This slide was used in AVTOKYO 2016
2016/10/22 @ Tokyo
Abount Me
- Kota Kanbe (Twitter, GitHub, [Facebook] (https://www.facebook.com/kota.kanbe) )
- Programmer @ Future architect, Inc. Japan
- Author of Vuls
- Owner of Mohikan Slack
Balse?
Vuls (VULnerability Scanner)
- Vulnerability scanner for Linux/FreeBSD, agentless, written in Go
- Not Web penetration scanner
- GitHub Vuls
What's Vuls
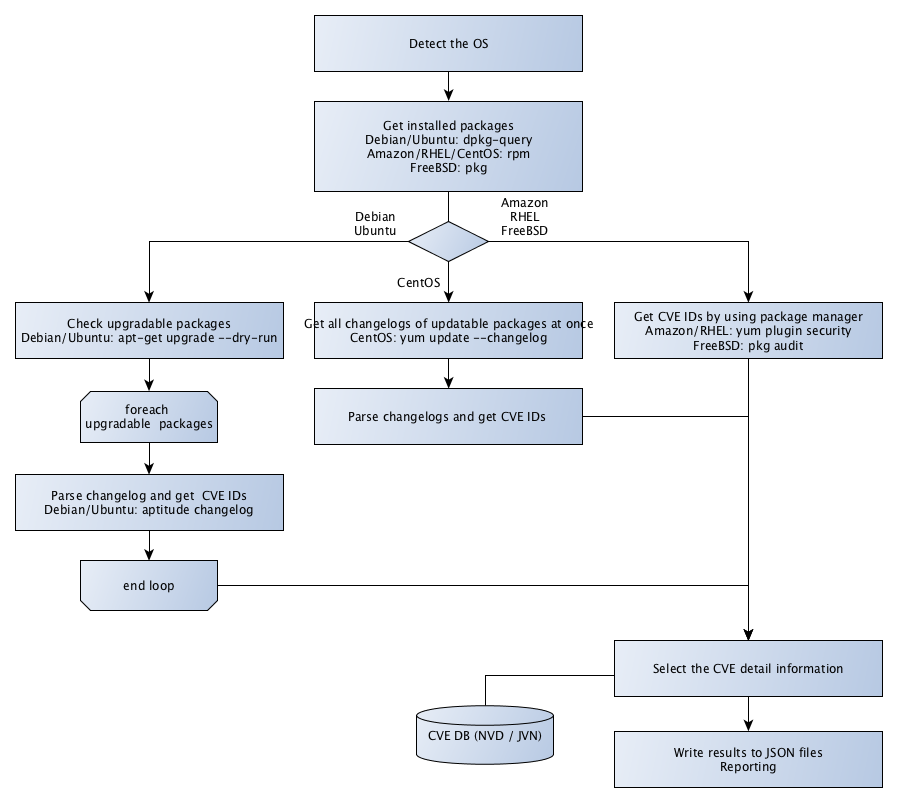
Architecture
Scan Flow
Why parsing a changelog
- Ubuntu, Debian, CentOS
locales 2.13+git20120306-21
login 1:4.1.5.1-1.1ubuntu7
lsb-base 9.20160110
make 4.1-6
mawk 1.3.3-17ubuntu2
mime-support 3.59ubuntu1
multiarch-support 2.21-0ubuntu5
Features
- Scan for any vulnerabilities in Linux/FreeBSD Server
- Supports Ubuntu, Debian, CentOS, Amazon Linux, RHEL, FreeBSD
- Cloud, on-premise, Docker
- Scan middleware that are not included in OS package management
- Scan N/W Devices, middleware, programming language libraries and framework for vulnerability
- Support software registered in CPE
- Agentless architecture
- User is required to only setup one machine that is connected to other target servers via SSH
- Nondestructive testing
- Pre-authorization is not necessary before scanning on AWS
- Email and Slack notification are both available. (supports Japanese language)
- Scan result is viewable on accessory software, TUI Viewer terminal or Web UI (VulsRepo).
