はじめに
体調不良が続き、投稿が丸2日以上遅れてしまい面目ありません。めっきり寒くなってきましたので皆さんも風邪など召されぬようご自愛下さい。
当記事が参加する Snyk Advent Calendar 2021 は、任意に表彰される Snyk 賞の3名に「最新のiPad 64GB Wi-Fiモデル + Apple Pencil(第2世代)」が贈られる、製品の宣伝が目的のアドベントカレンダーです。
Snyk
https://snyk.io/
Snyk 社は、2015年に設立されたアメリカのボストンを拠点とするクラウドコンピューティングを専門とするサイバーセキュリティ企業です。
「Forbes Cloud 100 2021」で39位にランクインし、Snyk の評価額は2021年9月には85億ドル (9,340億円!) に急騰しています。 1 2
顧客として Google、Salesforce、Intuit、Atlassian などが利用しているようです。 3
Snyk の語源と読み方
Snyk は「So Now You Know」の略です。
創業者は sneak (スニーク)と発音しているようです。
また、開発チーム内では snick (スニック)と発音する人もいるようです。「スニック」とは、鍵が閉まるときのカチッという音のことで、鍵が閉まるときの音は安全性を高めるものだから、だとか。 4
製品
製品としては以下の4つになるようです。
| 製品名 | 概要 |
|---|---|
| Snyk Open Source | オープンソースの脆弱性を見つけて自動的に修正する |
| Snyk Code | アプリケーションコードの脆弱性をリアルタイムで見つけて修正する |
| Snyk Container | コンテナイメージと Kubernetes アプリケーションの脆弱性を見つけて修正する |
| Snyk Infrastructure as Code | Terraform、CloudFormation、Kubernetes、ARM テンプレートの設定ミスを見つけて修正する |
プラン
https://snyk.io/plans/
プランには Free, Team, Business, Enterprise の4つがあり、有償プランは開発者5人で Snyk Open Source か Snyk Container のいずれか1つで月額125ドルからのようです。
Free プラン
Free プランでは以下の上限があります。
| テスト | 月間上限 |
|---|---|
| Snyk Open Source | 月200回 |
| Snyk Code | 月100回 |
| Snyk Container | 月100回 |
| Snyk Infrastructure as Code | 月300回 |
サインアップ
Snyk は SaaS なので、アカウントを作成しないと始まりません。GitHub, Google, Bitbucket, Azure AD, Docker ID のいずれかのアカウントで作成可能です。
https://app.snyk.io/login
インターフェース
Snyk のインターフェースは以下の通り。
- Snyk - Web ベース
- Snyk CLI - コマンドラインベース
- Snyk API - Business プランか Enterpirse プランでのみ利用可能
- IDE plugins
- Snyk Vulnerability Scanner (JETBRAINS)
- Snyk Vulnerability Scanner (Visual Studio Code)
- Snyk Vulnerability Scanner (Visual Studio 2015, 2017, 2019)
- Snyk Security Scanner (ECLIPSE)
- Website Scanner - URL を入力して Web サイトをオンラインで検査
- Snyk Vulnerability Database -
- Snyk Advisor -
Snyk CLI
インストール
Snyk CLI は2021年12月現在、 npm, Yarn, Homebrew, Scoop, Docker, 単一実行ファイルなどでインストール可能なようです。
npm
npm install snyk@latest -g
Yarn
yarn global add snyk
Homebrew
brew tap snyk/tap && brew install snyk
結果
==> Tapping snyk/tap
Cloning into '/usr/local/Homebrew/Library/Taps/snyk/homebrew-tap'...
remote: Enumerating objects: 1960, done.
remote: Counting objects: 100% (924/924), done.
remote: Compressing objects: 100% (704/704), done.
remote: Total 1960 (delta 315), reused 751 (delta 218), pack-reused 1036
Receiving objects: 100% (1960/1960), 265.65 KiB | 5.11 MiB/s, done.
Resolving deltas: 100% (803/803), done.
Tapped 2 formulae (20 files, 330.8KB).
