About Publication
- "Dan Kaminsky's DNS Discovery" @ BlackHat 2008
- "Per Request IPv6 Addresses"
What You Would Learn
- Kaminsky Attack
- Attack Impact on the IPv6 host network
Kaminsky Attack
-
Dan Kaminsky discovers a serious vulnerability in DNS
-
This vulnerability leads clients to fake servers that the attacker chose
[for beginners] DNS (Domain Name System)
- DNS is a phone book for the Internet
- DNS Server serves delegation service system
[for beginners] DNS Cache
- Caching address resolutions saves time and mitigates traffic overload
DNS Cache Poisoning
- a type of attack that exploits DNS
- An attacker registers a fake DNS server as an authorized one in a DNS cache server
- The DNS cache server returns an incorrect IP address for the client query
DNS Cache Poisoning mechanism
- QID (Query ID) is 16-bit field
- 65534 (2^16) is not big number
Limited damage of DNS Cache Poisoning Attack
- An attacker hijacks a client access only when he/she can snoop his/her queries
- DNS Cache will expire after a while
Kaminsky Attack is more Powerful
- unlimited damage
- An attacker hijacks a DNS cache server without clients' queries
- independent of time expiration
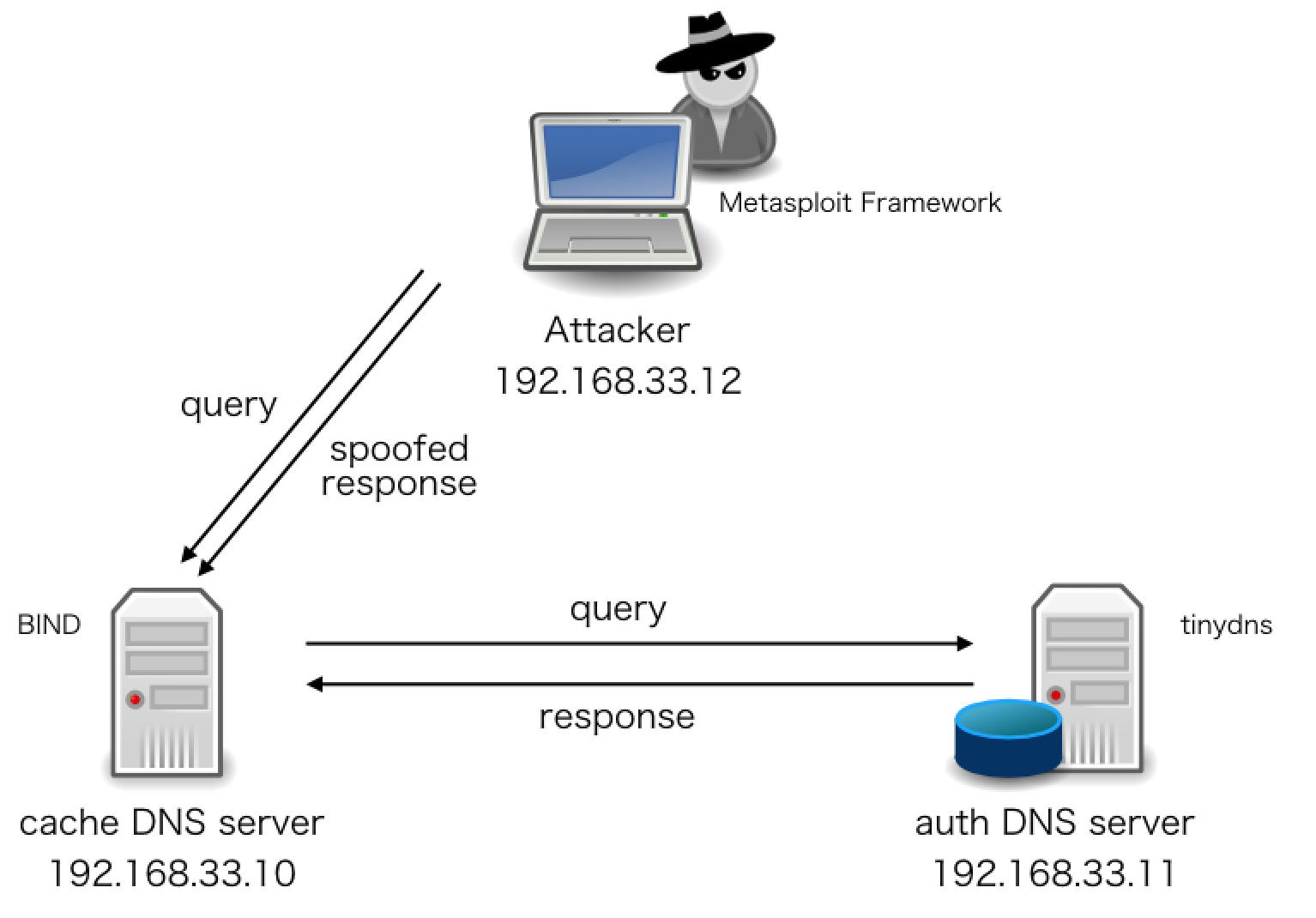
Kaminsky Attack mechanism
- An attacker asks to resolve a fake address to the DNS cache server
- The DNS cache server asks the fake query to the authorized DNS server
- An attacker sends a fake response from his DNS server before the one from the authorized DNS server
- Condition: QID in the attacker's response must be same with the authorized one
- The DNS cache server gains the fake response and overwrites the authorized DNS server
Patches
- Source port randomization
- don't use fixed QID
- QID extension field from 16-bit to 32-bit
- network monitoring
- provision the intensive DNS response
Ultimate solution
DNSSEC (Domain Name System Security Extensions)
BUT DNSSEC is not coming soon :(
Kaminsky Attack Damage on the IPv6 network
Q1. Bigger, smaller or same impact compared to the IPv4 network?
Q2. Why?
Q3. How to solve this attack?
[for beginners] IPv4 and IPv6
IPv4
- Internet Protocol version 4
- 32bit address long
- decimal representation (e.g., 8.8.8.8)
IPv6
- Internet Protocol version 6
- 128bit address long
- hexadecimal representation (e.g., 2001:4860:4860::8888)
[for beginners] Which IP version is popular?
-
Answer: IPv4
-