Support OS
| Distribution | Release |
|---|---|
| Ubuntu | 12, 14, 16 |
| Debian | 7, 8 |
| RHEL | 6, 7 |
| CentOS | 5, 6, 7 |
| Amazon Linux | All |
| FreeBSD | 10 |
Configuration
Demo
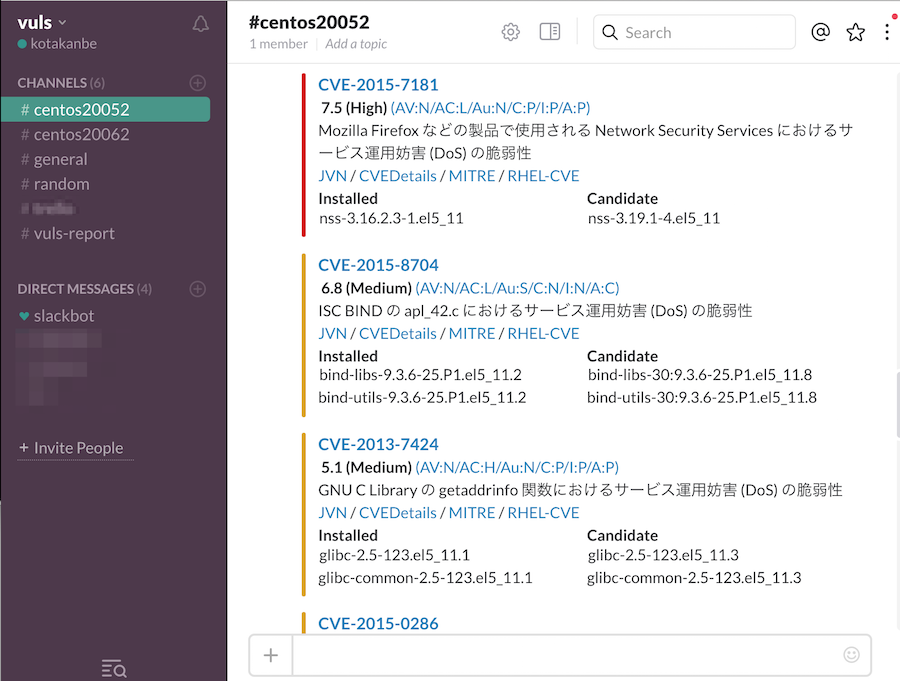
Reporting / Slack
Web UI / usiusi360/vulsrepo
Why I Created Vuls
- I managed over 100 Linux servers for several years.
- Vulnerability management and software update task is too much of a hassle.
- System administrator will have to constantly watch out for any new vulnerabilities in NVD or JVN.
- It is expensive to perform analysis to determine the servers affected by new vulnerabilities.
- Everyday ...
Why I Published Vuls To GitHub
- I traveled India and Nepal for 1 month.
- I tried training at Japanese Temple near birthplace of the buddha for a week.
- Morning training
- An old monk thinks about peace of the world from the heart.
- I thought what can I do for peace of the world
- .....
- OSS!
For Peace Of The World
Buzzed All Over The World

Got First Place In GitHub Trending
Pull Request-Driven Development
Total 159 P/R (2016/10/19)
- FreeBSD Support by justyntemme #90
- High Speed Scaning on CentOS by ti-ga #138
- High speed data fetch from JVN by kotakanbe #21
- High speed scanning on Ubuntu(20x Faster on Ubuntu, 4x Faster on Debian) by kotakanbe #172
Recent Changes
- Setup Vuls using DockerHub by matsuno #223
- Support ignore CveIDs in config #222
- Confirm before installing dependencies on prepare #219
- Remove all.json #218
- Improve makefile, -version shows git hash, fix README #216
- change e-mail package from gomail to net/smtp by by matsuno #211
- Add only-containers option to scan subcommand #122 #190
Community
- 217 Members (#general)
- 120 Members (#vulsjp)

VulsMatsuri #1
- 2016/9/26 about 100 people
- Slides
Links
What I'm Working On
- CPE auto-detection of programming language library
- Vuls is possible to detect vulnerabilities in non-OS packages
- I'm planning to integrate with OWASP Dependency Check
- I'm going to talk more details at Security-JAWS #3 10/28
I'm Here To Talk With Hacker
-
For now, root privilege is needed to scan RHEL, Ubuntu, Debian and CentOS. Do you know how to detect the vulnerabilities(CVE-ID) without root privilege on these OSes?(FreeBSD and Amazon Linux do not require root privilege for this)
-
Miss Detection on Ubuntu, Debian, CentOS
- Vuls parses a changelog of upgradable packages. If the CVE-ID is written in irregular format, Vuls can't detect the CVE-IDs. Do you know how to detect the CVE-ID without parsing the changelog?
-
I am planning to integrate with other security scanner, something like OWASP-dependency-check, lynis, wpscan or ssh-audit. Please teach me other scanner that you recommend.
-
Windows support
We Are Hiring Hacker And Engineer!
If you are interested, please contact me ( Twitter: @kotakanbe )
Thanks
Give a GitHub Star if you are interested :)