==> Downloading https://static.snyk.io/cli/v1.797.0/snyk-macos
######################################################################## 100.0%
==> Installing snyk from snyk/tap
🍺 /usr/local/Cellar/snyk/1.797.0: 3 files, 52.7MB, built in 4 seconds
==> Running `brew cleanup snyk`...
Disable this behaviour by setting HOMEBREW_NO_INSTALL_CLEANUP.
Hide these hints with HOMEBREW_NO_ENV_HINTS (see `man brew`).
Scoop
scoop bucket add snyk https://github.com/snyk/scoop-snyk
scoop install snyk
ヘルプ
snyk --help
Snyk CLI
Snyk CLI scans and monitors your projects for security vulnerabilities.
Visit https://snyk.io for more details.
Not sure where to start?
1. Authenticate with snyk auth.
2. Test your local project with snyk test.
3. Get alerted for new vulnerabilities with snyk monitor.
Available commands
To learn more about Snyk CLI use the --help option, e.g. snyk container --help or snyk auth --help
.
snyk auth
Authenticate Snyk CLI with a Snyk account.
snyk test
Test local project's dependencies for vulnerabilities.
snyk monitor
Snapshot and continuously monitor your project.
snyk container
Test container images for vulnerabilities.
snyk iac
Find security issues in your Infrastructure as Code files.
snyk code
Find security issues using static code analysis.
snyk config
Manage Snyk CLI configuration.
snyk protect
Applies the patches specified in your .snyk file to the local file system.
snyk policy
Display the .snyk policy for a package.
snyk ignore
Modifies the .snyk policy to ignore stated issues.
snyk wizard
Configure your .snyk policy file.
バージョン確認
snyk --version
2021年12月20日現在のバージョンを確認すると 1.797.0 でした。(ちなみにその後 12/20 に6回バージョンアップがあったようです。)
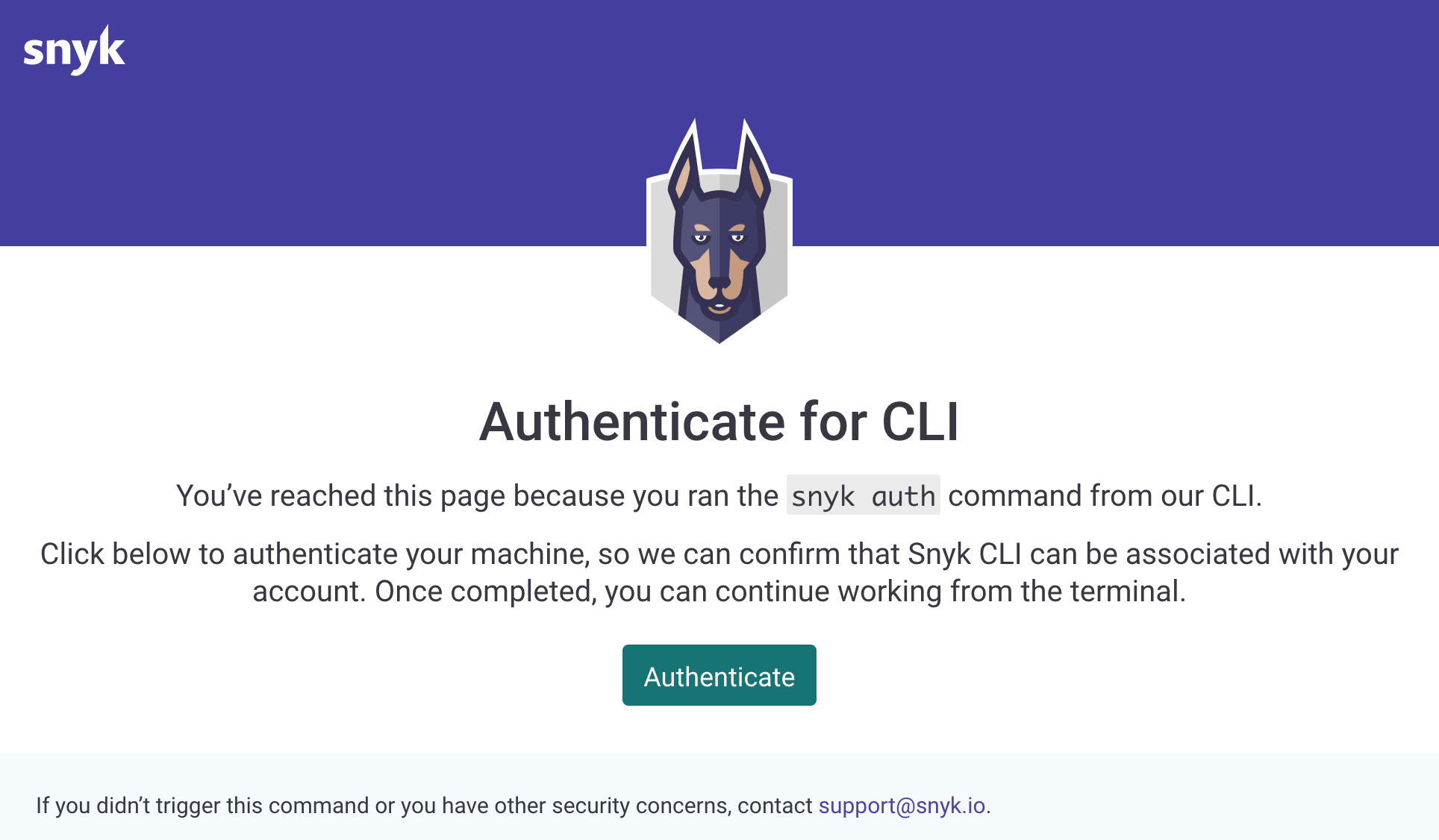
認証
snyk auth
結果
Now redirecting you to our auth page, go ahead and log in,
and once the auth is complete, return to this prompt and you'll
be ready to start using snyk.
If you can't wait use this url:
https://snyk.io/login?token=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx&utm_medium=cli&utm_source=cli&utm_campaign=HOMEBREW&os=darwin&docker=false
