概要
自宅からAWSへSRXを使用してVPNで接続をする。
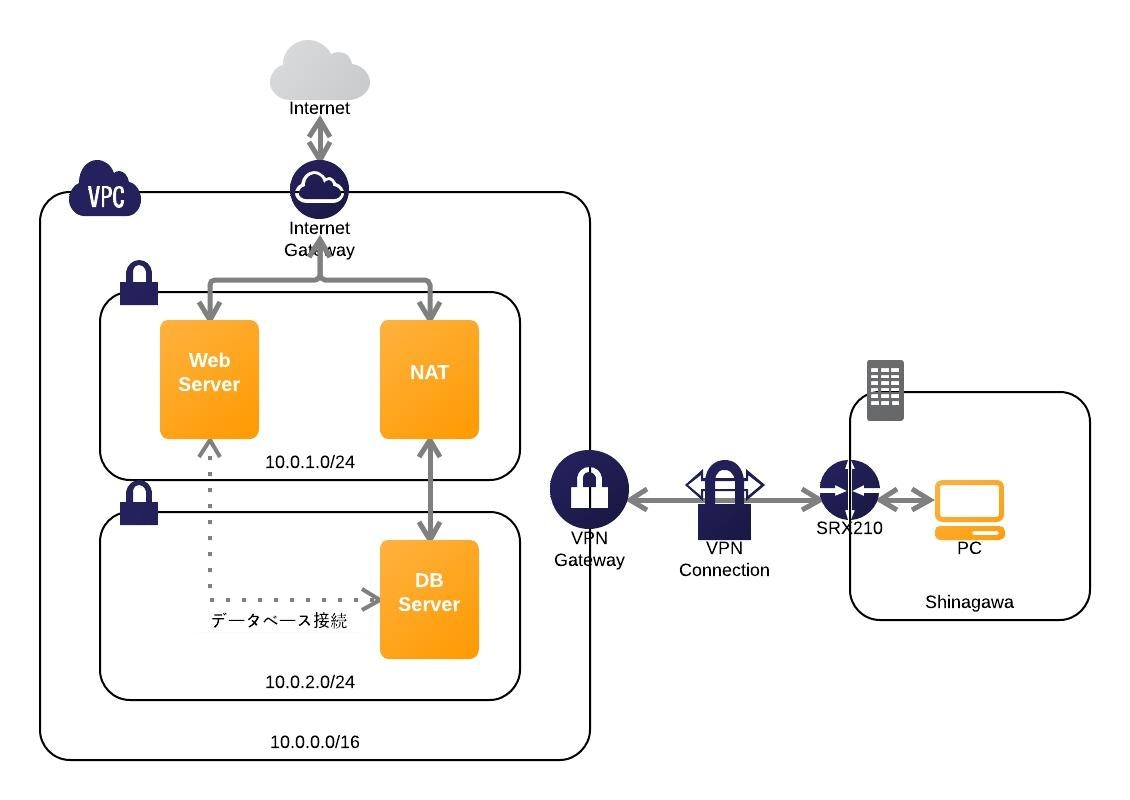
AWS構成
品川からAWSへ接続する。
VPC設定
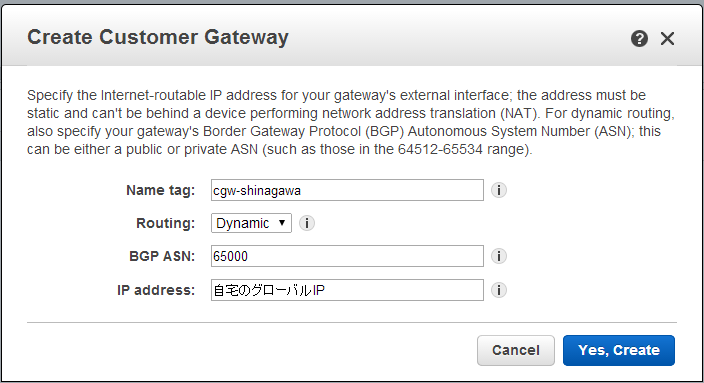
Customer Gateways
VPC DashboardからCustomer Gatewaysを選択。
BGPにて経路交換を行うため、Dynamic設定をする。
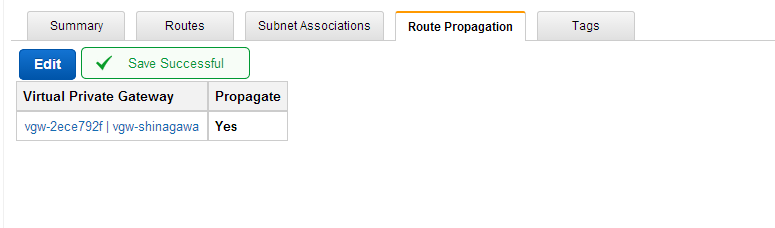
Virtual Private Gateways
ipsecを使用するため、Virtual Private Gatewaysを選択。
作成するだけ。
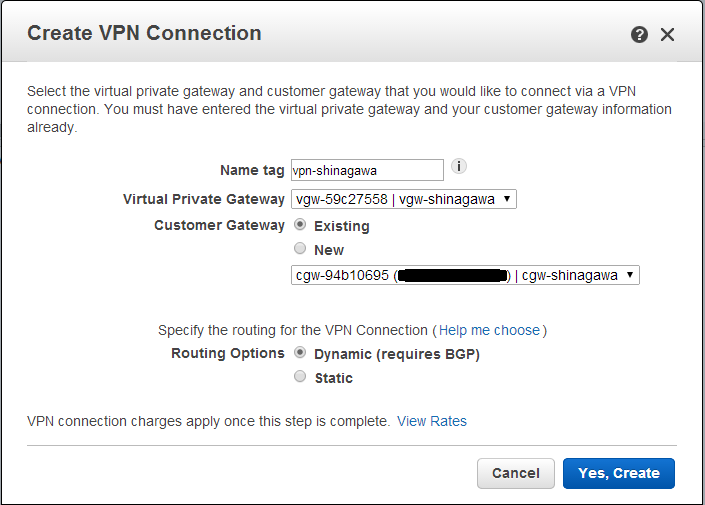
VPN Connections
VPNを作成するためにVPN Connectionsを選択。
先ほど作成した、「VPN Connections」、「VPN Connections」を関連付けする。
また、BGPにて接続するためDynamicとする。
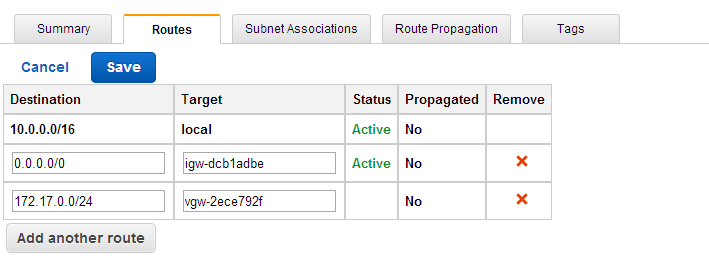
Route
作成したGWへのルートを追加
SRX設定
設定する元Configは、こちら
VPN ConnectionsのDownload Configurationから設定をダウンロードする。
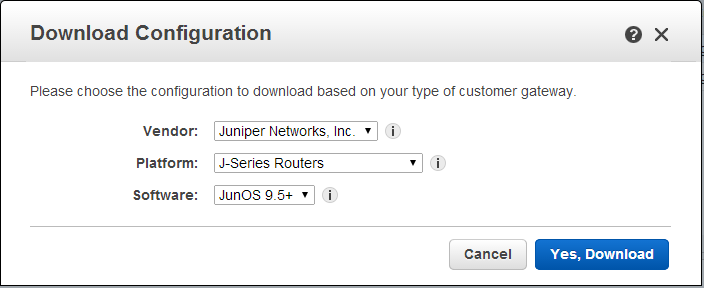
後は設定をそのまま追加すればいいかと思いきや、一手間必要。
- デフォルトルートを広告してしまうため、該当のルートのみに変更
## 削除
set policy-options policy-statement EXPORT-DEFAULT term default from route-filter 0.0.0.0/0 exact
## 追加
set policy-options policy-statement EXPORT-DEFAULT term default from route-filter 172.17.0.0/24 exact
- pp0.0にてピア接続するために変更
## 削除
set security ike gateway gw-vpn-81b50280-1 external-interface ge-0/0/0.0
set security ike gateway gw-vpn-81b50280-2 external-interface ge-0/0/0.0
## 追加
set security ike gateway gw-vpn-81b50280-1 external-interface pp0.0
set security ike gateway gw-vpn-81b50280-2 external-interface pp0.0
- ファイアウォール
ルータの設定やセキュリティポリシーによって変更する必要がある
set security policies from-zone trust to-zone vpn policy trust-to-vpn match source-address any
set security policies from-zone trust to-zone vpn policy trust-to-vpn match destination-address any
