概要
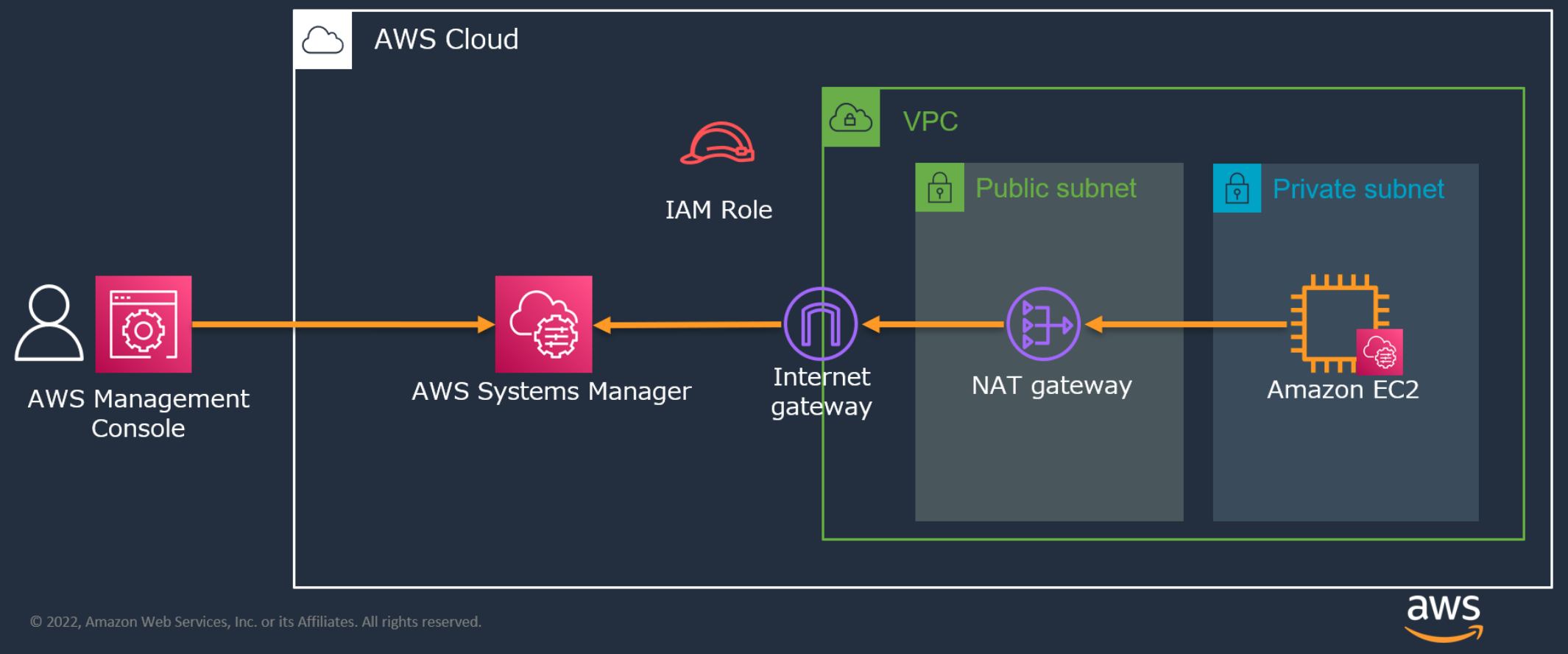
AWS Systems Managerを使ってPrivate subnetにあるEC2にリモート接続をしてみた
マネージドインスタンスにする3つのSTEP