Your account has been authenticated. Snyk is now ready to be used.
上記コマンドを実行すると自動的にブラウザが起動します。
PHP アプリケーションの検査
PHP でサポートされているパッケージ管理ツール
Development Language Package manager/build tool PHP Composer
PHP でサポートされている拡張子
Language Extension PHP fcgi PHP php3 PHP php4 PHP php5 PHP phps PHP phpt PHP inc PHP aw PHP php PHP ctp
WordPress の脆弱性を検査する
パッケージの検査
mkdir snyk && cd $_
composer require johnpbloch/wordpress-core-installer
composer require johnpbloch/wordpress-core
snyk test
結果
Using version ^2.0 for johnpbloch/wordpress-core-installer
./composer.json has been created
Running composer update johnpbloch/wordpress-core-installer
Loading composer repositories with package information
Updating dependencies
Lock file operations: 1 install, 0 updates, 0 removals
- Locking johnpbloch/wordpress-core-installer (2.0.0)
Writing lock file
Installing dependencies from lock file (including require-dev)
Package operations: 1 install, 0 updates, 0 removals
- Installing johnpbloch/wordpress-core-installer (2.0.0): Extracting archive
Generating autoload files
Using version ^5.8 for johnpbloch/wordpress-core
./composer.json has been updated
Running composer update johnpbloch/wordpress-core
Loading composer repositories with package information
Updating dependencies
Lock file operations: 1 install, 0 updates, 0 removals
- Locking johnpbloch/wordpress-core (5.8.2)
Writing lock file
Installing dependencies from lock file (including require-dev)
Package operations: 1 install, 0 updates, 0 removals
- Installing johnpbloch/wordpress-core (5.8.2): Extracting archive
Generating autoload files
Testing /Users/bezeklik/Workspace/snyk...
Organization: bezeklik
Package manager: composer
Target file: composer.lock
Project name: snyk
Open source: no
Project path: /Users/bezeklik/Workspace/snyk
Licenses: enabled
✔ Tested 5 dependencies for known issues, no vulnerable paths found.
Next steps:
- Run `snyk monitor` to be notified about new related vulnerabilities.
- Run `snyk test` as part of your CI/test.
最新版の WordPress 5.8.2 なのでパッケージの脆弱性は検出されず。
コードの検査
snyk code test
結果
Testing /Users/bezeklik/Workspace/snyk ...
✗ [Low] XML External Entity (XXE) Injection
Path: wordpress/wp-includes/atomlib.php, line 173
Info: Unsanitized input from data from a remote resource flows to xml_parse. This may result in an XXE vulnerability. You may be vulnerable if using an old version of PHP (<8.0)
✗ [Medium] Open Redirect
Path: wordpress/wp-includes/js/backbone.js, line 2032
Info: Unsanitized input from the document location flows into replace, where it is used as an URL to redirect the user. This may result in an Open Redirect vulnerability.
✗ [Medium] Open Redirect
Path: wordpress/wp-admin/js/privacy-tools.js, line 91
Info: Unsanitized input from data from a remote resource flows into window.location, where it is used as an URL to redirect the user. This may result in an Open Redirect vulnerability.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-login.php, line 672
Info: setcookie has the Secure attribute set to false. Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Open Redirect
Path: wordpress/wp-includes/ms-settings.php, line 79
Info: Unsanitized input from an HTTP header flows into header, where it is used as an URL to redirect the user. This may result in an Open Redirect vulnerability.
✗ [Medium] Open Redirect
Path: wordpress/wp-includes/pluggable.php, line 1343
Info: Unsanitized input from an HTTP header flows into header, where it is used as an URL to redirect the user. This may result in an Open Redirect vulnerability.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/comment.php, line 577
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/comment.php, line 578
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/comment.php, line 579
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1031
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1032
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1033
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1034
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1035
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1036
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1039
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1040
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1043
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1044
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1045
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1046
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1049
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1050
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1051
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1052
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/pluggable.php, line 1055
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/option.php, line 1274
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 62
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie in HTTPS Session Without 'Secure' Attribute
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 63
Info: setcookie misses the Secure attribute (it is false by default). Set it to true to protect the cookie from man-in-the-middle attacks.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-login.php, line 416
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-login.php, line 419
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-login.php, line 672
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 577
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 578
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 579
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 595
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 596
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/comment.php, line 597
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1031
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1032
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1033
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1034
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1035
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1036
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1039
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1040
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1043
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1044
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1045
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1046
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1049
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1050
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1051
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1052
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/pluggable.php, line 1055
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/option.php, line 1097
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/option.php, line 1098
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/option.php, line 1274
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 62
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 63
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Sensitive Cookie Without 'HttpOnly' Flag
Path: wordpress/wp-admin/post.php, line 231
Info: setcookie misses the HttpOnly attribute (it is false by default). Set it to true to protect the cookie from possible malicious code on client side.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2432
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2565
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2568
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/l10n.php, line 1105
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-files.php, line 59
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/dashboard.php, line 1155
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/dashboard.php, line 1256
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/dashboard.php, line 1765
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/plugin-install.php, line 246
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-snoopy.php, line 1218
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp.php, line 461
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/update-core.php, line 559
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/update-core.php, line 733
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-theme.php, line 217
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/class-wp-ms-themes-list-table.php, line 512
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-phpass.php, line 83
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-phpass.php, line 84
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-phpass.php, line 152
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-phpass.php, line 154
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/image.php, line 504
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/plugin.php, line 1338
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/rss.php, line 813
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Caption.php, line 120
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-text-diff-renderer-table.php, line 453
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-text-diff-renderer-table.php, line 454
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-text-diff-renderer-table.php, line 467
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-embed.php, line 232
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-site.php, line 965
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Copyright.php, line 92
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Cache/Memcached.php, line 95
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/module.tag.apetag.php, line 314
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-term-query.php, line 740
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Author.php, line 102
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/schema.php, line 1078
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 122
