はじめに
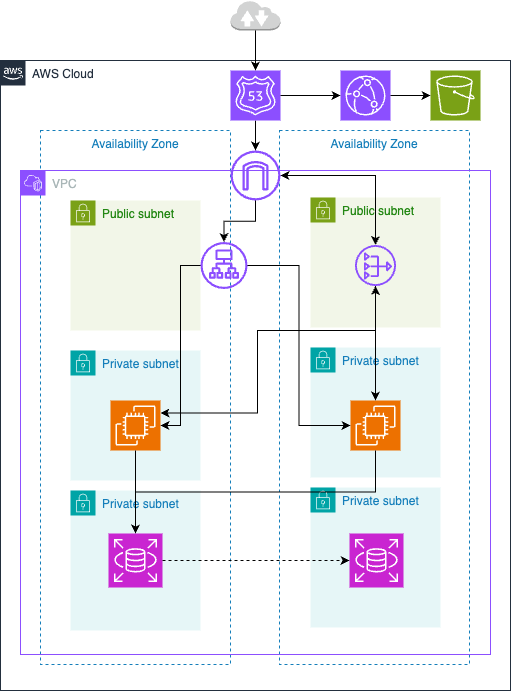
以前AWSにおける基本的なインフラ構成についてという記事を書き、その中に下記のインフラ構成図を載せました。
今回はこの構成図にあるリソースをTerraformで作成していきたいと思います。
Terraformコード集
provider.tf
ここではAWSプロバイダーの設定やTerraformのバージョン要件、state管理を行うバックエンド設定を書いていきます。
このファイルは各環境に動作が依存するので実際に使う場合は適宜変えることをお勧めします。
provider "aws" {
region = "ap-northeast-1"
}
terraform {
required_version = ">= 1.0.0"
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
backend "s3" {
bucket = "terraform-state-bucket"
key = "terraform.tfstate"
region = "ap-northeast-1"
}
}
variables.tf
ここではプロジェクト名や環境名などの変数定義を行います。
variable "project" {
type = string
default = "your-project-name"
}
variable "environment" {
type = string
default = "production"
}
vpc.tf
ここではvpcとsubnet, ネットワーク設定を作っていきます。
CIDRの設定等環境依存の場所が多いのでこの辺りは自分の手元の環境を見ながら適宜変えてください。
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
tags = {
Name = "${var.project}-vpc"
Environment = var.environment
}
}
resource "aws_subnet" "public_1" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.1.0/24"
availability_zone = "ap-northeast-1a"
tags = {
Name = "${var.project}-public-1"
Environment = var.environment
}
}
resource "aws_subnet" "public_2" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.2.0/24"
availability_zone = "ap-northeast-1c"
tags = {
Name = "${var.project}-public-2"
Environment = var.environment
}
}
resource "aws_subnet" "private_1" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.3.0/24"
availability_zone = "ap-northeast-1a"
tags = {
Name = "${var.project}-private-1"
Environment = var.environment
}
}
resource "aws_subnet" "private_2" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.4.0/24"
availability_zone = "ap-northeast-1c"
tags = {
Name = "${var.project}-private-2"
Environment = var.environment
}
}
resource "aws_internet_gateway" "main" {
vpc_id = aws_vpc.main.id
tags = {
Name = "${var.project}-igw"
Environment = var.environment
}
}
resource "aws_eip" "nat" {
domain = "vpc"
tags = {
Name = "${var.project}-nat-eip"
Environment = var.environment
}
}
resource "aws_nat_gateway" "main" {
allocation_id = aws_eip.nat.id
subnet_id = aws_subnet.public_1.id
tags = {
Name = "${var.project}-nat"
Environment = var.environment
}
}
resource "aws_route_table" "public" {
vpc_id = aws_vpc.main.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.main.id
}
tags = {
Name = "${var.project}-public-rt"
Environment = var.environment
}
}
resource "aws_route_table" "private" {
vpc_id = aws_vpc.main.id
route {
cidr_block = "0.0.0.0/0"
nat_gateway_id = aws_nat_gateway.main.id
}
tags = {
Name = "${var.project}-private-rt"
Environment = var.environment
}
}
resource "aws_route_table_association" "public_1" {
subnet_id = aws_subnet.public_1.id
route_table_id = aws_route_table.public.id
}
resource "aws_route_table_association" "public_2" {
subnet_id = aws_subnet.public_2.id
route_table_id = aws_route_table.public.id
}
resource "aws_route_table_association" "private_1" {
subnet_id = aws_subnet.private_1.id
route_table_id = aws_route_table.private.id
}
resource "aws_route_table_association" "private_2" {
subnet_id = aws_subnet.private_2.id
route_table_id = aws_route_table.private.id
}
route53.tf
ここではroute53に関する設定を作っていきます。
resource "aws_route53_zone" "main" {
name = "example.com"
tags = {
Environment = var.environment
}
}
ec2.tf
インスタンスとそれ周りのことを記載します。
resource "aws_iam_role" "ec2" {
name = "${var.project}-ec2-role"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "ec2.amazonaws.com"