※ セミナーの資料を引用しています
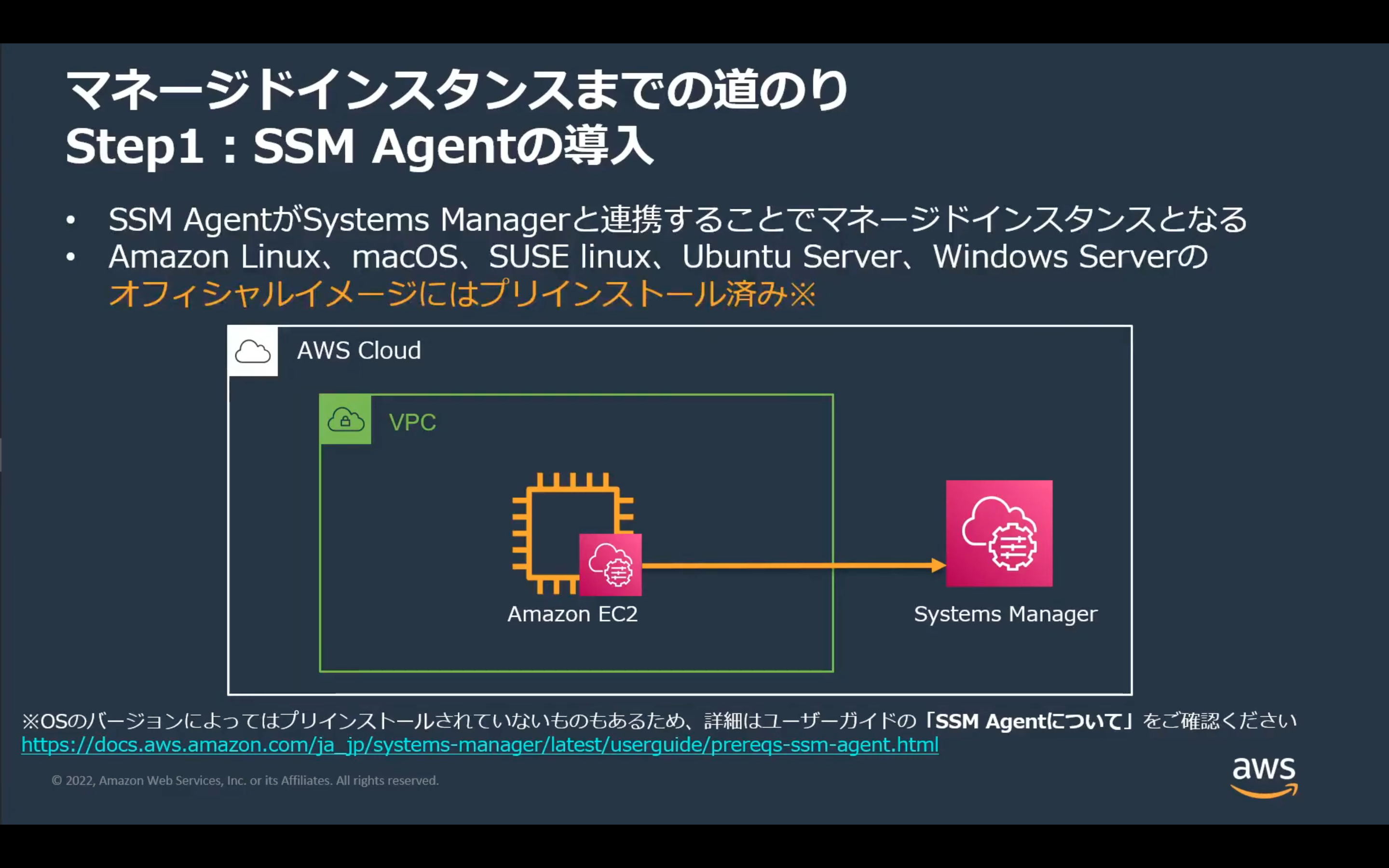
STEP1 SSM Agentの導入
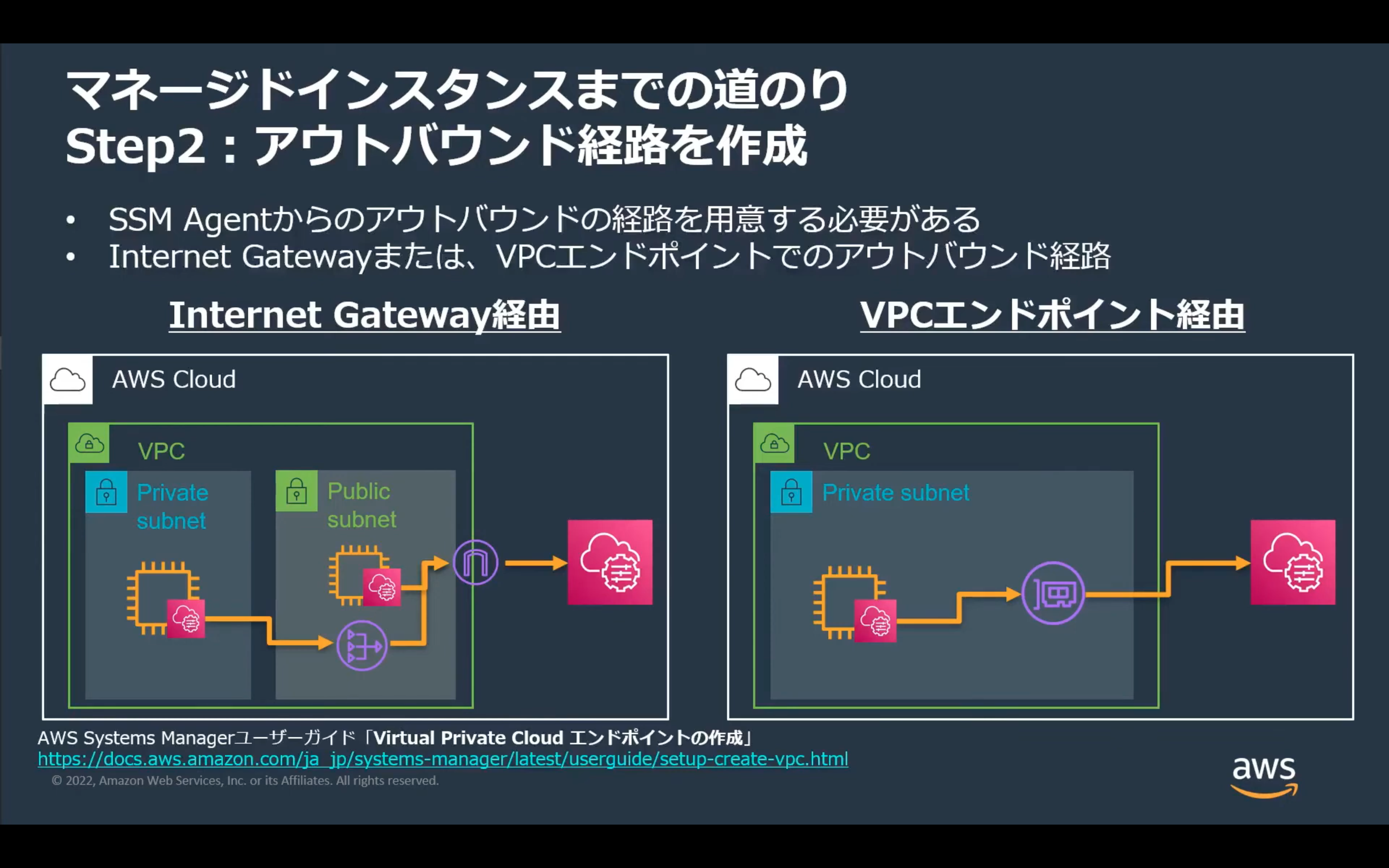