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 302
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 510
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 600
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 762
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/cron.php, line 1224
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-blogs.php, line 135
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-blogs.php, line 153
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-blogs.php, line 269
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Category.php, line 115
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-oembed-controller.php, line 174
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 355
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 374
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 378
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 788
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 857
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ms-functions.php, line 2815
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-simplepie.php, line 736
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/rest-api/endpoints/class-wp-rest-pattern-directory-controller.php, line 125
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/misc.php, line 1347
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/misc.php, line 1451
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-pop3.php, line 190
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-comment-query.php, line 432
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-comment-query.php, line 999
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-site-query.php, line 339
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/upgrade.php, line 952
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Credit.php, line 101
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-network-query.php, line 248
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/file.php, line 518
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Restriction.php, line 101
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/import.php, line 143
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/bookmark.php, line 153
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Enclosure.php, line 271
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Source.php, line 73
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Item.php, line 116
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/PHPMailer/SMTP.php, line 640
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/PHPMailer/SMTP.php, line 648
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/default-constants.php, line 232
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/class-wp-community-events.php, line 315
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/class-wp-community-events.php, line 317
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/class-wp-plugins-list-table.php, line 951
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Cache/Memcache.php, line 99
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/rest-api/endpoints/class-wp-rest-attachments-controller.php, line 1002
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/SimplePie/Rating.php, line 92
Info: MD5 hash (used in md5) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2566
Info: SHA1 hash (used in sha1) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2567
Info: SHA1 hash (used in sha1) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 141
Info: SHA1 hash (used in sha1) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-session-tokens.php, line 74
Info: SHA1 hash (used in sha1) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2350
Info: md5 hash (used in hash_hmac) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/pluggable.php, line 2373
Info: md5 hash (used in hash_hmac) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/PHPMailer/SMTP.php, line 627
Info: md5 hash (used in hash_hmac) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 1669
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 1699
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/update-core.php, line 1120
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/update-core.php, line 1224
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/file.php, line 1258
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-admin/includes/class-core-upgrader.php, line 411
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/rest-api/endpoints/class-wp-rest-attachments-controller.php, line 1188
Info: MD5 hash (used in md5_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php, line 232
Info: sha1 hash (used in hash_hmac) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 664
Info: md5 hash (used in getHashdata) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 670
Info: sha1 hash (used in getHashdata) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 1673
Info: SHA1 hash (used in sha1_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [Medium] Use of Password Hash With Insufficient Computational Effort
Path: wordpress/wp-includes/ID3/getid3.php, line 1703
Info: SHA1 hash (used in sha1_file) is insecure. Consider changing it to a secure hashing algorithm.
✗ [High] File Inclusion
Path: wordpress/wp-includes/blocks.php, line 99
Info: Unsanitized input from data from a remote resource flows into _, where it is included dynamically. Allowing unvalidated user input to control files that are included dynamically in PHP can lead to malicious code execution.
✗ [High] File Inclusion
Path: wordpress/wp-includes/ID3/getid3.php, line 632
Info: Unsanitized input from data from a remote resource flows into _, where it is included dynamically. Allowing unvalidated user input to control files that are included dynamically in PHP can lead to malicious code execution.
✗ [High] File Inclusion
Path: wordpress/wp-admin/admin.php, line 291
Info: Unsanitized input from an HTTP parameter flows into _, where it is included dynamically. Allowing unvalidated user input to control files that are included dynamically in PHP can lead to malicious code execution.
✗ [High] File Inclusion
Path: wordpress/wp-admin/admin.php, line 293
Info: Unsanitized input from an HTTP parameter flows into _, where it is included dynamically. Allowing unvalidated user input to control files that are included dynamically in PHP can lead to malicious code execution.
✗ [High] File Inclusion
Path: wordpress/wp-admin/update.php, line 100
Info: Unsanitized input from an HTTP parameter flows into _, where it is included dynamically. Allowing unvalidated user input to control files that are included dynamically in PHP can lead to malicious code execution.
✗ [High] SQL Injection
Path: wordpress/wp-admin/includes/class-wp-list-table.php, line 617
Info: Unsanitized input from an HTTP parameter flows into prepare, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-admin/user-edit.php, line 108
Info: Unsanitized input from an HTTP parameter flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-admin/user-edit.php, line 159
Info: Unsanitized input from an HTTP parameter flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-includes/comment.php, line 1189
Info: Unsanitized input from an HTTP parameter flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-admin/setup-config.php, line 317
Info: Unsanitized input from an HTTP parameter flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-includes/comment.php, line 2933
Info: Unsanitized input from the database flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-includes/comment.php, line 3128
Info: Unsanitized input from the database flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] SQL Injection
Path: wordpress/wp-includes/comment.php, line 3129
Info: Unsanitized input from the database flows into query, where it is used in an SQL query. This may result in an SQL Injection vulnerability.
