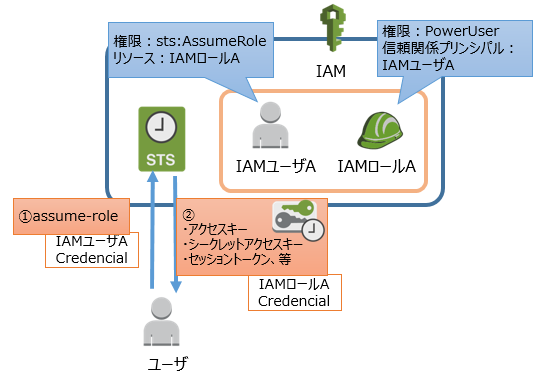
概要
同じアカウント内でAssumeRoleだけ出来るIAMユーザを払い出す。
AssumeRoleだけ許可されたIAMユーザクレデンシャルを保持するユーザがAssumeRoleを行い、関連付けられたIAMロールでリソースを触れるようにする
イメージ図
手順例
IAM関連リソース作成
IAMユーザ作成
- ARN
- arn:aws:iam::xxxxx:user/assume-test-user
- アクセス許可のポリシー
- 作成予定のRoleのみにAssueRoleを許可
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sts:AssumeRole"
],
"Effect": "Allow",
"Resource": [
"arn:aws:iam::xxxxxx:role/assume-role-test"
]
}
]
}
IAMロール作成
- ロールARN
- arn:aws:iam::xxxxx:role/assume-role-test
- アクセス許可のポリシー
- 任意だがとりあえずPowerUser
- 信頼関係
- プリンシパルには上記のIAMユーザを指定
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::xxxxxx:user/assume-test-user"
},
"Action": "sts:AssumeRole"
}
]
}
使い方
前提
- IAMユーザのクレデンシャルを登録済の環境であること
手順
# aws sts assume-role --role-arn arn:aws:iam::xxxxx:role/assume-role-test --role-session-name zzzzz(任意)
★アクセスキー、シークレットアクセスキー、セッショントークンを控える
# export AWS_ACCESS_KEY_ID = xxxx
# export AWS_SECRET_ACCESS_KEY= xxxx
# export AWS_SESSION_TOKEN= xxx
★あとはExpireするまで自由に
# aws ec2 describe-instances
参考
AWS CLIでAssumeRole http://www.slideshare.net/tetsunorinishizawa/aws-cliassume-role