概要
HackThebox:Preignitionのflagを入手する手順を記す。
Port Scan
$ nmap -A -sV -v preignition.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-13 22:11 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:11
Completed NSE at 22:11, 0.00s elapsed
Initiating NSE at 22:11
Completed NSE at 22:11, 0.00s elapsed
Initiating NSE at 22:11
Completed NSE at 22:11, 0.00s elapsed
Initiating Ping Scan at 22:11
Scanning preignition.htb (10.129.194.18) [2 ports]
Completed Ping Scan at 22:11, 0.25s elapsed (1 total hosts)
Initiating Connect Scan at 22:11
Scanning preignition.htb (10.129.194.18) [1000 ports]
Discovered open port 80/tcp on 10.129.194.18
Increasing send delay for 10.129.194.18 from 0 to 5 due to max_successful_tryno increase to 4
Increasing send delay for 10.129.194.18 from 5 to 10 due to max_successful_tryno increase to 5
Completed Connect Scan at 22:11, 35.72s elapsed (1000 total ports)
Initiating Service scan at 22:11
Scanning 1 service on preignition.htb (10.129.194.18)
Completed Service scan at 22:12, 6.52s elapsed (1 service on 1 host)
NSE: Script scanning 10.129.194.18.
Initiating NSE at 22:12
Completed NSE at 22:12, 5.74s elapsed
Initiating NSE at 22:12
Completed NSE at 22:12, 1.00s elapsed
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Nmap scan report for preignition.htb (10.129.194.18)
Host is up (0.25s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
NSE: Script Post-scanning.
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Initiating NSE at 22:12
Completed NSE at 22:12, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.62 seconds
Webサーバーが提供されていることが分かる。
gobuster
http://preignition.htb に対してgobusterでディレクトリ探索を行う。
$ gobuster dir -u http://preignition.htb -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://preignition.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/09/13 22:19:19 Starting gobuster in directory enumeration mode
===============================================================
/admin.php (Status: 200) [Size: 999]
===============================================================
2022/09/13 22:21:17 Finished
===============================================================
admin.phpを見つけたのでアクセスしてみる。
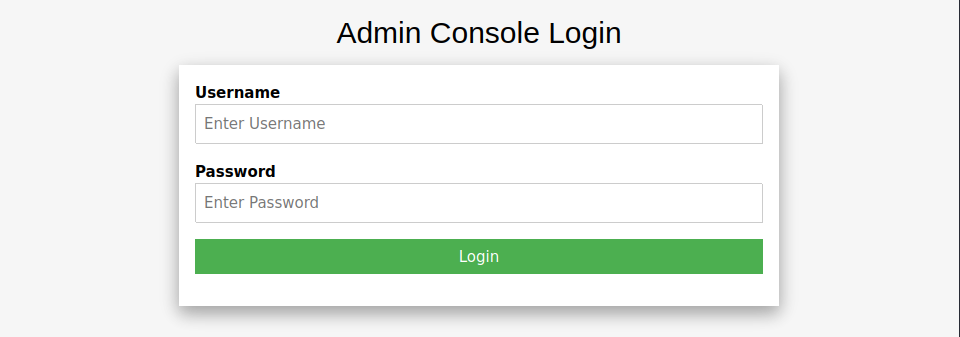
admin.php
とりあえず、admin/root/passwordなどの単語を入力してみる。
結果的にadmin:adminでログインできることが分かる。
ログインに成功するとページにflagが表示される。
以上。