This slide was used in Security-JAWS 【第3回】2016年10月28日(金)
2016/10/28 @ Tokyo
Who am I
- Kota Kanbe (Twitter, GitHub, [Facebook] (https://www.facebook.com/kota.kanbe) )
- Programmer @ Future architect, Inc. Japan
- Author of GitHub Vuls
- Owner of Mohikan Slack
Vulnerability Management on AWS
Inspector can scan only OS packages.
We need to manage vulnerabilities of programming language libraries.
Today, I talk about how to manage it automatically and the way to notify the scan report by slack or E-Mail in Japanese by using Vuls and OWASP Dependency Check.
Vuls (VULnerability Scanner)
- Vulnerability scanner for Linux/FreeBSD, agentless, written in Go
- Not for web vulnerability scanner
- GitHub Vuls
- 異常なほど詳しい日本語README
What's Vuls
Buzzed All Over The World

Got First Place In GitHub Trending
Architecture
Features (日本語)
- Scan for any vulnerabilities in Linux/FreeBSD Server
- Supports Ubuntu, Debian, CentOS, Amazon Linux, RHEL, FreeBSD
- Cloud, on-premise, Docker
- Scan middleware that are not included in OS package management
- Agentless architecture
- User is required to only setup one machine that is connected to other target servers via SSH
- Nondestructive testing
- Pre-authorization is not necessary before scanning on AWS
- Email and Slack notification are both available. (supports Japanese language)
- Scan result is viewable on accessory software, TUI Viewer terminal or Web UI (VulsRepo).
Usage: Scan vulnerabilities of non-OS packages
[servers]
[servers.172-31-4-82]
host = "172.31.4.82"
user = "ec2-user"
keyPath = "/home/username/.ssh/id_rsa"
cpeNames = [
"cpe:/a:rubyonrails:ruby_on_rails:4.2.1",
]
Sample: NVD Vulnerability Database
<entry id="CVE-2016-2098">
<vuln:vulnerable-software-list>
...
<vuln:product>cpe:/a:rubyonrails:ruby_on_rails:4.2.1</vuln:product>
...
</vuln:vulnerable-software-list>
<vuln:cve-id>CVE-2016-2098</vuln:cve-id>
<vuln:cvss>
<cvss:base_metrics>
<cvss:score>7.5</cvss:score>
<cvss:access-vector>NETWORK</cvss:access-vector>
...
</vuln:cvss>
...
<vuln:cwe id="CWE-20"/>
<vuln:summary>Action Pack in Ruby on Rails before 3.2.22.2, 4.x before 4.1.14.2, and 4.2.x before 4.2.5.2 allows remote attackers to execute arbitrary Ruby code by leveraging an application's unrestricted use of the render method.</vuln:summary>
</entry>
How to find CPE names of libraries
-
NVD: Search Common Platform Enumerations (CPE)
- It’s such a hassle
-
go-cpe-dictionary is a good choice for geeks.
- It’s a hassle
-
When you update the libraries, you also have to update the config.toml of Vuls ;)
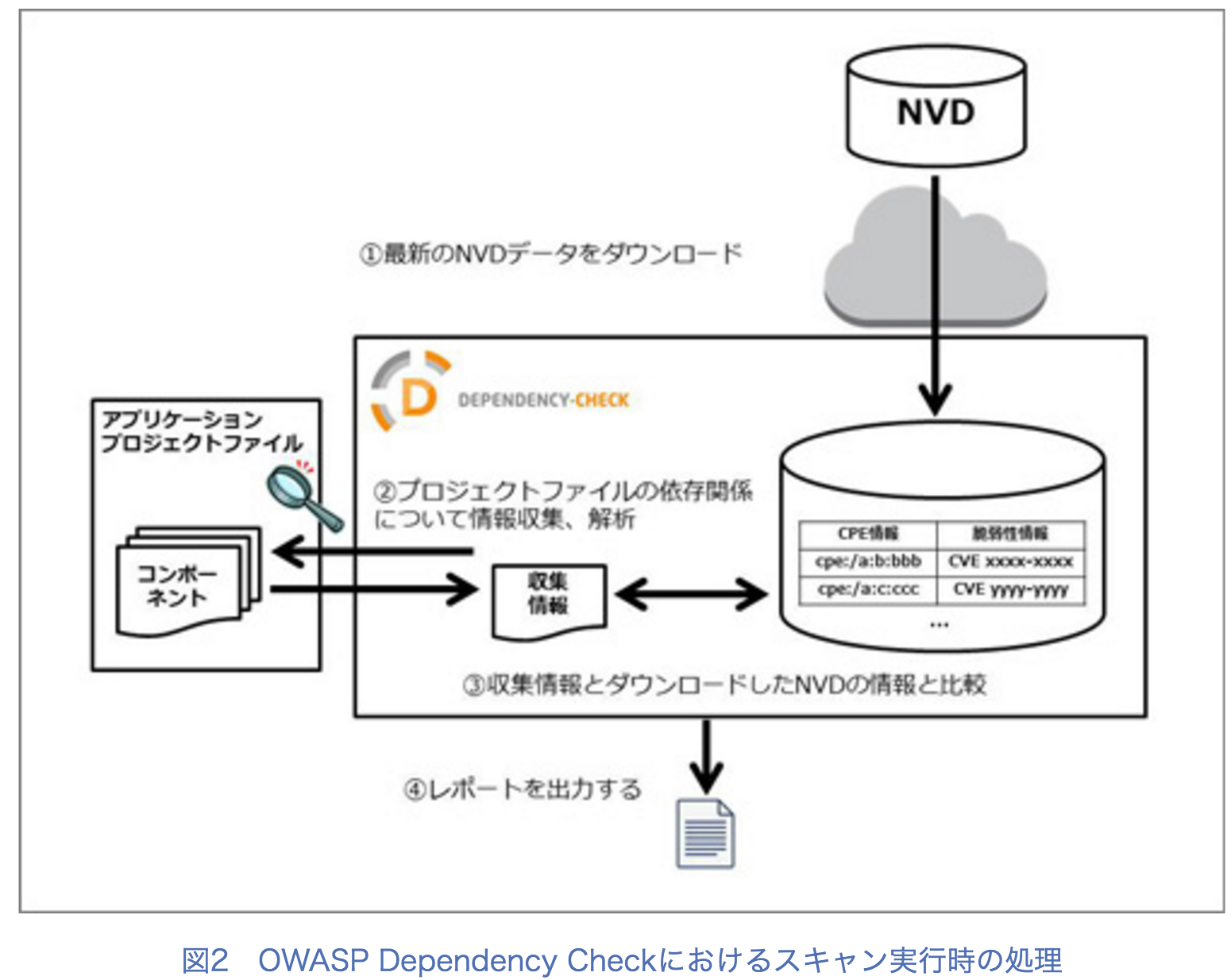
OWASP Dependency Check
- Dependency-Check is a utility that identifies project dependencies
- checks if there are any known, publicly disclosed, vulnerabilities.
- Currently Java and .NET are supported;
- additional experimental support has been added for Ruby, Node.js, Python, and limited support for C/C++ build systems (autoconf and cmake).
OWASP Dependency Check Report
Integrate with OWASP Dependency Check
- #232
- Execute OWASP Dependency Check with
--format=XMLoption. - Define the xml file path of dependency check in config.toml.
[servers.u16]
host = "127.0.0.1"
port = "22"
user = "vuls"
keyPath = "/path/to/.ssh/id_rsa"
dependencyCheckXMLPath = "/tmp/dependency-check-report.xml"
Demo
Benefit Of Integrating Vuls And OWASP Dependency Check
- Automatic Update of Vuls config when the libraries are updated.
- Reporting in Japanese
- OWASP Dependency Check supports only English
- Reporting by Email or Slack by using Vuls.
Tagging To EC2
What I'm planning to do next
Presentation (in Japan)
7/6-8 JANOG387/27 July Tech Fest 201610/5-7 Security Days Fall 201610/22 AVTokyo10/26 GREE社内勉強会- 10/28 Security-JAWS #3
- 11/22 OSSユーザのための勉強会#16 Vuls
- 12/1 Internet Week 2016
How To Catchup Vuls
- Vuls README is awesome
- VulsMatsuri #1
- 2016/9/26 about 100 people
- Slides@connpass
- Links
- Join Slack Team
We Are Hiring Hacker And Engineer!
If you are interested, please contact me ( Twitter: @kotakanbe )
Thanks
Give a GitHub Star if you are interested :)