同僚の皆が凄すぎて毎朝大体9時頃に出社するのが唯一のアイデンティティみたいな俺ですこんばんは。
EC2 AutoRecoveryの設定をterraformで実装する例です。
terraformでaws_instanceリソースを記述する時にcountを使うと
一つのリソース内で複数のEC2を起動することができるのはご存知だと思います。
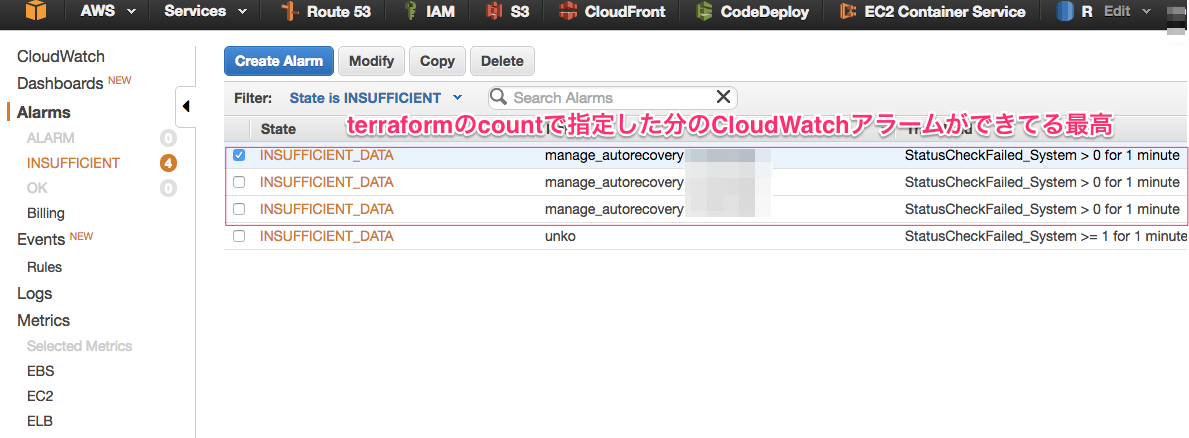
countは様々なリソースに指定できるので、aws_cloudwatch_metric_alarmリソースにも書いてみるとどうなるかという内容です。
EC2
- variables.tf
# manage Variables
variable "manage" {
default = {
name = "manage"
ami = "ami-XXXXXXXX"
instance_type = "t2.large"
iam_instance_profile = "oreno-iam-profile"
source_dest_check = true
ebs_optimized = false
root_block_device = "gp2"
root_block_device_size = 64
count = 3
}
}
- ec2.tf
elementを使うと一つのリソースをcount数分展開するようになります。
loopっぽいことができます。クソ便利です。
${element(aws_instance.manage.*.id, count.index)}
他にもaws_eipリソースでcount起動したaws_instance全てにEIPを当てるのにも使ったりします。
# Launch Manage Server
resource "aws_instance" "manage" {
ami = "${lookup(var.manage, "ami")}"
instance_type = "${lookup(var.manage,"instance_type")}"
key_name = "mykey-${var.region}"
iam_instance_profile = "${lookup(var.manage,"iam_instance_profile")}"
source_dest_check = "${lookup(var.manage, "source_dest_check")}"
ebs_optimized = "${lookup(var.manage, "ebs_optimized")}"
vpc_security_group_ids = ["${aws_security_group.manage.id}"]
subnet_id = "${aws_subnet.prd-public-1c-subnet.id}"
root_block_device {
volume_type = "${lookup(var.manage,"root_block_device")}"
volume_size = "${lookup(var.manage,"root_block_device_size")}"
}
count = "${lookup(var.manage, "count")}"
tags {
Name = "manage${count.index + 1}"
Role = "manager"
Environment = "prd"
Service = "orenosaikounoservice"
}
}
# CloudWatch Alarm EC2 AutoRecovery
resource "aws_cloudwatch_metric_alarm" "manage" {
alarm_name = "manage_autorecovery ${element(aws_instance.manage.*.id, count.index)}"
comparison_operator = "GreaterThanThreshold"
evaluation_periods = "1"
metric_name = "StatusCheckFailed_System"
namespace = "AWS/EC2"
period = "60"
statistic = "Minimum"
threshold = "0"
alarm_actions = [ "arn:aws:automate:${var.region}:ec2:recover" ]
count = "${lookup(var.manage, "count")}"
dimensions = {
Name = "InstanceId"
Value = "${element(aws_instance.manage.*.id, count.index)}"
}
depends_on = ["aws_instance.manage"]
}
apply
$ terraform apply
・・省略・・
aws_cloudwatch_metric_alarm.manage.1: Creating...
actions_enabled: "" => "true"
alarm_actions.#: "" => "1"
alarm_actions.1593769270: "" => "arn:aws:automate:ap-northeast-1:ec2:recover"
alarm_name: "" => "manage_autorecovery XXXXXXXXXXXXXXXXX"
comparison_operator: "" => "GreaterThanThreshold"
dimensions.#: "" => "2"
dimensions.Name: "" => "InstanceId"
dimensions.Value: "" => "i-XXXXXXXXXXXXXXXXX"
evaluation_periods: "" => "1"
metric_name: "" => "StatusCheckFailed_System"
namespace: "" => "AWS/EC2"
period: "" => "60"
statistic: "" => "Minimum"
threshold: "" => "0"
aws_cloudwatch_metric_alarm.manage.1: Creation complete
aws_cloudwatch_metric_alarm.manage.0: Creation complete
aws_cloudwatch_metric_alarm.manage.2: Creation complete