✗ [High] Server-Side Request Forgery (SSRF)
Path: wordpress/wp-admin/includes/class-file-upload-upgrader.php, line 128
Info: Unsanitized input from an HTTP parameter flows into unlink, where it is used as an URL to perform a request. This may result in a Server-Side Request Forgery vulnerability.
✗ [High] Server-Side Request Forgery (SSRF)
Path: wordpress/wp-includes/class-wp-image-editor-gd.php, line 98
Info: Unsanitized input from data from a remote resource flows into file_get_contents, where it is used as an URL to perform a request. This may result in a Server-Side Request Forgery vulnerability.
✗ [High] Path Traversal
Path: wordpress/wp-includes/class-wp-image-editor-gd.php, line 98
Info: Unsanitized input from data from a remote resource flows into file_get_contents, where it is used as a path. This may result in a Path Traversal vulnerability and allow an attacker to read arbitrary files.
✗ [High] Path Traversal
Path: wordpress/wp-admin/includes/class-file-upload-upgrader.php, line 128
Info: Unsanitized input from an HTTP parameter flows into unlink, where it is used as a path. This may result in a Path Traversal vulnerability and allow an attacker to delete arbitrary files.
✗ [High] Path Traversal
Path: wordpress/wp-includes/l10n.php, line 1169
Info: Unsanitized input from an HTTP parameter flows into file_get_contents, where it is used as a path. This may result in a Path Traversal vulnerability and allow an attacker to read arbitrary files.
✗ [High] Path Traversal
Path: wordpress/wp-includes/ms-files.php, line 87
Info: Unsanitized input from an HTTP parameter flows into readfile, where it is used as a path. This may result in a Path Traversal vulnerability and allow an attacker to read arbitrary files.
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-login.php, line 221
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/user-edit.php, line 584
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/rest-api/class-wp-rest-server.php, line 513
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-signup.php, line 116
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-signup.php, line 149
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-signup.php, line 261
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-signup.php, line 272
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-signup.php, line 278
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2075
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2346
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2414
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2592
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2608
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2740
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2832
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/media.php, line 2902
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/network/sites.php, line 388
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/class-wp-users-list-table.php, line 403
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/network/site-info.php, line 171
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/install.php, line 432
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/nav-menus.php, line 720
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/nav-menus.php, line 1006
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 621
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 654
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 656
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 673
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 695
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 700
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 766
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 847
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 860
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/plugin-install.php, line 872
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/theme-editor.php, line 285
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/async-upload.php, line 67
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/async-upload.php, line 72
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/async-upload.php, line 88
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/async-upload.php, line 98
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/async-upload.php, line 155
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/widgets-form.php, line 302
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/blocks/legacy-widget.php, line 119
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/load.php, line 1598
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/load.php, line 1605
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/authorize-application.php, line 140
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/network/upgrade.php, line 124
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/network/upgrade.php, line 128
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/comment-template.php, line 73
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/comment-template.php, line 254
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/comment-template.php, line 1028
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/comment-template.php, line 1974
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/comment-template.php, line 2704
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/plugins.php, line 641
Info: Unsanitized input from an HTTP parameter flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/includes/dashboard.php, line 1732
Info: Unsanitized input from an HTTP header flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/tinymce/wp-tinymce.php, line 38
Info: Unsanitized input from data from a remote resource flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/tinymce/wp-tinymce.php, line 41
Info: Unsanitized input from data from a remote resource flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/tinymce/wp-tinymce.php, line 42
Info: Unsanitized input from data from a remote resource flows into the echo statement, where it is used to render an HTML page returned to the user. This may result in a Cross-Site Scripting attack (XSS).
✗ [High] Regular Expression Denial of Service (ReDoS)
Path: wordpress/wp-includes/class-snoopy.php, line 322
Info: Unsanitized user input from an HTTP parameter flows into preg_match, where it is used to build a regular expression. This may result in a Regular expression Denial of Service attack (reDOS).