STEP2 アウトバウンド経路を作成
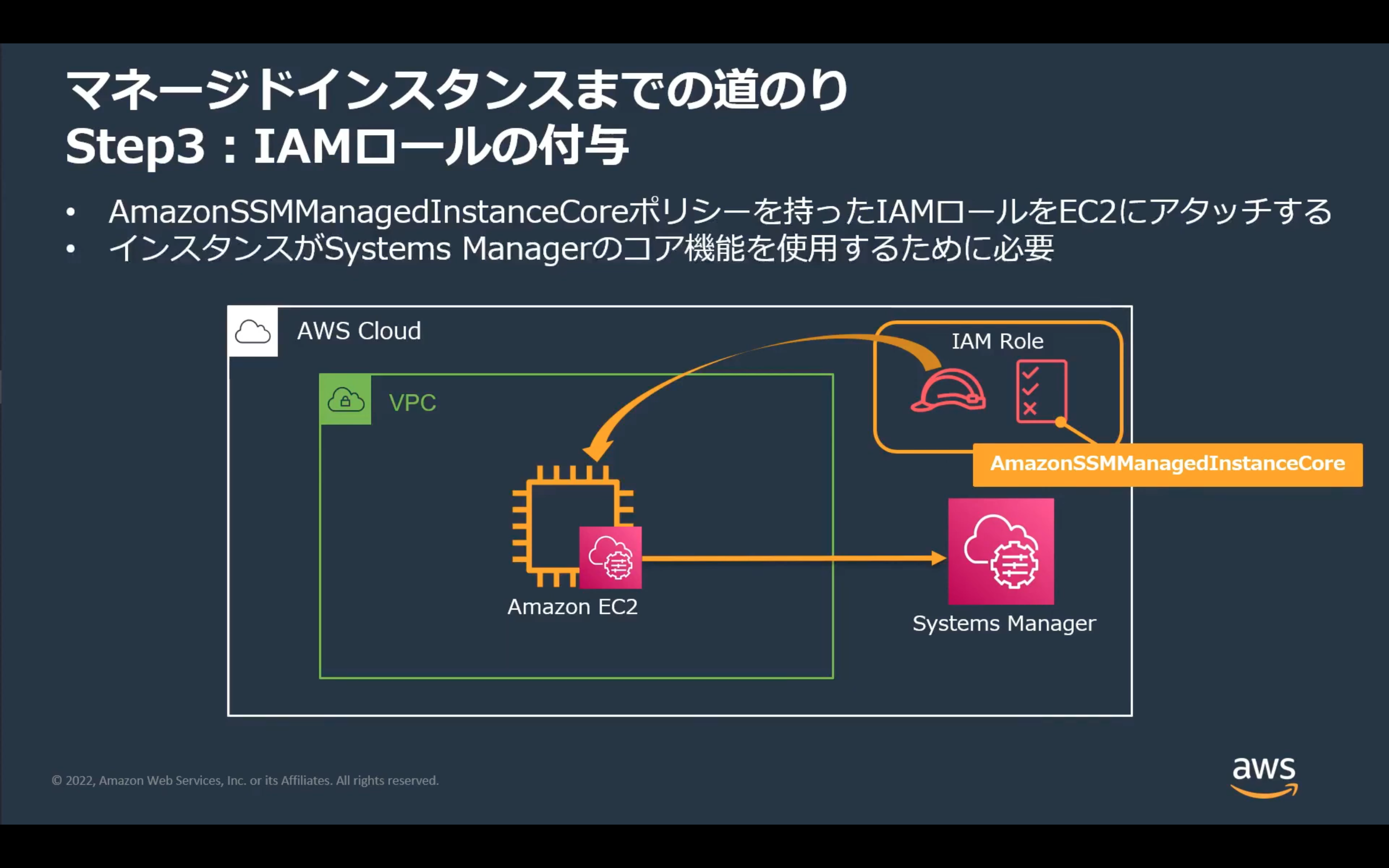
STEP3 IAMロールの付与
CloudFormation
※セミナーの内容と完全に一致していません
AWSTemplateFormatVersion: "2010-09-09"
Description: "This template is for 'AWS Hands-on for Beginners Systems Manager Hands-on'."
