It's been a long time to see you guys, this is the 21st post for Tech-Circle Hands on Advent Calendar 2016.
Yesterday, rina0521 wrote the greatest article!
The article category of this week is IoT'n AI, but there is a hidden one... yes, something very important... that is Enterprise, you know.
First of all
This article is totally unrelated to my company, and only expresses my personal thought. Man, today I'm writing this post is Sunday, as usual. But anyway, let's start the story.
Excel, the DIVINE
Screenshotted evidences, application forms, project schedule books... once you look around, you will notice that this enterpris-ation is completely rotten.
Don't misunderstand, Excel is not a mere spreadsheet software, it's a greatful platform.
Do you remember my last article what I wrote last year? You've already learned that you can grant any formidable power you wish, to your Excel, by declaring the divine description in VBA.
And today, you'll get the sealed demonic knowledge... yes, the method how you can implement those enterpris-able force as DLL. I promise it enhances your enterpris-ability appriximately four times.
Breaking the seal
Suppose the environment that TCP communications from unauthorized binary files to the other hosts are restricted, except for MS Office Suite. This is crap, we need a quick resolution in this situation.
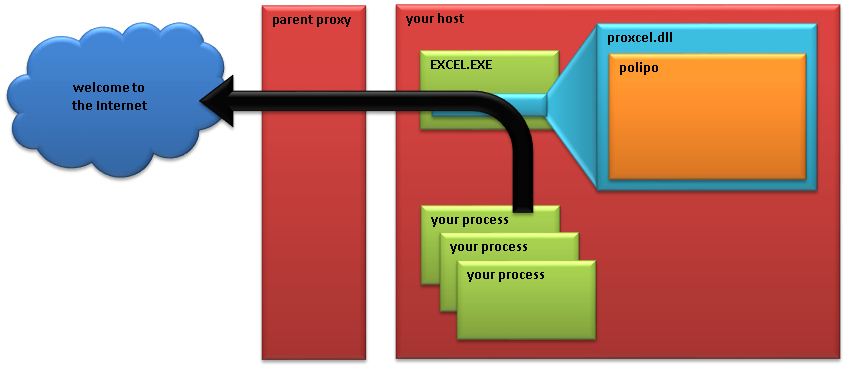
This time, we're going to make your Excel into a http proxy, by loading polipo1 DLL into the memory address space of Excel. First of all, we need to build polipo as DLL. Now let's call this DLL as Proxcel. After that, give polipo function the parameter of parent proxies. See below image2.
Prepare yourself
First, prepare a C compiler what you like, such as MinGW in order to build polipo DLL.
Remember that you must not use MinGW64 if your Excel is 32bit. MinGW64 seems that it ignores -m32 flag, and 32bit Excel cannot load 64bit DLL. Yeah, I know your Excel is 32bit. How absurd this situation is!
Oh, just one more thing, MinGW doesn't have make.exe, so you need to copy or rename the original mingw32-make.exe to make.exe, or install GNU Make.
The Forbidden Ritual
Next, clone polipo repository and modify some files like below.
Of course I know you love DF3, so I couldn't help pasting that in DF diff format.