✗ [High] Regular Expression Denial of Service (ReDoS)
Path: wordpress/wp-includes/class-snoopy.php, line 389
Info: Unsanitized user input from an HTTP parameter flows into preg_match, where it is used to build a regular expression. This may result in a Regular expression Denial of Service attack (reDOS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/nav-menu.js, line 1354
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/plupload/handlers.js, line 90
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/plupload/handlers.js, line 207
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/plupload/handlers.js, line 221
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/site-health.js, line 168
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/image-edit.js, line 540
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/image-edit.js, line 549
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/image-edit.js, line 557
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/image-edit.js, line 627
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/inline-edit-post.js, line 443
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/dashboard.js, line 151
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/inline-edit-tax.js, line 232
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/post.js, line 239
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/post.js, line 1019
Info: Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-includes/js/plupload/handlers.js, line 135
Info: Unsanitized input from data from a remote resource flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/site-health.js, line 171
Info: Unsanitized input from data from a remote resource flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/image-edit.js, line 483
Info: Unsanitized input from data from a remote resource flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/post.js, line 68
Info: Unsanitized input from data from a remote resource flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/tags.js, line 138
Info: Unsanitized input from data from a remote resource flows into after, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/tags.js, line 155
Info: Unsanitized input from data from a remote resource flows into after, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/tags-box.js, line 315
Info: Unsanitized input from data from a remote resource flows into after, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/tags.js, line 141
Info: Unsanitized input from data from a remote resource flows into prepend, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/inline-edit-post.js, line 432
Info: Unsanitized input from data from a remote resource flows into before, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/inline-edit-tax.js, line 209
Info: Unsanitized input from data from a remote resource flows into before, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/updates.js, line 2540
Info: Unsanitized input from the document location flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/updates.js, line 2563
Info: Unsanitized input from the document location flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/updates.js, line 2649
Info: Unsanitized input from the document location flows into append, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Cross-site Scripting (XSS)
Path: wordpress/wp-admin/js/updates.js, line 2547
Info: Unsanitized input from the document location flows into prepend, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
✗ [High] Code Injection
Path: wordpress/wp-includes/js/customize-preview.js, line 859
Info: Unsanitized input from the document location flows into setInterval, where it is executed as JavaScript code. This may result in a Code Injection vulnerability.
✔ Test completed
Organization: undefined
Test type: Static code analysis
Project path: /Users/bezeklik/Workspace/snyk
263 Code issues found
105 [High] 157 [Medium] 1 [Low]
コード検査をしてみると、最新版なのにまさかの 263 件も検出されてしまう。
人気の PHP アプリケーションの脆弱性を検査する
GitHub のリポジトリ一覧取得
検査対象の検討のために GitHub Search API を使って PHP で書かれたリポジトリの一覧をスター数の多い順に50件ほど取得してみます。
GITHUB_API=https://api.github.com/search/repositories
LANGUAGE=php
KEYWORD=''
STARS=10000
curl --silent \
--header "Accept: application/vnd.github.v3+json" \
"${GITHUB_API}?q=${KEYWORD}+in:name,description,readme+language:${LANGUAGE}+stars:>=${STARS}&sort=stars&order=desc&per_page=50" \
| jq --raw-output '.items[] | [.full_name, .html_url, .language // "-", .stargazers_count] | @tsv' \
| awk '{printf("|%d|[%s](%s)|%s|%'"'"'d|\n", NR, $1, $2, $3, $4)}'
GITHUB_API=https://api.github.com/search/repositories
LANGUAGE=php
KEYWORD=cms
STARS=900
curl --silent \
--header "Accept: application/vnd.github.v3+json" \
"${GITHUB_API}?q=${KEYWORD}+in:name,description,readme+language:${LANGUAGE}+stars:>=${STARS}&sort=stars&order=desc&per_page=50" \
| jq --raw-output '.items[] | [.full_name, .html_url, .language // "-", .stargazers_count] | @tsv' \
| awk '{printf("|%d|[%s](%s)|%s|%'"'"'d|\n", NR, $1, $2, $3, $4)}'