}
}
]
})
}
resource "aws_iam_instance_profile" "ec2" {
name = "${var.project}-ec2-profile"
role = aws_iam_role.ec2.name
}
resource "aws_launch_template" "app" {
name_prefix = "${var.project}-template"
image_id = "ami-0d52744d6551d851e"
instance_type = "t3.micro"
network_interfaces {
associate_public_ip_address = false
security_groups = [aws_security_group.app.id]
}
iam_instance_profile {
name = aws_iam_instance_profile.ec2.name
}
user_data = base64encode(<<-EOF
#!/bin/bash
yum update -y
yum install -y nginx
systemctl start nginx
systemctl enable nginx
EOF
)
tags = {
Name = "${var.project}-lt"
Environment = var.environment
}
}
resource "aws_autoscaling_group" "app" {
name = "${var.project}-asg"
desired_capacity = 2
max_size = 4
min_size = 2
target_group_arns = [aws_lb_target_group.app.arn]
vpc_zone_identifier = [aws_subnet.private_1.id, aws_subnet.private_2.id]
launch_template {
id = aws_launch_template.app.id
version = "$Latest"
}
tag {
key = "Name"
value = "${var.project}-app"
propagate_at_launch = true
}
}
alb.tf
albの作成やそれに必要な設定を書いています。
resource "aws_security_group" "alb" {
name = "${var.project}-alb-sg"
description = "Security group for ALB"
vpc_id = aws_vpc.main.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "${var.project}-alb-sg"
Environment = var.environment
}
}
resource "aws_lb" "main" {
name = "${var.project}-alb"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.alb.id]
subnets = [aws_subnet.public_1.id, aws_subnet.public_2.id]
tags = {
Name = "${var.project}-alb"
Environment = var.environment
}
}
resource "aws_lb_target_group" "app" {
name = "${var.project}-tg"
port = 80
protocol = "HTTP"
vpc_id = aws_vpc.main.id
health_check {
enabled = true
healthy_threshold = 2
interval = 30
matcher = "200"
path = "/"
port = "traffic-port"
protocol = "HTTP"
timeout = 5
unhealthy_threshold = 2
}
tags = {
Name = "${var.project}-tg"
Environment = var.environment
}
}
resource "aws_lb_listener" "http" {
load_balancer_arn = aws_lb.main.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.app.arn
}
}
rds.tf
DBに関する設定を書いていきます。
resource "aws_db_subnet_group" "main" {
name = "${var.project}-db-subnet-group"
subnet_ids = [aws_subnet.private_1.id, aws_subnet.private_2.id]
tags = {
Name = "${var.project}-db-subnet-group"
Environment = var.environment
}
}
resource "aws_db_instance" "main" {
identifier = "${var.project}-db"
engine = "mysql"
engine_version = "8.0"
instance_class = "db.t3.micro"
allocated_storage = 20
db_name = "myapp"
username = "admin"
password = "your-password-here"
db_subnet_group_name = aws_db_subnet_group.main.name
vpc_security_group_ids = [aws_security_group.rds.id]
multi_az = true
skip_final_snapshot = true
tags = {
Name = "${var.project}-db"
Environment = var.environment
}
}
security_groups.tf
セキュリティグループに関して記載していきます。
ここもサービスに依存するので適宜変えることをお勧めします。
resource "aws_security_group" "rds" {
name = "${var.project}-rds-sg"
description = "Security group for RDS"
vpc_id = aws_vpc.main.id
ingress {
from_port = 3306
to_port = 3306
protocol = "tcp"
security_groups = [aws_security_group.app.id]
}
tags = {
Name = "${var.project}-rds-sg"
Environment = var.environment
}
}
resource "aws_security_group" "app" {
name = "${var.project}-app-sg"
description = "Security group for application"
vpc_id = aws_vpc.main.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "${var.project}-app-sg"
Environment = var.environment
}
}