--- snip ---
00013 | ||00013 |
00014 L|# CC = gcc ||00014 R|CC = gcc
00015 L|CDEBUGFLAGS = -Os -g -Wall -fno-strict-aliasing ||00015 R|CDEBUGFLAGS = -static
| ||00016 R|#CDEBUGFLAGS = -Os -g -Wall -fno-strict-aliasing
00016 | ||00017 |
--- snip ---
00037 | ||00038 |
00038 L|# EXE=.exe ||00039 R|EXE=.dll
00039 L|# LDLIBS = -lws2_32 ||00040 R|LDLIBS = -lws2_32
| ||00041 R|LDFLAGS = -shared
00040 | ||00042 |
--- snip ---
00074 | ||00076 |
| ||00077 R|proxcel$(EXE): polipo$(EXE)
| ||00078 R| cp polipo$(EXE) proxcel$(EXE)
| ||00079 R|
00075 |polipo$(EXE): $(OBJS) ||00080 |polipo$(EXE): $(OBJS)
--- snip ---
00083 | ||00088 |
00084 L|all: polipo$(EXE) polipo.info html/index.html loca||00089 R|all: proxcel$(EXE) polipo.info html/index.html loc
00085 | ||00090 |
--- snip ---
00135 |clean: ||00140 |clean:
00136 L| -rm -f polipo$(EXE) *.o *~ core TAGS gmon.out ||00141 R| -rm -f proxcel$(EXE) polipo$(EXE) *.o *~ core
00137 | -rm -f polipo.cp polipo.fn polipo.log polipo.v||00142 | -rm -f polipo.cp polipo.fn polipo.log polipo.v
--- snip ---
--- snip ---
00040 | ||00040 |
| ||00041 R|void __declspec(dllexport) __cdecl RunProxy(void)
| ||00042 R| char *argv[] = {"dummy", "--", "proxyAddress=\
| ||00043 R| main(sizeof(argv) / sizeof(argv[0]), argv);
| ||00044 R|}
| ||00045 R|
00041 |int ||00046 |int ```
--- snip ---
Crap, the full code couldn't fit in the area. The code added to main.c is like below.
-- snip --
void __declspec(dllexport) __cdecl RunProxy(void) {
char *argv[] = {"dummy", "--", "proxyAddress=\"127.0.0.1\"", "proxyPort=33333", "parentProxy=<parent proxy address>:<parent proxy port>"};
main(sizeof(argv) / sizeof(argv[0]), argv);
}
-- snip --
Yeah whatever, now let's build it.
/work/polipo $ make
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -c -o util.o util.c
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -c -o event.o event.c
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -c -o io.o io.c
-- snip --
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -c -o socks.o socks.c
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -c -o mingw.o mingw.c
gcc -static -DLOCAL_ROOT=\"/usr/share/polipo/www/\" -DDISK_CACHE_ROOT=\"/var/cache/polipo/\" -shared -o polipo.dll util.o event.o io.o chunk.o atom.o object.o log.o diskcache.o main.o config.o local.o http.o client.o server.o auth.o tunnel.o http_parse.o parse_time.o dns.o forbidden.o md5import.o ftsimport.o socks.o mingw.o -lws2_32
cp polipo.dll proxcel.dll
/work/polipo $
Okay, our divine arsenal, proxcel.dll has been built now!!
Do everything as a Divine-Excelist
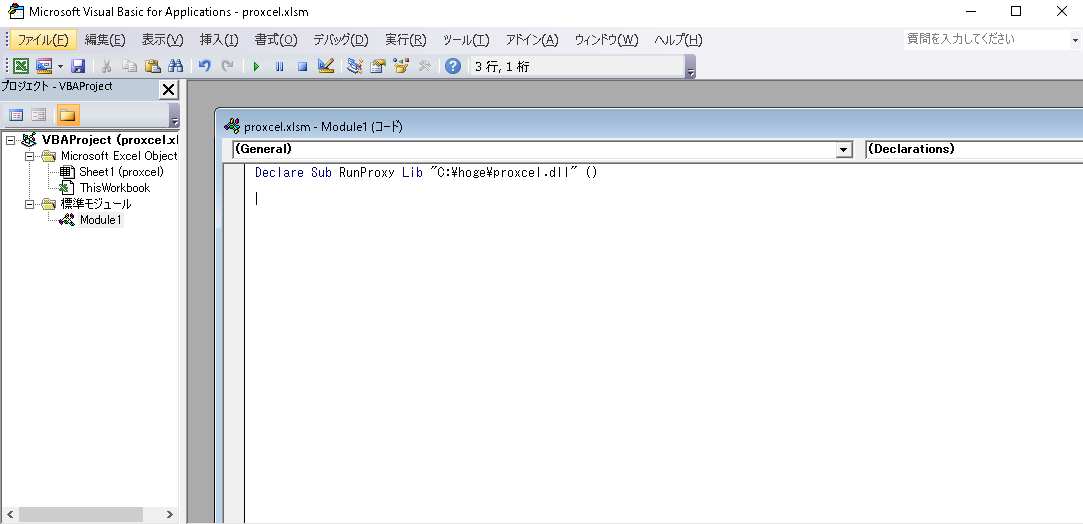
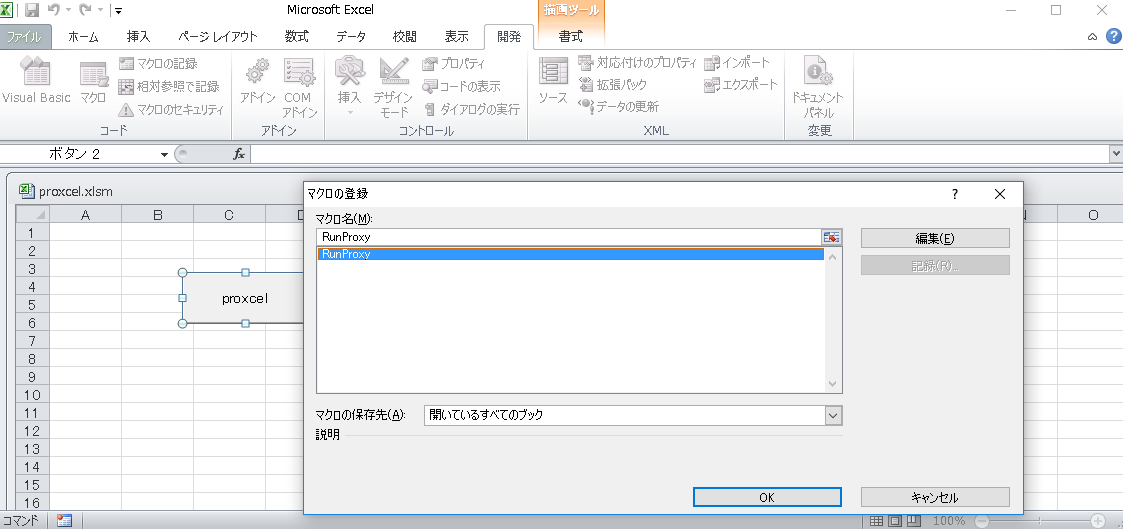
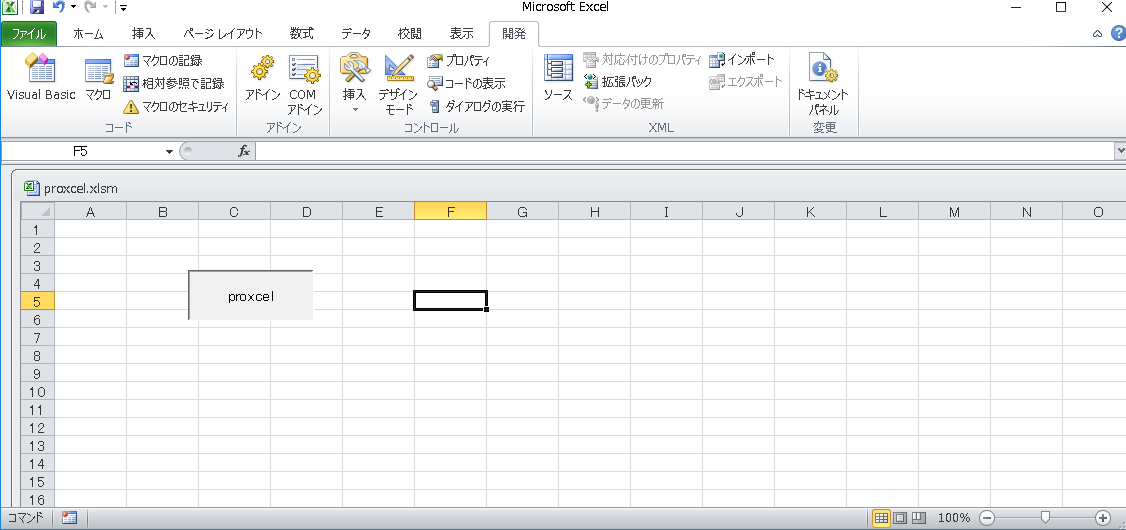
The final step, only we have to do is, just code like below on Excel!
Declare Sub RunProxy Lib "C:\**snip**\proxcel.dll" ()
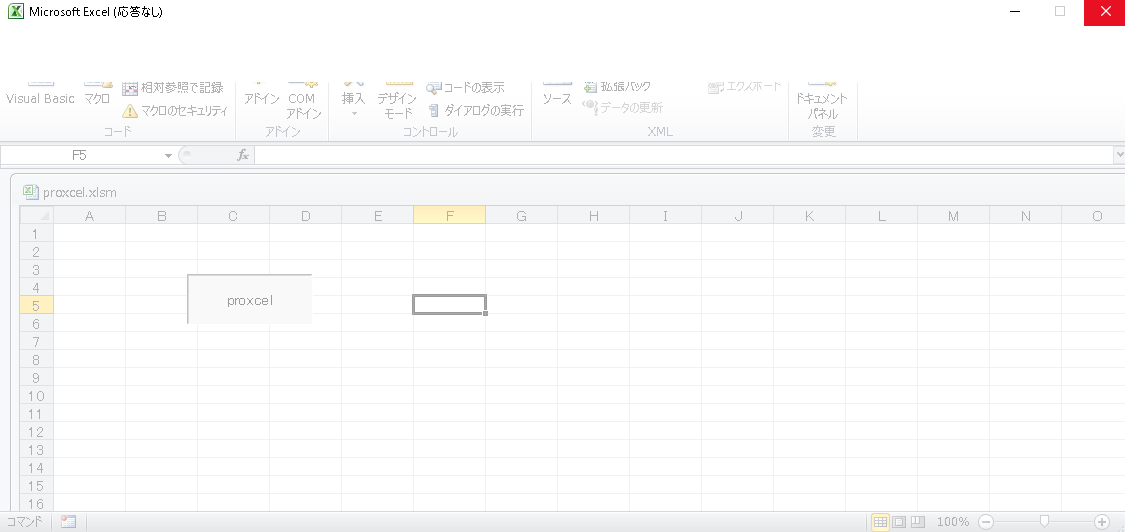
Now then, just push "proxcel" enterpris-ingly!!
You can't go back anymore...!
Hey, don't worry, it's okay, though Excel looks frozen, it's correct for now, because it's running as single-threading mode.
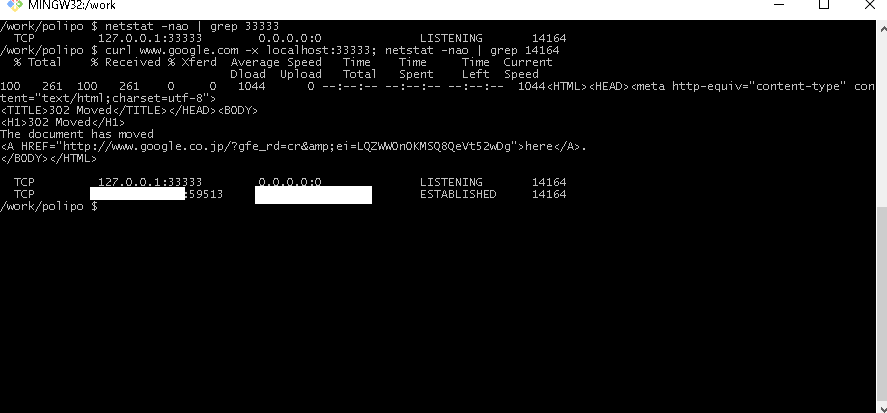
Let's check Excel PID and listening status.
Awesome..!! you can see that Excel is listening at "127.0.0.1:33333"!
What!? You doubt this merciless power...!? Okay, then I'll show you the proof!!
Woohoooooo!!! EXCELlent...!! How enterpris-ing this is!
Conclusion
This article was super, wasn't this?
More importantly, if you want to get various kinds of knowledge as a powerful System Engineer correctly, you must read System Engineer Advent Calendar 2016.
The next post
morio36 will take care of the next one.
I can't wait to see that!