AWSリージョン間接続 BGP
VyOSでリージョン間のVPNを構築。
単一構成であればスタティックルートで良いですが、冗長構成も考えBGPの構成を実装。
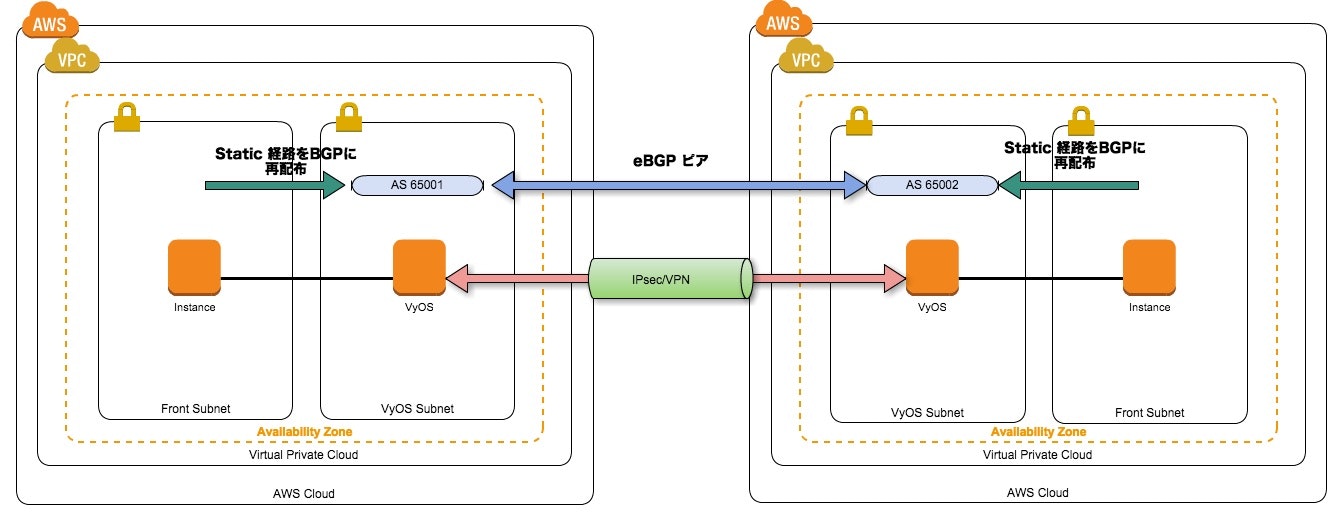
構成図
ルーティング
- 拠点間をeBGPにてピア接続を行う。
- Front SubnetのネットワークはStatic経路をBGPに再配布することによって経路公告を行う
- BGPTimerは[Hello:4秒][Dead:12秒]とし検知12秒 切替1秒 (短くしすぎたらピアDownが頻発したのでこのぐらいがちょうどいいかと)
- Routemapを付与しない場合バグが発生したので設定している
- MTUは1414
- IPSec/GREでトンネルを構築
AWS設定
・AmazonLinux 最新版のAMI
→RoutingTableに「対向のネットワーク:VyOSのENI」を設定する
・VyOS コミュニティAMIの最新版(Version 1.1.0)
→source dest checkを無効にする
→EIPを付与する
・セキュリティグループ
→対向のEIP宛の通信を許可しておく
Config
set system host-name [hostname]
set vpn ipsec ipsec-interfaces interface [if:eth0]
set vpn ipsec ike-group ike lifetime 3600
set vpn ipsec ike-group ike proposal 1 encryption aes128
set vpn ipsec ike-group ike proposal 1 hash sha1
set vpn ipsec esp-group esp lifetime 1800
set vpn ipsec esp-group esp proposal 1 encryption aes128
set vpn ipsec esp-group esp proposal 1 hash sha1
set vpn ipsec site-to-site peer [対向EIP] authentication mode pre-shared-secret
set vpn ipsec site-to-site peer [対向EIP] authentication pre-shared-secret [パスワード文字列]
set vpn ipsec site-to-site peer [対向EIP] authentication id [自身のID]
set vpn ipsec site-to-site peer [対向EIP] authentication remote-id [対向のID]
set vpn ipsec site-to-site peer [対向EIP] default-esp-group esp
set vpn ipsec site-to-site peer [対向EIP] ike-group ike
set vpn ipsec site-to-site peer [対向EIP] local-address [ローカルIP]
set vpn ipsec site-to-site peer [対向EIP] tunnel 1 local prefix [LoopbackIP]
set vpn ipsec site-to-site peer [対向EIP] tunnel 1 remote prefix [対向LoopbackIP]
set interfaces loopback lo address [LoopbackIP]
set interfaces tunnel tun0 address [VPN用アドレス/30]
set interfaces tunnel tun0 local-ip [LoopbackIP]
set interfaces tunnel tun0 remote-ip [対向LoopbackIP]
set interfaces tunnel tun0 mtu 1414
set interfaces tunnel tun0 encapsulation gre
set protocols bgp [自AS番号] neighbor [対向VPN用アドレス/30] remote-as 65001
set protocols bgp [自AS番号] neighbor [対向VPN用アドレス/30] soft-reconfiguration inbound
set protocols bgp [自AS番号] neighbor [対向VPN用アドレス/30] update-source tun0
set protocols bgp [自AS番号] network [VPN用ネットワークアドレス/30]
set protocols bgp [自AS番号] network [LoopbackIP]
set protocols bgp [自AS番号] timers holdtime 12
set protocols bgp [自AS番号] timers keepalive 4
set protocols bgp [自AS番号] parameters log-neighbor-changes
set policy prefix-list prefix-connect-to-bgp rule 10 action permit
set policy prefix-list prefix-connect-to-bgp rule 10 prefix [VyOS Subnet]
set policy route-map routemap-connect-to-bgp rule 1 action permit
set policy route-map routemap-connect-to-bgp rule 1 match ip address prefix-list prefix-connect-to-bgp
set protocols bgp [自AS番号] network [VyOS Subnet] route-map routemap-connect-to-bgp
set policy prefix-list prefix-static-to-bgp rule 10 action permit
set policy prefix-list prefix-static-to-bgp rule 10 prefix [Front Subnet]
set policy route-map routemap-static-to-bgp rule 1 action permit
set policy route-map routemap-static-to-bgp rule 1 match ip address prefix-list prefix-static-to-bgp
set protocols bgp [自AS番号] redistribute static route-map routemap-static-to-bgp
set protocols static route [Front Subnet] next-hop [AWS DefaultGW]
etc...
今回は冗長構成を踏まえた設定となるため、冗長構成パターンは別途記載予定。