BUT impending shortage of IPv4 address space
- 4.29 billion (2^32) is not large address space for us
-
using IPv6 is getting popular for data center network service
- e.g., facebook, Google
[for beginners] Similarity and Difference between IPv4 and IPv6
- In most aspect, the IPv6 protocol is very similar to IPv4
- However, in some design and operational area, there is difference => address assignment policy
Address Assignment Policy
- IPv4 - a single IP address per devices
- IPv6 - multiple IP addresses per devices
Benefits having multiple IP addresses
-
client perspective
- app performance with multi-core CPU
- running virtual machines on a device
- no NAT
-
business perspective
- operational challenge
- network architecture challenge
IPv4 Address Assinment Options
- use DHCP (Dynamic Host Configuration Protocol)
- DHCP automatically provides a host with its IP address and other related configuration information
- configure an IP address manually
IPv6 Address assignment Options
- use RA (Routing Advertisement)
- RA tells a host routing path
- use RA + DHCPv6
- use DHCPv6
- configure an IP address manually
Why You need to understand address assignment options?
- because DNS servers' info is conveyed with an IPv4/IPv6 address
4-step for IPv4 Address Assignment using DHCP
- DHCP Discover
- Client Host: "Is any DHCP server here? Give me an IP address."
- DHCP Offer
- DHCP Server: "Yes, I am here. How about this IP address? If you use this address, these relative info can be used."
- DHCP Request
- Client Host: "Thanks! I gonna use this address and relative info."
- DHCP Ack
IPv6 Addressing Overview
- A prefix and a subnet IDs are given either by RA or by DHCPv6
- An interface ID is either given by DHCPv6 or generated by a host
How to get DNS servers info with IPv6
- RA or DHCPv6 conveys DNS info
- A host can select which timing it receives DNS server info.
Again, Kaminsky Attack Damage on the IPv6 network
Q1. Bigger or smaller impact compared to the IPv4 network?
Q2. Why?
Q3. How to solve this attack?
Discussions @ coffee with science meetup
Reference
- http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html
- https://www.nic.ad.jp/ja/newsletter/No40/0800.html
- https://tools.ietf.org/html/draft-vixie-dnsext-dns0x20-00
- https://tools.ietf.org/html/rfc7934
- https://tools.ietf.org/html/rfc8106
- multiple images copied through google image search results