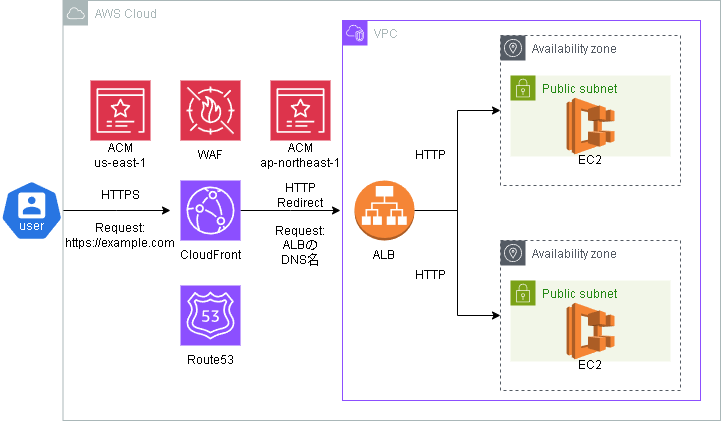
はじめに
Terraformを学習したかったのでAWSで一般的なWebサーバのコードを作成してみました。
構成
今回はVPC、EC2、ALB
VPC
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "test-vpc"
}
}
resource "aws_subnet" "public1" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.0.0/24"
availability_zone = "ap-northeast-1a"
map_public_ip_on_launch = true
tags = {
Name = "PublicSubnet1"
}
}
resource "aws_subnet" "public2" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.1.0/24"
availability_zone = "ap-northeast-1c"
map_public_ip_on_launch = true
tags = {
Name = "PublicSubnet2"
}
}
resource "aws_subnet" "private1" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.10.0/24"
availability_zone = "ap-northeast-1a"
tags = {
Name = "PrivateSubnet1"
}
}
resource "aws_subnet" "private2" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.11.0/24"
availability_zone = "ap-northeast-1c"
tags = {
Name = "PrivateSubnet2"
}
}
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.main.id
tags = {
Name = "test-igw"
}
}
resource "aws_route_table" "rt" {
vpc_id = aws_vpc.main.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "test-public-rt"
}
}
resource "aws_route_table_association" "pub_1a_association" {
subnet_id = aws_subnet.public1.id
route_table_id = aws_route_table.rt.id
}
resource "aws_route_table_association" "pub_1c_association" {
subnet_id = aws_subnet.public2.id
route_table_id = aws_route_table.rt.id
}
EC2
data "aws_ami" "latest_amazon_linux" {
owners = ["amazon"]
most_recent = true
filter {
name = "name"
values = ["amzn2-ami-hvm-*-x86_64-gp2"]
}
}
# EC2インスタンス1a
resource "aws_instance" "instance1" {
ami = data.aws_ami.latest_amazon_linux.id
instance_type = "t2.micro"
subnet_id = aws_subnet.public1.id
user_data = <<-EOF
#!/bin/bash
sudo amazon-linux-extras install nginx1 -y
sudo systemctl start nginx
sudo systemctl enable nginx
echo "<html><body>OK</body></html>" | sudo tee /usr/share/nginx/html/health
EOF
vpc_security_group_ids = [aws_security_group.ec2_sg.id]
tags = {
Name = "EC2Instance1A"
}
depends_on = [aws_security_group.ec2_sg]
}
resource "aws_instance" "instance2" {
ami = data.aws_ami.latest_amazon_linux.id
