
スキャンした側にはncrackのログがある
# Ncrack 0.6 scan initiated Sun Jun 28 21:00:38 2020 as: /usr/bin/ncrack -T3 --user adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,adm,info,info,info,info,info,info --pass ,123456,password,12345678,qwerty,123456789,12345,1234,111111,1234567,dragon,123123,baseball,abc123,football,monkey,letmein,696969,shadow,master,666666,qwertyuiop,123321,mustang,1234567890,michael,654321,pussy,superman,1qaz2wsx,7777777,fuckyou,121212,000000,qazwsx,123qwe,killer,trustno1,jordan,jennifer,zxcvbnm,asdfgh,hunter,buster,soccer,harley,batman,andrew,tigger,sunshine,iloveyou,fuckme,2000,charlie,robert,thomas,hockey,ranger,daniel,starwars,klaster,112233,george,asshole,computer,michelle,jessica,pepper,1111,zxcvbn,555555,11111111,131313,freedom,777777,pass,fuck,maggie,159753,aaaaaa,ginger,princess,joshua,cheese,amanda,summer,love,ashley,6969,nicole,chelsea,biteme,matthew,access,987654321,dallas,austin,thunder,taylor,matrix --pairwise -f -oN /tmp/ncrack10125231009113685752.report ssh://xxx.xxx.xxx.xxx:22
# Ncrack done at Sun Jun 28 21:01:08 2020 -- 1 service scanned in 30.00 seconds.
nmap
nmapを利用したログが残っている
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE nmaprun>
<?xml-stylesheet href="file:///usr/bin/../share/nmap/nmap.xsl" type="text/xsl"?>
<!-- Nmap 7.60 scan initiated Sun Jun 28 18:14:32 2020 as: /usr/bin/nmap --unprivileged -Pn -n -sT -sV --version-intensity 5 -T4 --script banner -oX /tmp/nmap1144012732494230082.report 127.0.0
.1 -->
<nmaprun scanner="nmap" args="/usr/bin/nmap --unprivileged -Pn -n -sT -sV --version-intensity 5 -T4 --script banner -oX /tmp/nmap1144012732494230082.report 127.0.0.1" start="1593335672" startstr="Sun Jun 28 18:14:32 2020" version="7.60" xmloutputversion="1.04">
<scaninfo type="connect" protocol="tcp" numservices="1000" services="1,3-4,6-7,9,13,17,19-26,30,32-33,37,42-43,49,53,70,79-85,88-90,99-100,106,109-111,113,119,125,135,139,143-144,146,161,163,179,199,211-212,222,254-256,259,264,280,301,306,311,340,366,389,406-407,416-417,425,427,443-445,458,464-465,481,497,500,512-515,524,541,543-545,548,554-555,563,587,593,616-617,625,631,636,646,648,666-668,683,687,691,700,705,711,714,720,722,726,749,765,777,783,787,800-801,808,843,873,880,888,898,900-903,911-912,981,987,990,992-993,995,999-1002,1007,1009-1011,1021-1100,1102,1104-1108,1110-1114,1117,1119,1121-1124,1126,1130-1132,1137-1138,1141,1145,1147-1149,1151-1152,1154,1163-1166,1169,1174-1175,1183,1185-1187,1192,1198-1199,1201,1213,1216-1218,1233-1234,1236,1244,1247-1248,1259,1271-1272,1277,1287,1296,1300-1301,1309-1311,1322,1328,1334,1352,1417,1433-1434,1443,1455,1461,1494,1500-1501,1503,1521,1524,1533,1556,1580,1583,1594,1600,1641,1658,1666,1687-1688,1700,1717-1721,1723,1755,1761,1782-1783,1801,1805,1812,1839-1840,1862-1864,1875,1900,1914,1935,1947,1971-1972,1974,1984,1998-2010,2013,2020-2022,2030,2033-2035,2038,2040-2043,2045-2049,2065,2068,2099-2100,2103,2105-2107,2111,2119,2121,2126,2135,2144,2160-2161,2170,2179,2190-2191,2196,2200,2222,2251,2260,2288,2301,2323,2366,2381-2383,2393-2394,2399,2401,2492,2500,2522,2525,2557,2601-2602,2604-2605,2607-2608,2638,2701-2702,2710,2717-2718,2725,2800,2809,2811,2869,2875,2909-2910,2920,2967-2968,2998,3000-3001,3003,3005-3007,3011,3013,3017,3030-3031,3052,3071,3077,3128,3168,3211,3221,3260-3261,3268-3269,3283,3300-3301,3306,3322-3325,3333,3351,3367,3369-3372,3389-3390,3404,3476,3493,3517,3527,3546,3551,3580,3659,3689-3690,3703,3737,3766,3784,3800-3801,3809,3814,3826-3828,3851,3869,3871,3878,3880,3889,3905,3914,3918,3920,3945,3971,3986,3995,3998,4000-4006,4045,4111,4125-4126,4129,4224,4242,4279,4321,4343,4443-4446,4449,4550,4567,4662,4848,4899-4900,4998,5000-5004,5009,5030,5033,5050-5051,5054,5060-5061,5080,5087,5100-5102,5120,5190,5200,5214,5221-5222,5225-5226,5269,5280,5298,5357,5405,5414,5431-5432,5440,5500,5510,5544,5550,5555,5560,5566,5631,5633,5666,5678-5679,5718,5730,5800-5802,5810-5811,5815,5822,5825,5850,5859,5862,5877,5900-5904,5906-5907,5910-5911,5915,5922,5925,5950,5952,5959-5963,5987-5989,5998-6007,6009,6025,6059,6100-6101,6106,6112,6123,6129,6156,6346,6389,6502,6510,6543,6547,6565-6567,6580,6646,6666-6669,6689,6692,6699,6779,6788-6789,6792,6839,6881,6901,6969,7000-7002,7004,7007,7019,7025,7070,7100,7103,7106,7200-7201,7402,7435,7443,7496,7512,7625,7627,7676,7741,7777-7778,7800,7911,7920-7921,7937-7938,7999-8002,8007-8011,8021-8022,8031,8042,8045,8080-8090,8093,8099-8100,8180-8181,8192-8194,8200,8222,8254,8290-8292,8300,8333,8383,8400,8402,8443,8500,8600,8649,8651-8652,8654,8701,8800,8873,8888,8899,8994,9000-9003,9009-9011,9040,9050,9071,9080-9081,9090-9091,9099-9103,9110-9111,9200,9207,9220,9290,9415,9418,9485,9500,9502-9503,9535,9575,9593-9595,9618,9666,9876-9878,9898,9900,9917,9929,9943-9944,9968,9998-10004,10009-10010,10012,10024-10025,10082,10180,10215,10243,10566,10616-10617,10621,10626,10628-10629,10778,11110-11111,11967,12000,12174,12265,12345,13456,13722,13782-13783,14000,14238,14441-14442,15000,15002-15004,15660,15742,16000-16001,16012,16016,16018,16080,16113,16992-16993,17877,17988,18040,18101,18988,19101,19283,19315,19350,19780,19801,19842,20000,20005,20031,20221-20222,20828,21571,22939,23502,24444,24800,25734-25735,26214,27000,27352-27353,27355-27356,27715,28201,30000,30718,30951,31038,31337,32768-32785,33354,33899,34571-34573,35500,38292,40193,40911,41511,42510,44176,44442-44443,44501,45100,48080,49152-49161,49163,49165,49167,49175-49176,49400,49999-50003,50006,50300,50389,50500,50636,50800,51103,51493,52673,52822,52848,52869,54045,54328,55055-55056,55555,55600,56737-56738,57294,57797,58080,60020,60443,61532,61900,62078,63331,64623,64680,65000,65129,65389"/>
<verbose level="0"/>
<debugging level="0"/>
<host starttime="1593335673" endtime="1593335699"><status state="up" reason="user-set" reason_ttl="0"/>
<address addr="127.0.0.1" addrtype="ipv4"/>
<hostnames>
</hostnames>
<ports><extraports state="closed" count="996">
<extrareasons reason="conn-refused" count="996"/>
</extraports>
<port protocol="tcp" portid="22"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="ssh" product="OpenSSH" version="7.6p1 Ubuntu 4" extrainfo="Ubuntu Linux; protocol 2.0" ostype="Linux" method="probed" conf="10"><cpe>cpe:/a:openbsd:openssh:7.6p1</cpe><cpe>cpe:/o:linux:linux_kernel</cpe></service><script id="banner" output="SSH-2.0-OpenSSH_7.6p1 Ubuntu-4"/></port>
<port protocol="tcp" portid="80"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="http" product="Apache httpd" version="2.4.29" extrainfo="(Ubuntu)" method="probed" conf="10"><cpe>cpe:/a:apache:http_server:2.4.29</cpe></service></port>
<port protocol="tcp" portid="631"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="ipp" product="CUPS" version="2.2" method="probed" conf="10"><cpe>cpe:/a:apple:cups:2.2</cpe></service></port>
<port protocol="tcp" portid="3306"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="mysql" product="MySQL" version="5.7.30-0ubuntu0.18.04.1" method="probed" conf="10"><cpe>cpe:/a:mysql:mysql:5.7.30-0ubuntu0.18.04.1</cpe></service><script id="banner" output="[\x00\x00\x00\x0A5.7.30-0ubuntu0.18.04.1\x00+\x00\x00\x00)\x1D\
x1F\x1E[}6.\x00\xFF\xFF\x08\x02\x00\xFF\xC1\x15\x00\x00\x00\x00\x00\...
"/></port>
</ports>
<times srtt="74" rttvar="66" to="100000"/>
</host>
<runstats><finished time="1593335699" timestr="Sun Jun 28 18:14:59 2020" elapsed="26.84" summary="Nmap done at Sun Jun 28 18:14:59 2020; 1 IP address (1 host up) scanned in 26.84 seconds" exit="success"/><hosts up="1" down="0" total="1"/>
</runstats>
</nmaprun>
- openssh-serverは
version="7.6p1 Ubuntu 4"と正しく読めているようだ。バナーのおかげか。 - CPEは出ているが、パッケージの場合はバックポートがあるため、これだけを見ても正しくDetectorは動作できないと思われる。OSごとのOVALと合わせて推定する必要がありそう。
- apache2は
2.4.29と推定されたので、バックポートが対応できない。むしろそれが当たり前か。 - ゆえに、推定バージョンでの検査は、Detectorが作りこまれるまでは正しく推定できないと思われる。(OSとパッチレベルがわかれば、OSごとのOVALで正しく推定可能。得たバージョンだけでCPEマッチするとバックポートが誤検知になる)
今後
FingerprinterやDetectorがどんどん出てくるとよさげ
- OSSなので「オープンな脆弱性スキャナ」が作れる可能性があるため、使うだけではなく開発も協力しやすい
- 例えば、「WordPress coreのSecurity Updateが出たから、バージョンで検出できるようにDetectorを書いてcommitする」みたいな貢献はできそう
- そのためには「ソフトウェアごとのPlugin」を、分かりやすく書いておく必要がありそう
とりあえずは、以上。