Parameters:
VPCCidr:
Type: "String"
Default: "10.0.0.0/16"
Description: "VPCCidr"
PublicSubnetCidr:
Type: "String"
Default: "10.0.0.0/24"
Description: "PublicSubnetCidr"
PrivateSubnetCidr:
Type: "String"
Default: "10.0.1.0/24"
Description: "PrivateSubnetCidr"
Resources:
VPC:
Type: "AWS::EC2::VPC"
Properties:
CidrBlock:
Ref: "VPCCidr"
EnableDnsSupport: "true"
EnableDnsHostnames: "true"
Tags:
- Key: "Name"
Value: "h4b-vpc"
PublicSubnet:
Type: "AWS::EC2::Subnet"
Properties:
VpcId:
Ref: "VPC"
CidrBlock:
Ref: "PublicSubnetCidr"
AvailabilityZone:
Fn::Select:
- "0"
-
Fn::GetAZs:
Ref: "AWS::Region"
MapPublicIpOnLaunch: "true"
Tags:
- Key: "Name"
Value: "h4b-public-subnet"
PrivateSubnet:
Type: "AWS::EC2::Subnet"
Properties:
VpcId:
Ref: "VPC"
CidrBlock:
Ref: "PrivateSubnetCidr"
AvailabilityZone:
Fn::Select:
- "1"
-
Fn::GetAZs:
Ref: "AWS::Region"
Tags:
- Key: "Name"
Value: "h4b-private-subnet"
EIP:
Type: "AWS::EC2::EIP"
Properties:
Tags:
- Key: "Name"
Value: "h4b-eip"
InternetGateway:
Type: "AWS::EC2::InternetGateway"
Properties:
Tags:
- Key: "Name"
Value: "h4b-igw"
AttachGateway:
Type: "AWS::EC2::VPCGatewayAttachment"
Properties:
VpcId:
Ref: "VPC"
InternetGatewayId:
Ref: "InternetGateway"
NATGateway:
Type: "AWS::EC2::NatGateway"
Properties:
AllocationId:
Fn::GetAtt:
- "EIP"
- "AllocationId"
ConnectivityType: "public"
SubnetId:
Ref: "PublicSubnet"
RouteTableforPublic:
Type: "AWS::EC2::RouteTable"
Properties:
VpcId:
Ref: "VPC"
Tags:
- Key: "Name"
Value: "h4b-public-route-table"
RouteTableforPrivate:
Type: "AWS::EC2::RouteTable"
Properties:
VpcId:
Ref: "VPC"
Tags:
- Key: "Name"
Value: "h4b-private-route-table"
RouteForPublic:
Type: "AWS::EC2::Route"
DependsOn: "AttachGateway"
Properties:
RouteTableId:
Ref: "RouteTableforPublic"
DestinationCidrBlock: "0.0.0.0/0"
GatewayId:
Ref: "InternetGateway"
RouteForPrivate:
Type: "AWS::EC2::Route"
DependsOn: "NATGateway"
Properties:
RouteTableId:
Ref: "RouteTableforPrivate"
DestinationCidrBlock: "0.0.0.0/0"
NatGatewayId:
Ref: "NATGateway"
SubnetRouteTableAssociation1:
Type: "AWS::EC2::SubnetRouteTableAssociation"
Properties:
SubnetId:
Ref: "PublicSubnet"
RouteTableId:
Ref: "RouteTableforPublic"
SubnetRouteTableAssociation2:
Type: "AWS::EC2::SubnetRouteTableAssociation"
Properties:
SubnetId:
Ref: "PrivateSubnet"
RouteTableId:
Ref: "RouteTableforPrivate"
EC2SecurityGroup:
Type: "AWS::EC2::SecurityGroup"
Properties:
VpcId:
Ref: "VPC"
GroupDescription: "No Inbound Rule Security Group"
GroupName: "h4b-ec2-sg"
Tags:
- Key: "Name"
Value: "h4b-ec2-sg"
Instance:
Type: AWS::EC2::Instance
Properties:
ImageId: ami-0bdd30a3e20da30a1
SecurityGroupIds:
- !Ref EC2SecurityGroup
AvailabilityZone:
Fn::Select:
- "1"
-
Fn::GetAZs:
Ref: "AWS::Region"
IamInstanceProfile: !Ref InstanceProfile
InstanceType: t2.micro
SubnetId: !Ref PrivateSubnet
Tags:
- Key: Name
Value: h4b-instance
InstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
Roles:
- !Ref EC2SSMRole
EC2SSMRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Statement:
- Action: 'sts:AssumeRole'
Effect: Allow
Principal:
Service: ec2.amazonaws.com
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore