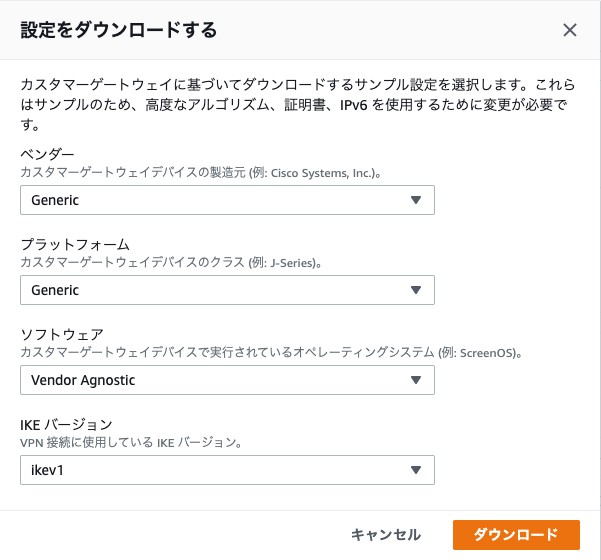
AWS Site to Site VPN を設定する際、Vyattaの動的ルーティング(BGP)用の設定ファイルテンプレートをダウンロードして楽に設定することもできるが、あえて手動で設定してみる。
Vyattaと書いてますが、VyOS1.3を使っています。
まず、Genericでテンプレートをダウンロードしておく。以降、設定値は基本的にこのファイルから拾っていく。
IKEの設定
ここはコピペでOK
set vpn ipsec ike-group AWS lifetime '28800'
set vpn ipsec ike-group AWS proposal 1 dh-group '2'
set vpn ipsec ike-group AWS proposal 1 encryption 'aes128'
set vpn ipsec ike-group AWS proposal 1 hash 'sha1'
set vpn ipsec ike-group AWS dead-peer-detection action 'restart'
set vpn ipsec ike-group AWS dead-peer-detection interval '15'
set vpn ipsec ike-group AWS dead-peer-detection timeout '30'
IPsecの設定
ここはコピペでOK
set vpn ipsec ipsec-interfaces interface 'eth0'
set vpn ipsec esp-group AWS compression 'disable'
set vpn ipsec esp-group AWS lifetime '3600'
set vpn ipsec esp-group AWS mode 'tunnel'
set vpn ipsec esp-group AWS pfs 'enable'
set vpn ipsec esp-group AWS proposal 1 encryption 'aes128'
set vpn ipsec esp-group AWS proposal 1 hash 'sha1'
IPsecのPeerの設定
for Peer1
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Peer1 IP | IPSec Tunnel #1 > #3: Tunnel Interface Configuration > Outside IP Addresses > Virtual Private Gateway |
| Pre shared key1 | IPSec Tunnel #1 > #1: Internet Key Exchange Configuration > Pre-Shared Key |
| Router Interface IP | 自分のルーターのInterfaceに割り当てられてるIP(EC2だったらそのPrivate IP) |
set vpn ipsec site-to-site peer <<Peer1 IP>> authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer <<Peer1 IP>> authentication pre-shared-secret '<<Pre shared key1>>'
set vpn ipsec site-to-site peer <<Peer1 IP>> description 'VPC tunnel 1'
set vpn ipsec site-to-site peer <<Peer1 IP>> ike-group 'AWS'
set vpn ipsec site-to-site peer <<Peer1 IP>> local-address '<<Router Interface IP>>'
set vpn ipsec site-to-site peer <<Peer1 IP>> vti bind 'vti0'
set vpn ipsec site-to-site peer <<Peer1 IP>> vti esp-group 'AWS'
for Peer2
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Peer2 IP | IPSec Tunnel #2 > #3: Tunnel Interface Configuration > Outside IP Addresses > Virtual Private Gateway |
| Pre shared key2 | IPSec Tunnel #2 > #1: Internet Key Exchange Configuration > Pre-Shared Key |
| Router Interface IP | 自分のルーターのInterfaceに割り当てられてるIP(EC2だったらそのPrivate IP) |
set vpn ipsec site-to-site peer <<Peer2 IP>> authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer <<Peer2 IP>> authentication pre-shared-secret '<<Pre shared key2>>'
set vpn ipsec site-to-site peer <<Peer2 IP>> description 'VPC tunnel 2'
set vpn ipsec site-to-site peer <<Peer2 IP>> ike-group 'AWS'
set vpn ipsec site-to-site peer <<Peer2 IP>> local-address '<<Router Interface IP>>'
set vpn ipsec site-to-site peer <<Peer2 IP>> vti bind 'vti1'
set vpn ipsec site-to-site peer <<Peer2 IP>> vti esp-group 'AWS'
Tunnel Interfaceの設定
for Tunnel1
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Tunnel1 IP CIDR | IPSec Tunnel #1 > #3: Tunnel Interface Configuration > Inside IP Addresses > Customer Gateway |
set interfaces vti vti0 address '<<Tunnel1 IP CIDR>>'
set interfaces vti vti0 description 'VPC tunnel 1'
set interfaces vti vti0 mtu '1436'
for Tunnel2
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Tunnel2 IP CIDR | IPSec Tunnel #2 > #3: Tunnel Interface Configuration > Inside IP Addresses > Customer Gateway |
set interfaces vti vti1 address '<<Tunnel2 IP CIDR>>'
set interfaces vti vti1 description 'VPC tunnel 2'
set interfaces vti vti1 mtu '1436'
BGP の設定
for Peer1
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Neighbor1 IP | IPSec Tunnel #1 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Neighbor IP Address |
| VGW ASN | IPSec Tunnel #1 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Virtual Private Gateway ASN |
| CGW ASN | IPSec Tunnel #1 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Customer Gateway AS |