set security policies from-zone trust to-zone vpn policy trust-to-vpn match application any
set security policies from-zone trust to-zone vpn policy trust-to-vpn then permit
set security policies from-zone vpn to-zone trust policy trust-to-vpn match source-address any
set security policies from-zone vpn to-zone trust policy trust-to-vpn match destination-address any
set security policies from-zone vpn to-zone trust policy trust-to-vpn match application any
set security policies from-zone vpn to-zone trust policy trust-to-vpn then permit
set security policies from-zone vpn to-zone vpn policy trust-to-vpn match source-address any
set security policies from-zone vpn to-zone vpn policy trust-to-vpn match destination-address any
set security policies from-zone vpn to-zone vpn policy trust-to-vpn match application any
set security policies from-zone vpn to-zone vpn policy trust-to-vpn then permit
set security zones security-zone vpn interfaces st0.1
set security zones security-zone vpn interfaces st0.2
delete security zones security-zone trust interfaces st0.1
delete security zones security-zone trust interfaces st0.2
通信確認
- IKE Status確認
root> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 3843154 UP 53d3ff37802470d3 86e611a696ac37bf Main xxx.xxx.xxx.xxx 3843153 UP 85dc9face9e23f63 4cbb9957c5ee31f5 Main xxx.xxx.xxx.xxx
- IPsec 確認