instance_type = "t2.micro"
subnet_id = aws_subnet.public2.id
user_data = <<-EOF
#!/bin/bash
sudo amazon-linux-extras install nginx1 -y
sudo systemctl start nginx
sudo systemctl enable nginx
echo "<html><body>OK</body></html>" | sudo tee /usr/share/nginx/html/health
EOF
vpc_security_group_ids = [aws_security_group.ec2_sg.id]
tags = {
Name = "EC2Instance1C"
}
depends_on = [aws_security_group.ec2_sg]
}
resource "aws_security_group" "ec2_sg" {
name = "ec2_sg"
description = "Allow HTTP and SSH"
vpc_id = aws_vpc.main.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["10.0.0.0/16"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["3.112.23.0/29"] # Instance Connect
}
egress {
from_port = 0
to_port = 0
protocol = "-1" # 全トラフィック
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "ec2_sg"
}
}
ALB
- 今回はHTTP通信のみ許可しています。CloudFrontとRoute53を作成した後リスナーとSGを変更します。
resource "aws_lb" "alb" {
name = "MyLoadBalancer"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.alb_sg.id]
subnets = [
aws_subnet.public1.id,
aws_subnet.public2.id
]
enable_deletion_protection = false
}
resource "aws_lb_listener" "listener" {
load_balancer_arn = aws_lb.alb.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.lb_tg.arn
}
}
resource "aws_lb_target_group" "lb_tg" {
name = "test-lb-tg"
port = 80
protocol = "HTTP"
vpc_id = aws_vpc.main.id
health_check {
path = "/health"
}
}
resource "aws_lb_target_group_attachment" "instance1" {
target_group_arn = aws_lb_target_group.lb_tg.arn
target_id = aws_instance.instance1.id
port = 80
}
resource "aws_lb_target_group_attachment" "instance2" {
target_group_arn = aws_lb_target_group.lb_tg.arn
target_id = aws_instance.instance2.id
port = 80
}
resource "aws_security_group" "alb_sg" {
name = "alb-sg"
description = "Allow HTTP and SSH"
vpc_id = aws_vpc.main.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
}
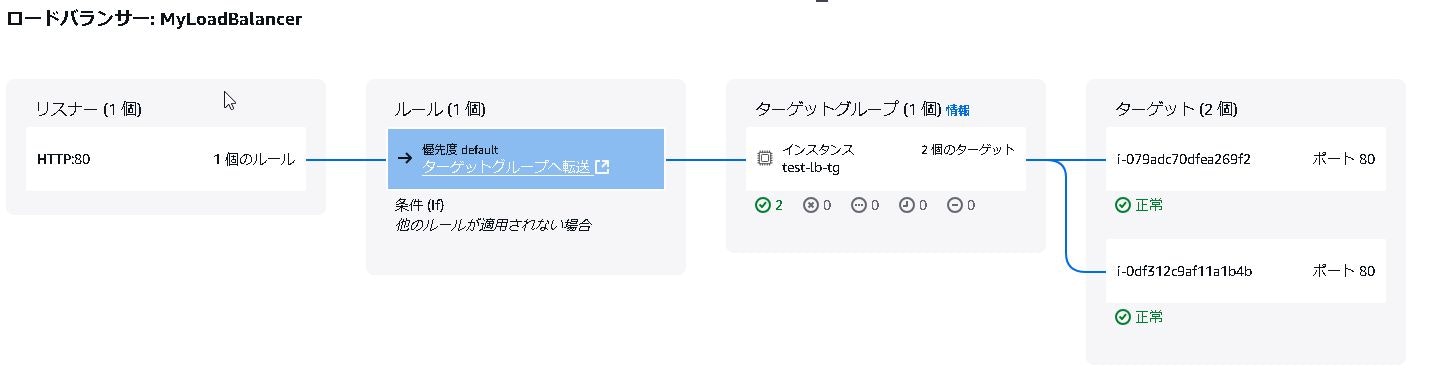
結果
C:\terraform>curl http://MyLoadBalancer-2077151388.ap-northeast-1.elb.amazonaws.com
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
・
・
・
さいごに
CloudFormationではスタック間の依存関係を処理する手間が煩雑に感じられましたが、Terraformではリソース間の依存関係が自動的に解決される仕組みがあるため、コードを書く際にスムーズで効率的だと感じました。