set protocols bgp <<CGW ASN>> neighbor <<Neighbor1 IP>> remote-as '<<VGW ASN>>'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor1 IP>> address-family ipv4-unicast soft-reconfiguration 'inbound'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor1 IP>> timers holdtime '30'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor1 IP>> timers keepalive '10'
for Peer2
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| Neighbor2 IP | IPSec Tunnel #2 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Neighbor IP Address |
| VGW ASN | IPSec Tunnel #2 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Virtual Private Gateway ASN |
| CGW ASN | IPSec Tunnel #2 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Customer Gateway AS |
set protocols bgp <<CGW ASN>> neighbor <<Neighbor2 IP>> remote-as '<<VGW ASN>>'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor2 IP>> address-family ipv4-unicast soft-reconfiguration 'inbound'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor2 IP>> timers holdtime '30'
set protocols bgp <<CGW ASN>> neighbor <<Neighbor2 IP>> timers keepalive '10'
(Optional) AWSに注入する経路(例 : 192.168.0.0/16)
| 項目 | 設定値(Genericテンプレートから拾う) |
|---|---|
| CGW ASN | IPSec Tunnel #1 > #4: Border Gateway Protocol (BGP) Configuration > BGP Configuration Options > Customer Gateway AS |
set protocols bgp <<CGW ASN>> address-family ipv4-unicast network 192.168.0.0/16
確認
IKE確認
StateがupになってればOK
$ show vpn ike sa
Peer ID / IP Local ID / IP
------------ -------------
34.218.54.59 172.31.53.30
Description: VPC tunnel 1
State IKEVer Encrypt Hash D-H Group NAT-T A-Time L-Time
----- ------ ------- ---- --------- ----- ------ ------
up IKEv2 aes128 sha1_96 2(MODP_1024) no 3600 28800
Peer ID / IP Local ID / IP
------------ -------------
52.39.144.177 172.31.53.30
Description: VPC tunnel 2
State IKEVer Encrypt Hash D-H Group NAT-T A-Time L-Time
----- ------ ------- ---- --------- ----- ------ ------
up IKEv2 aes128 sha1_96 2(MODP_1024) no 3600 28800
IPsec確認
同じくStateがupになっていればOK
$ show vpn ipsec sa
Connection State Uptime Bytes In/Out Packets In/Out Remote address Remote ID Proposal
----------------------------- ------- -------- -------------- ---------------- ---------------- ----------- ----------------------------------
peer-34.218.54.59-tunnel-vti up 13m14s 5K/9K 82/160 34.218.54.59 N/A AES_CBC_128/HMAC_SHA1_96/MODP_1024
peer-52.39.144.177-tunnel-vti up 13m14s 5K/9K 82/160 52.39.144.177 N/A AES_CBC_128/HMAC_SHA1_96/MODP_1024
BGP確認
Peerが2つあるかどうか
$ show ip bgp summary
IPv4 Unicast Summary:
BGP router identifier 172.31.53.30, local AS number 65001 vrf-id 0
BGP table version 2
RIB entries 3, using 576 bytes of memory
Peers 2, using 43 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt
169.254.109.145 4 64512 90 89 0 0 0 00:14:17 1 2
169.254.151.165 4 64512 90 89 0 0 0 00:14:17 1 2
経路Advertise確認
BGPで 192.168.0.0/16 がadvertiseされてるかどうか
$ show ip bgp neighbors 169.254.109.145 advertised-routes
BGP table version is 2, local router ID is 172.31.53.30, vrf id 0
Default local pref 100, local AS 65001
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 172.31.0.0/16 0.0.0.0 0 64512 i
*> 192.168.0.0/16 0.0.0.0 0 32768 i
$ show ip bgp neighbors 169.254.151.165 advertised-routes
BGP table version is 2, local router ID is 172.31.53.30, vrf id 0
Default local pref 100, local AS 65001
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 172.31.0.0/16 0.0.0.0 0 64512 i
*> 192.168.0.0/16 0.0.0.0 0 32768 i
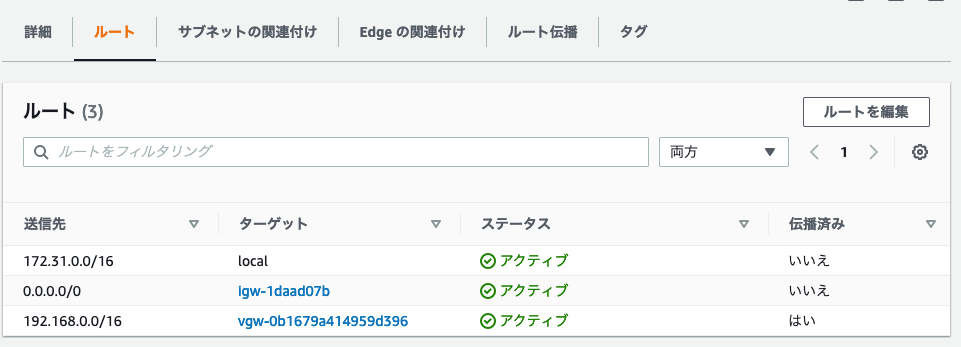
経路確認
今回VPCのCIDRは 172.31.0.0/16 なのでその経路があればOK
$ show ip route bgp
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
B>* 172.31.0.0/16 [20/100] via 169.254.151.165, vti1, weight 1, 00:17:52