root> show security ipsec security-associations Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon vsys Port Gateway /<131073 ESP:aes-128/sha1 c546e29c 3445/ unlim - root 500 xxx.xxx.xxx.xxx />131073 ESP:aes-128/sha1 90bce219 3445/ unlim - root 500 xxx.xxx.xxx.xxx /<131074 ESP:aes-128/sha1 ad9f05f7 3450/ unlim - root 500 xxx.xxx.xxx.xxx />131074 ESP:aes-128/sha1 9c37647f 3450/ unlim - root 500 xxx.xxx.xxx.xxx
- BGPピア確認
root> show bgp summary Groups: 1 Peers: 2 Down peers: 0 Table Tot Paths Act Paths Suppressed History Damp State Pending inet.0 0 0 0 0 0 0 Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped... xxx.xxx.xxx.xxx 10124 31 35 0 0 4:42 0/0/0/0 0/0/0/0 xxx.xxx.xxx.xxx 10124 32 34 0 0 4:38 0/0/0/0 0/0/0/0
- BGP受信経路確認
`root> show route protocol bgp
inet.0: 10 destinations, 11 routes (10 active, 0 holddown, 0 hidden)
- = Active Route, - = Last Active, * = Both
10.0.0.0/16 *[BGP/170] 00:03:30, localpref 100
AS path: 10124 I
> to 169.254.252.5 via st0.2
[BGP/170] 00:03:30, localpref 100
AS path: 10124 I
> to 169.254.252.1 via st0.1
`
- BGP送信経路確認(ピア毎に確認)
`root> show route advertising-protocol bgp xxx.xxx.xxx.xxx
inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden)
Prefix Nexthop MED Lclpref AS path
-
172.17.0.0/24 Self I
` -
Ping
[ec2-user@ip-10-0-1-10 ~]$ ping 172.17.0.11 PING 172.17.0.11 (172.17.0.11) 56(84) bytes of data. 64 bytes from 172.17.0.11: icmp_seq=1 ttl=126 time=8.14 ms 64 bytes from 172.17.0.11: icmp_seq=2 ttl=126 time=7.81 ms 64 bytes from 172.17.0.11: icmp_seq=3 ttl=126 time=11.3 ms
etc...
BGPピア、VPNは簡単に接続できるが、ファイアーウォールの設定は環境によって変更する必要がある。
また、1日接続しているだけで1ドル程度かかるため、
個人的に使用する場合は必要な時だけにする。